COVID-19 Heroes
Dell Technologies takes a holistic, risk-based approach to build resilience
At Dell Technologies, collaboration across the security function has been a pillar to crisis response during the COVID-19 pandemic.

Image courtesy of Dell Technologies
With data and team members’ health and safety top of mind, Dell Technologies, one of the world’s leading technology companies helping to transform the digital landscape and providing organizations with secure and agile IT solutions, made the decision on March 15, 2020, to close office sites and move 90% of its team members to remote work over the course of one weekend.
According to Tim Rigg, Vice President of Global Security Operations for Dell Technologies Security and Resiliency Organization (SRO), the company’s long-standing history of flexible work and its risk assessment tool made the immediate shift to a work-from-home model an easy task.
The company’s approach to flexible work allows team members to choose the work style that best fulfills their needs on the job and in their personal lives. “We believe work is not tied to where and when you work, but what you do — and it is core to our culture now. Before March 2020, 65% of our team members leveraged work flexibility on an occasional basis, and 30% of team members were working remotely on any given day,” Rigg says.
Having an underlying infrastructure, such as systems, technologies, tools and leadership support for flexible work, as well as a risk assessment tool already in place, made the transition seamless. “The flexibility we’ve created has helped team members find work-life balance while maintaining productivity and a commitment to innovation,” he explains.
The switch to remote access and secure remote connections were vital to business continuity and organizational resilience. This flexibility enabled the organization to continue providing a competitive advantage to its users and created new value by launching nine different products in nine weeks in the first few months of the pandemic.

Tim Rigg, Vice President of Global Security Operations, Dell Technologies Security and Resiliency Organization. Image courtesy of Rigg
To continue to operate without disruption, Rigg and the Global Security Operations team leveraged the company’s initial risk assessment tool — a holistic and multifaceted approach to protecting the company’s physical assets, inventory, information, intellectual property and people. The tool determines potential impacts resulting from the interruption of time-sensitive or critical business processes. Originally, the tool was built to align with the health and safety of employees and assess travel risk management and duty of care across the shifting landscape.
Rigg explains, “At the onset of the pandemic, the risk assessment helped us be proactive regarding business disruption and pivot our performance based on what the tool indicated. We shut down travel by country, region and globe to help ensure that our employees were as safe as possible in their current environment. We were able to not only make emergency arrangements for some employees, but even help other team members who were on personal travel to return safely home.”
After making the switch to remote work, Dell Technologies’ leadership — in coordination with Global HR, Real Estate and Facilities, the SRO team and others — knew the organization needed to transform its original risk assessment tool to guide further decisions on how to reopen Dell Technologies’ sites while keeping team members and communities healthy.
“As the virus started spreading more widely, crossing boundaries and oceans, we continued to build out the tool, adding more data and variables, to enable a consistent approach to make decisions,” Rigg explains. “Thus, the Inversed Risk Matrix.”
The Inversed Risk Matrix helped make sense of all the health data about COVID-19 — the number of infections, hospitalizations, recoveries, curve inclination, etc. — to make informed, data-based decisions that responsibly guided return-to-site strategy, putting the health and safety of the organization’s team members and communities first. The matrix collected data from three credible public sources: Johns Hopkins, the Centers for Disease Control (CDC) and the World Health Organization.
In addition, the matrix used a total of 15 different variables, all weighed appropriately, to calculate the overall risk score across 182 countries and 173 provinces or states where the company operates. “Not only did this tool help us reopen Dell sites safely in certain locations, but it also helped us remain onsite safely and make other decisions about travel, events, etc.,” Rigg notes.
The SRO team also leveraged a return-to-site strategy to help inform decision-making beyond reopening a particular site, in which the data and analysis that goes into the model are scalable to local conditions at the city, state and country levels. Rigg explains, “Previously, we had a three-part, phased approach to returning to each site, considering each facility’s capacity, local government regulations and our own data science and risk model (among other factors) to determine safety and readiness to reopen and remain on site. The strategy also prioritized team members’ roles that needed to be onsite.”
As the virus and situations globally, regionally and locally evolved, so did the company’s response and risk-related tools. “On June 29, 2021, we launched the new COVID-19 Risk Reference tool. This tool assesses the risk levels of an area based on COVID-19 cases, deaths and the percentage of people vaccinated in that area. The tool allows us to continue our globally consistent, data-driven approach to how we reopen Dell sites, all with our team members’ and communities’ health top of mind.”
Having met the challenges posed by the pandemic, Dell Technologies also recently announced to team members that the company will reopen sites not already open to team members, contractors and guests on January 4, 2022.
