How artificial intelligence can transform event venue security operations

It has become an essential function for security teams to protect the public by preventing weapons and other prohibited items from being brought into the spaces where people gather for entertainment, learning, worship, and more. Security measures in places such as stadiums, outdoor venues, schools, religious facilities, convention centers, corporate campuses, and government buildings need to be efficient to safely process large volumes of people. Further, there is a growing need for contactless security in the wake of the COVID-19 pandemic that will allow physical distancing while also respecting the privacy of individuals to improve the security experience.
Traditional methods of screening such as walk-through and handheld metal detectors have been in use for decades, and while historically, they have been effective for the detection of metal weapons, they are also very prone to high false alarm rates. Additionally, they are not particularly efficient, with limited throughput and the need for patrons to remove certain clothing such as belts or to empty items from their pockets such as keys and cell phones. And even with these steps, it is often necessary to include secondary screening measures such as pat downs.
For event operators, this process can negatively impact the experience of the guests by causing delays, hassle, and unnecessary secondary screening, which can also impact the business’s bottom line by decreasing the time that the guests have to enjoy the venue’s potential food, drink and merchandise offerings. New technology is forthcoming that will enhance detection and security providing a more positive experience for guests and operators.
Improving the Efficacy and the Efficiency of Screening with Artificial Intelligence
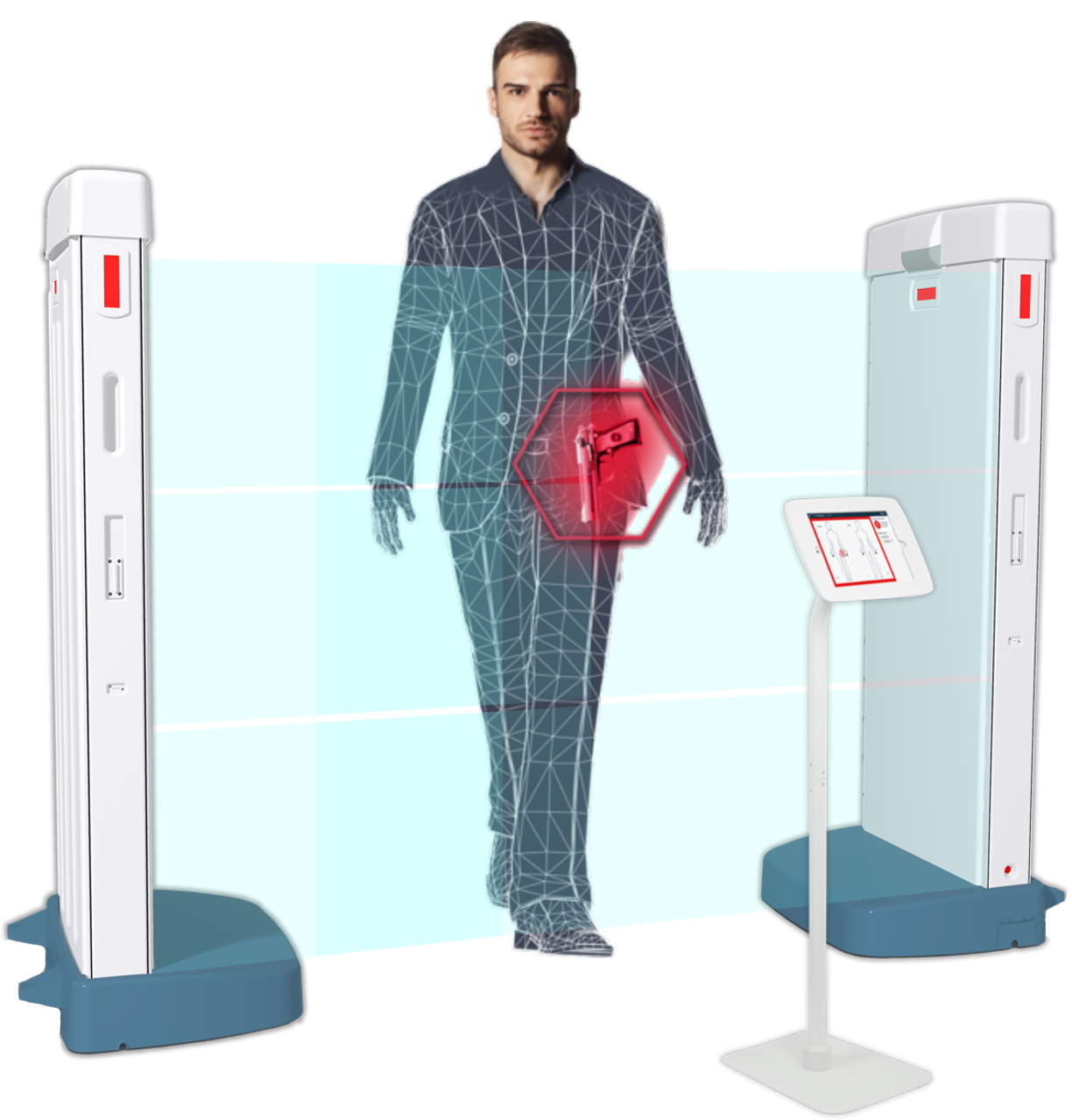
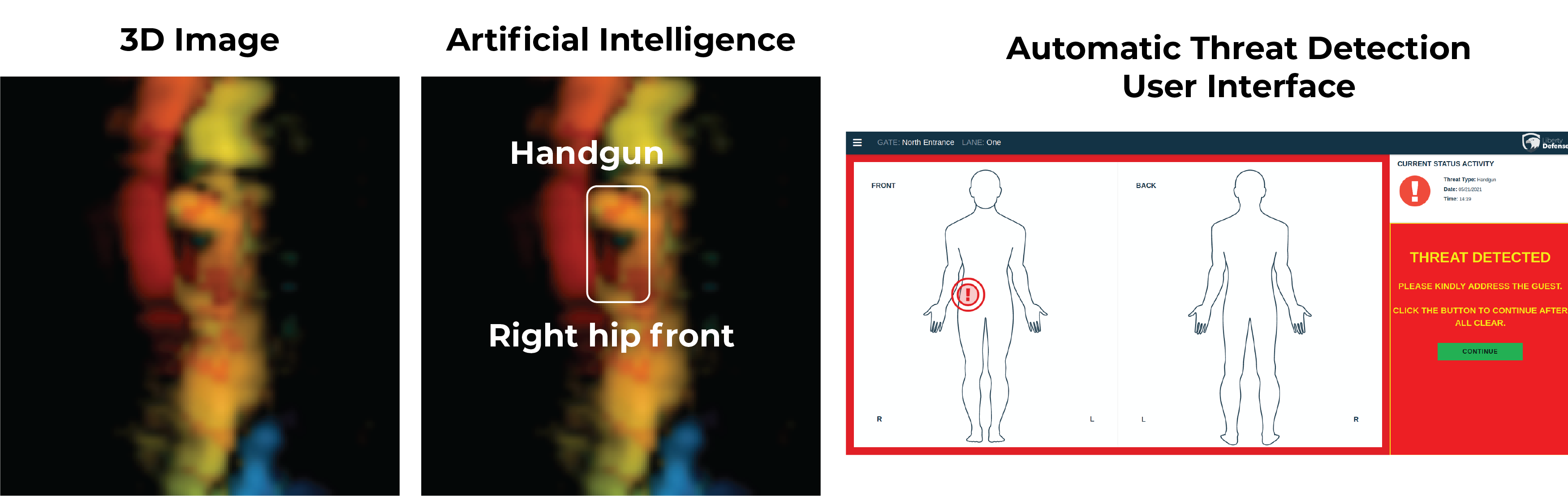
Technology advancements for data, artificial intelligence (AI), and computing provide an opportunity for security teams to make screening both more effective and efficient. This is done by using AI and deep learning algorithms, combined with large volumes of data acquired through three-dimensional (3D) imaging, along with advanced computing power, to improve the detection of concealed weapons.
3D images can be acquired using technologies such as low-power radar that bounces off a person’s body as the person walks past sensors at a security checkpoint. This means that is it possible to have patrons move through security more quickly, with less contact, fewer pat downs, and lower false alarm rates.
Example 1
Example 2

Example 3
The deep learning technology used for this is also used in many other real-life applications such as speech recognition, object recognition, sentiment analysis, and autonomous driving. The neural networks it uses are inspired by biology and how the human brain works, recognizing complex patterns within unstructured data. This is why deep learning is capable of detecting concealed firearms, IEDs, explosives, and other prohibited objects.
Contactless Security
