Analyzing the EDPB’s draft recommendations on supplementary measures
In the wake of Schrems II, the EDPB’s much-anticipated recommendations provide extensive guidance on supplementary measures parties can use to legally transfer data out of the EEA in the absence of an adequacy decision.

In a flurry of activity last week, the European Data Protection Board (EDPB) and the European Commission made major announcements affecting cross-border data transfers out of the EEA.
First, the EDPB announced the adoption of draft recommendations on measures that supplement cross-border data transfer tools as well as recommendations on the European Essential Guarantees for surveillance measures. The recommendations were adopted during the EDPB’s 41st plenary session and in response to the CJEU’s Schrems II ruling. The following day, the European Commission published a draft set of new standard contractual clauses. Taken together, these documents will, once finalized, fundamentally change data transfers out of the EEA.
The below post will examine the EDPB’s draft recommendations on supplementary measures. The draft new standard contractual clauses will be discussed in a separate post.
The EDPB’s recommendations as to supplementary measures provide guidance to businesses for how to legally transfer data out of the EEA in the wake of Schrems II. The draft recommendations are open for public comment until November 30, 2020.
The recommendations outline the following six-step “roadmap” for companies to follow when analyzing whether a data exporter needs to utilize supplementary measures for the transfer of personal data out of the EEA:
- Know your transfers
- Verify the transfer tool you are relying on
- Assess the laws of the third country
- Identify and adopt supplementary measures
- Take any formal procedural steps that the adoption of supplementary measures may require
- Re-evaluate your analysis at appropriate intervals
The EDPB also published the following infographic explaining its roadmaps:
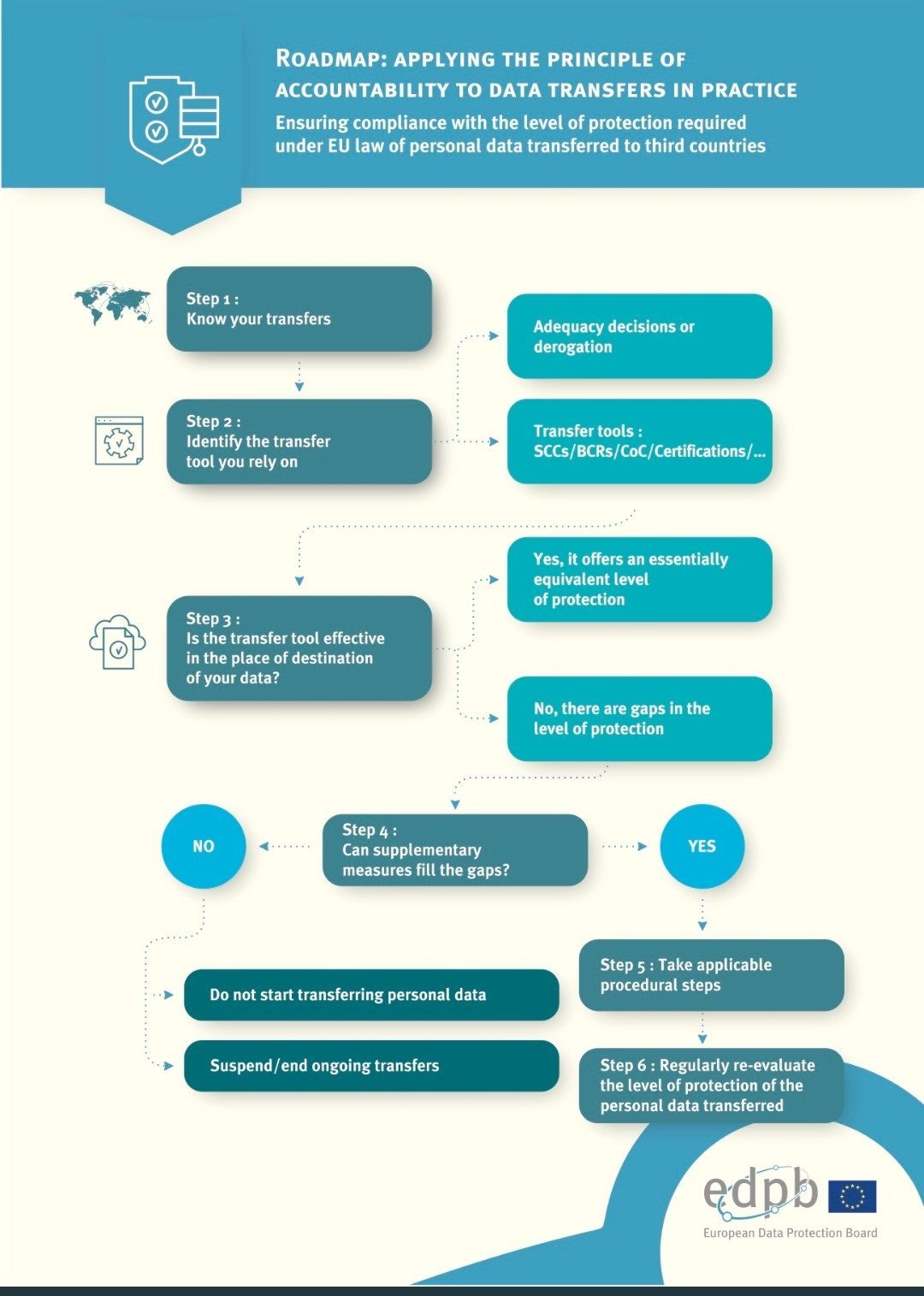
These steps are discussed in further detail below.