In the early pandemic stages when business leaders were looking to their peers for help and examples of minimizing business disruption and protecting employees, it was hard to synthesize the data and then determine which data was appropriate for informing business decisions, Rigg explains. However, all tools created by the Global Security Operations team did just that for Dell, assisting with:
- Daily situation reporting to executive leadership and other risk decision-makers and management during 800+ COVID-19-related meetings;
- Leadership and coordination of corporate, regional and country-level crisis management teams to assess critical needs and decisions across the business, team members and users;
- Travel and evacuations for team members and their stranded families due to flight cancellations or quickly developing quarantine requirements;
- Delivery of technologies to users and companies in need across various industries, such as healthcare, financial, education, government, etc.
Rigg says, “Dell’s first priority is the safety and health of our team members and the communities where we live and work. Although we never stopped working thanks to our culture of flexible work, the tools we created allowed us to take a conservative, globally consistent, data-driven approach to how we brought select team members back to the site.”
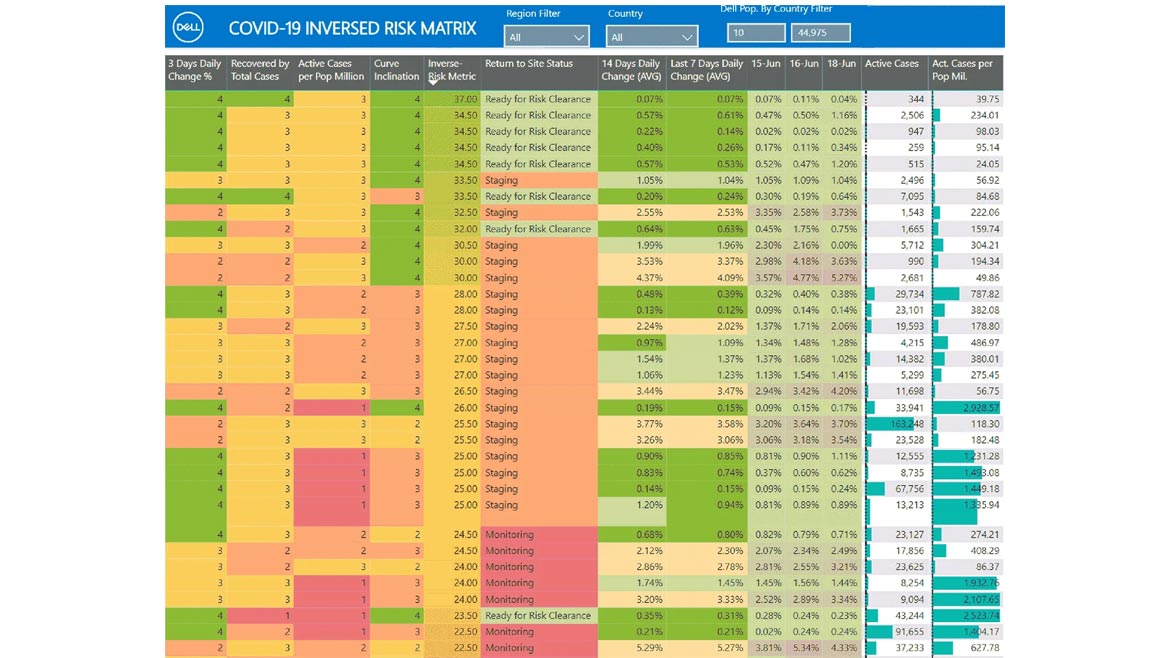
The Inversed Risk Matrix — a real-time dashboard that is continuously enhanced with predictive capabilities to gain more insights to guide business and decision-making — helped Dell Technologies leadership make sense of data about the COVID-19 virus. Image courtesy of Dell Technologies
On numerous occasions, the Global Security Operations and SRO teams also shared insights and resources via the Security Executive Council (SEC)’s COVID-19 security-related industry briefing sessions to a broad range of security professionals. In addition, both teams allowed the SEC to share unattributed output from the Inversed Risk Matrix with more than 700 companies, government agencies, universities, NGOs, research organizations, institutes and individual practitioners responsible for response to COVID-19 input around the world. Through this effort, the tool became the backbone of numerous COVID-19 pandemic response programs globally.
At Dell Technologies, collaboration across the security function, the chief security officer, environment, health and safety, human resources, real estate and facilities, and communications team has been a pillar to crisis response during the COVID-19 pandemic. Breaking down silos, all teams met regularly and used the tools developed to help make globally consistent, informed decisions about the health and safety of its team members and communities to emerge stronger through the disruption and to foster a culture of resilience.
“First and foremost, it has been the resilient nature of our team members and our unwavering commitment to health and safety of our team members and the communities where we live and work,” Rigg says. “Some of our best and brightest minds have worked on our return to site strategy since the beginning — the effort is truly collaborative and cross-functional. Our flexible workplace and the ability of executive leadership to make swift yet consistent decisions based on science and data are key contributors to our response efforts.”
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