Artificial intelligence can also provide another benefit that in the wake of the pandemic has become incredibly relevant. The COVID-19 pandemic provided the event industry with an opportunity to pause and re-evaluate what aspects of security could be made stronger, more efficient, and more comfortable for guests.
AI, when deployed as described in this article using 3D-imaging technology, can create a completely distant, contactless, and seamless experience for guests. The means that venues can be filled more quickly so that guests will spend more time being excited about their event and spend less time bogged down with security procedures.
Privacy
Another benefit to using AI in security operations is that it can also help guests maintain their sense of privacy. They are not required to empty their purses or pockets, are not being patted down by personnel, are not removing belts or jewelry, and they are not being asked about what metal they may have on or in their bodies. And because the 3D images used by the AI are used only by the AI, as opposed to by humans, this further protects the privacy of guests, because no personally identifiable information is captured or stored, and no images of their bodies are seen or stored.
How It Works
To prepare deep learning applications to detect weapons or other prohibited items, a structured and iterative process of training deep learning models is required to ensure that the quality of the data is high.
Deep Learning is a data-intensive task. Having a large volume of data, and in this case, 3D image data is a key success factor in order to train neural networks to achieve a high level of accuracy in their predictions. However, this alone is not sufficient. A large volume of high-quality annotated data is also required, and so the data must go through pre-processing, labeling, and a quality audit process. Any errors in pre-processing and labeling will lead to lower performance such as higher false alarm rates. To train computers using data and artificial intelligence, the data needs to represent real-world scenarios such as different body types, obscurants, weapons (class, shape, sizes, materials, etc.), and security operations. This is achieved by obtaining high-quality data sets and ensuring that all data that is used by the AI provides the necessary information for detection through the use of 3D imaging technology.
Looking Forward
With newer technologies providing rich data, advancements in deep learning in computer vision applications and exponential gains in computing power, artificial intelligence is making a difference in screening patrons for dangerous or prohibited items and delivering a significantly improved experience and result.
Against the backdrop of the pandemic, the need for minimizing contact between patrons and screeners will accelerate the use of AI technologies. Using AI, the screening process at event facilities could involve little or no touching, little or no need to remove jackets, empty pockets, and purses, and often no need for patrons to even stop walking – allowing for higher throughput without comprising safety, and an overall more positive experience for guests and staff.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!