Step 1 – Know Your Transfers
This step is self-explanatory – data exporters need to identify and document personal data transfers out of the EEA. The EDPB emphasizes that data exporters must consider not only the initial transfer but also any onward transfers such as transfers to sub-processors. Data exporters also must adhere to the principle of data minimization.
Of particular note, the EDPB states that “remote access from a third country (for example in support situations) and/or storage in a cloud situated outside the EEA, is also considered to be a transfer.” The fact that remote access from a third country is considered to be a transfer is not particularly surprising in light of prior EDPB guidance; however, it does impact companies who have looked to EEA data localization as a Schrems II solution but still need to remotely access the personal data from a non-adequate country.
Step 2 – Verify the Transfer Tool You are Relying On
Transfers undertaken pursuant to an adequacy decision do not require further analysis, but entities relying on an adequacy decision should continue to monitor any changes in those decisions. Data exporters in countries without adequacy decisions (e.g., the United States) need to identify an Article 46 transfer mechanism (e.g., standard contractual clauses or binding corporate rules). Data exporters can rely on Article 49 derogations (e.g., express consent) but such derogations “must be interpreted restrictively and mainly relate to processing activities that are occasional and non-repetitive.”
Step 3 – Assess the Laws of the Third Country
The use of an Article 46 transfer mechanism may not be enough if the laws of the third country in which the data is received interfere with the level of protection guaranteed by GDPR. Indeed, this was a central holding of Schrems II.
Therefore, data exporters must assess whether the laws of the third country “may impinge on the effectiveness of the appropriate safeguards of the Article 46 GDPR transfer tool [they] are relying on, in the context of [their] specific transfer.” Data importers, where appropriate, should provide data exporters with the relevant information relating to the third country in which the importer is established.
If the laws allowing for government access to personal data in the third country “are limited to what is necessary and proportionate in a democratic society,” the commitments contained in the Article 46 transfer tool may be sufficient. The EDPB’s accompanying European Essential Guarantees recommendations should be utilized for this determination. Conversely, if the data exporter determines that the third country’s laws do not ensure an essentially equivalent level of protection, the data exporter must “put in place effective supplementary measures or [] not transfer personal data.”
It is worth keeping in mind that the European Commission has only recognized a handful of non-EEA countries as having an adequate level of data protection. Therefore, although Schrems II involved data transfers to the United States, the fallout of that decision implicates any country where adequacy has not been found. Entities should carefully consider all of countries that may be implicated based on their business model, keeping in mind that remote access to data constitutes a transfer. Of course, we also are still waiting to see whether the United Kingdom will be given an adequacy decision before the end of the Brexit transition period.
With respect to transfers to the United States, if a data importer or any entity the importer may transfer the data to is subject to FISA 702, “SCCs or other Article 46 GDPR transfer tools may only be relied upon for such transfer if additional supplementary technical measures make access to the data transferred impossible or ineffective.”
The EDPB’s clarification that data importers subject to FISA 702 can still receive EEA personal data (albeit with appropriate technical measures) is significant. In the wake of Schrems II, Max Schrems took the position that transfers to entities subject to FISA 702 must stop. However, the EDPB was not willing to go that far. Still, it is clear that determining whether a US data importer is subject to FISA 702 will be an essential part of any analysis.
Step4 – Adopt Supplementary Measures
To be sure, the crux of the EDPB’s recommendations is its extensive discussion of supplementary measures.
As a threshold matter, entities are required to assess on a case-by-case basis the appropriate supplementary measures for the transfer, which may be a combination of contractual, technical or organizational measures. However, “[c]ontractual and organisational measures alone will generally not overcome access to personal data by public authorities of the third country,” and “there will be situations where only technical measures might impede or render ineffective access by public authorities in third countries to personal data, in particular for surveillance purposes.” Nonetheless, combining measures can “strengthen the overall level of data protection.”
When analyzing supplementary measures, the parties should examine, among other things, the format of the data to be transferred (i.e., plain text/pseudonymized or encrypted), the nature of the data, the length and complexity of the data, and the possibility that the data could be subject to onward transfer.
The bulk of the guidance on supplementary measures is found in Annex 2 of the recommendations, which spans 17 pages and includes an extensive discussion of the contours for utilizing technical, contractual and organizational measures. Any entity engaging in covered transfers will need to conduct a thorough review of those 17 pages to determine the measures it must utilize. Below is a summary of the EDPB’s discussion.
Technical Measures
The discussion of technical measures is accomplished through seven use cases.
Use Case 1 considers the technical measures for when a “data exporter uses a hosting service provider in a third country to store personal data,” that does not require access to data in the clear (i.e., unencrypted). There, among other factors, encryption should be state-of-the-art, “flawlessly implemented”, and the keys should be reliably managed and retained “solely under the control of the data exporter” or with entities in a third country where an adequacy decision has been issued. The EDPB’s concern with the location of the encryption keys, at least for US data transfers, is that data importers subject to FISA 702 may be required to turn over the keys to government authorities.
In Use Case 2, the EDPB recognizes that the use of pseudonymized data can be an effective supplementary measure. In that use case, the data exporter first pseudonymizes the personal data before transferring it to a third country. This measure is acceptable if, among other things, the personal data can no longer be linked to the data subject consistent with Article 4(5); the additional information necessary to identify the individual is kept by the data exporter in a Member State or adequate jurisdiction; and technical and organizational safeguards are implemented to keep the additional information secret.
The other uses cases considered by the EDPB are:
- Use Case 3 – Encrypted data merely transiting third country
- Use Case 4 – Protected recipient
- Use Case 5 – Split or multi-party processing
Finally, the EDPB identifies two use cases in which it has found no effective supplementary measures.
The first use case is when a data exporter uses a cloud service provider or other processor to process personal data in a third country, the processor needs to access the data in the clear (i.e., unencrypted), and the power granted to public authorities in the recipient country goes beyond what is necessary and proportionate in a democratic society. In this case, “where unencrypted personal data is technically necessary for the provision of the service by the processor, transport encryption and data-at-rest encryption even taken together, do not constitute a supplementary measure that ensures an essentially equivalent level of protection if the data importer is in possession of the cryptographic keys.” Of course, this use case implicates many types of everyday data transfers and the EDBP’s position will require close scrutiny from such entities.
The second use case is when a data exporter makes personal data available to entities in a third country to be used for shared business purposes, e.g., when personal data is shared in a large multi-national corporation. Supplementary measures cannot be used if the data is transferred in a way that the importer has direct access to the data of its own choice or the data is transferred through a communication service, the importer uses the data in the clear for its own purposes, and the power granted to public authorities in the recipient country goes beyond what is necessary and proportionate in a democratic society.
Contractual Measures
Some of the contractual measures discussed by the EDPB are:
- Technical Measures – Requiring the technical measures discussed above to be used for the transfer
- Transparency – Including transparency disclosures such as information on any access requests the data importer has received from government entities over a given period of time
- No Back Doors – Making representations that the data importer has not “purposefully created back doors” that could be used to access personal data
- Audit Rights – Reiterating the data exporter’s right to conduct audits
- “Warrant Canary” – Requiring the data importer to commit to regularly publish (e.g., at least every 24 hours) “a cryptographically signed message informing the exporter that as of a certain date and time it has received no order to disclose personal data or the like. The absence of an update of this notification will indicate to the exporter that the importer may have received an order.”
- Duty to Challenge Requests – Requiring the data importer to challenge any government access request, if possible
- Data Subject Authorization – Providing that personal data transmitted in plain text in the normal course of the business may only be accessed by government authorities with the express or implied consent of the data exporter and/or data subject
- Notice to Data Subjects – Obligating the data importer and/or exporter to notify data subjects of the access request to allow them to seek appropriate redress
- Assisting Data Subject – Requiring the parties to assist data subjects in exercising their rights in the third country
Organizational Measures
Organizational measures are internal policies, organizational methods, and standards that controllers and processors could apply to themselves and on data importers.
The measures can include:
- Adoption of policies for the transfer of personal data within groups of entities
- Disclosure to data exporters of information regarding government access requests
- Regular publication of transparency reports
- Use of data minimization
- Implementing a procedure for timely involving the data protection officer, if applicable
- Adoption of data security and data privacy policies (e.g., ISO certification)
Step 5 – Take any formal procedural steps that the adoption of supplementary measures may require
The EDPB notes that the use of supplementary measures must be considered in the context of the chosen Article 46 transfer mechanism. For example, for entities using the SCCs, any additional contractual clauses relating to supplementary measures should not conflict with the SCCs.
Step 6 – Re-evaluate your analysis at appropriate intervals
Entities are required to continually monitor the information identified above and adjust as may be necessary.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







