Do I need to be HIPAA compliant? Uncovering the “I didn’t know” claim

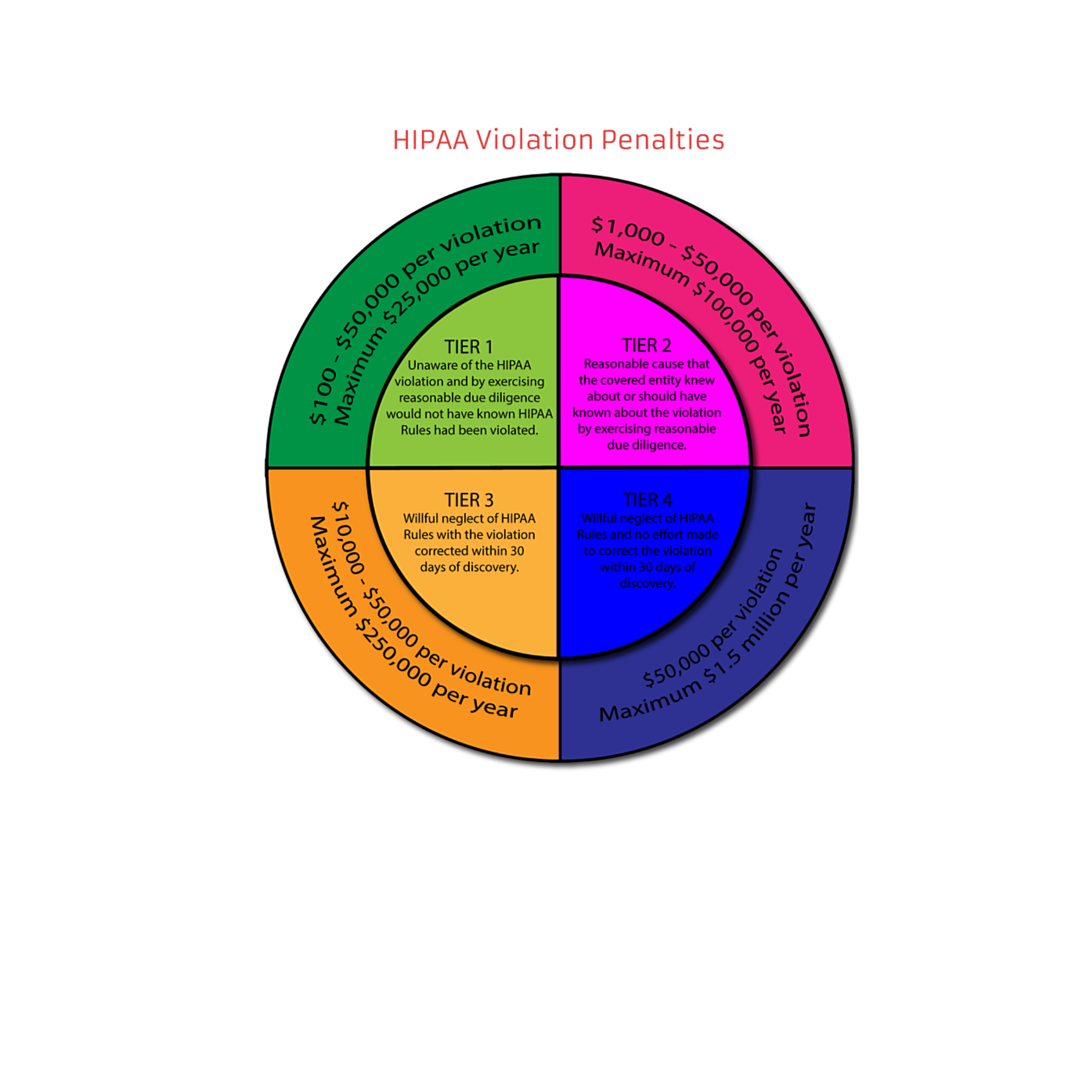
So let’s take a moment to review the most fundamental “I didn’t know” HIPAA issue of them all, which is “I didn’t know I needed to be HIPAA Compliant.” Or, if we ask the question preemptively (which is our goal here): “Do I (and my organization) need to be HIPAA Compliant?”
- you handle PHI to any degree. If so, you definitely need to be HIPAA compliant. And note, it’s not only Covered Entities ( health plans, health care clearinghouses, and health care providers who handle or electronically transmit PHI ) who need to be compliant, but their business associates (BAs) as well (see below). Typical covered entities include doctors and dentists, nursing homes and psychologists, as well as HMOs and company health plans to name a few.
- you are a Business Associates, ie, any person or entity who performs functions, services, or activities on behalf of a covered entity. Examples of Business Associates include claims processors, CPA accountants, attorneys, consultants, and benefits managers. Understand that a covered health care provider, health plan, or health care clearinghouse may also be a Business associate of another covered entity. Note: A cloud service provider for healthcare (a HIPAA compliant specialist) is also considered a Business Associate.
Other Common “I Didn’t Knows”
Even so, some may still protest (and do). Maybe it’s a healthcare organization that failed to encrypt a laptop or mobile device that stored patient information, or the employee who naively left a device on the front seat of his car and came back to find it stolen. The possibilities abound:
- I didn’t know my network could get hacked by falling for a phishing scam
- I didn’t know my managed service provider needed to be a cybersecurity expert (an MSSP), securing my servers/infrastructure & applying regular security updates
- I didn’t know my FTP server files needed securing, with password protections
- I didn’t know I needed to encrypt my emails containing PHI
- I didn't know a risk assessment could help identify where PHI may be compromised
- I didn’t know that carrying Cyber Liability Insurance is a great idea, if a data breach (or legal claims resulting from a breach) ever did occur. Technology Errors and Omissions insurance would also provide me with protection from mistakes my employees could make that might hurt my clients financially.
- I didn’t know a screensaver that automatically locks my desktop after a period of time is needful to protect PHI
And of course, our old favorite:
- I didn’t know post-it notes with my passwords out in the open are a (very) bad idea!
We see then that HIPAA regulations cover not only the kinds of entities responsible, but also how PHI is to be handled. Maintaining HIPAA compliance requires us to not only know these things, but also to take action on them.
A Quick HIPAA Overview
Protecting the confidentiality, integrity, and availability of medical data then is the overarching goal of HIPAA. But what does that really entail?
In brief, we must first understand the important distinction between compliance and certification:
- HIPAA Compliance refers to following the proper rules in accordance with requirements and regulations set forth by Health and Human Services (HHS) policies or guidelines. Understand that this is an ongoing requirement - not a once-and-done action.
- HIPAA Certification , on the other hand, is the process, typically involving a proven training program, of attesting that a person has completed an educational course. There is no single, HHS-authorized program for this. There are a number of reputable programs, however, that can guide your organization on the road to compliance, and help you to obtain a seal of compliance verification.
With this in mind, the following steps will be critical:
1. Start with conducting a complete risk assessment of your organization.* This is a vital part of HIPAA’s Administrative Safeguards . It entails identifying the ePHI (electronically protected health information) that your organization creates, receives, maintains or transmits; including any vendors or consultants that handle ePHI, along with the “human, natural, and environmental threats to information systems that contain ePHI.”
But identifying the risks to ePHI - as we’ve said - isn’t once and done. The following represents what a typical, monthly gap remediation process will look like for maintaining HIPAA compliance for your organization:
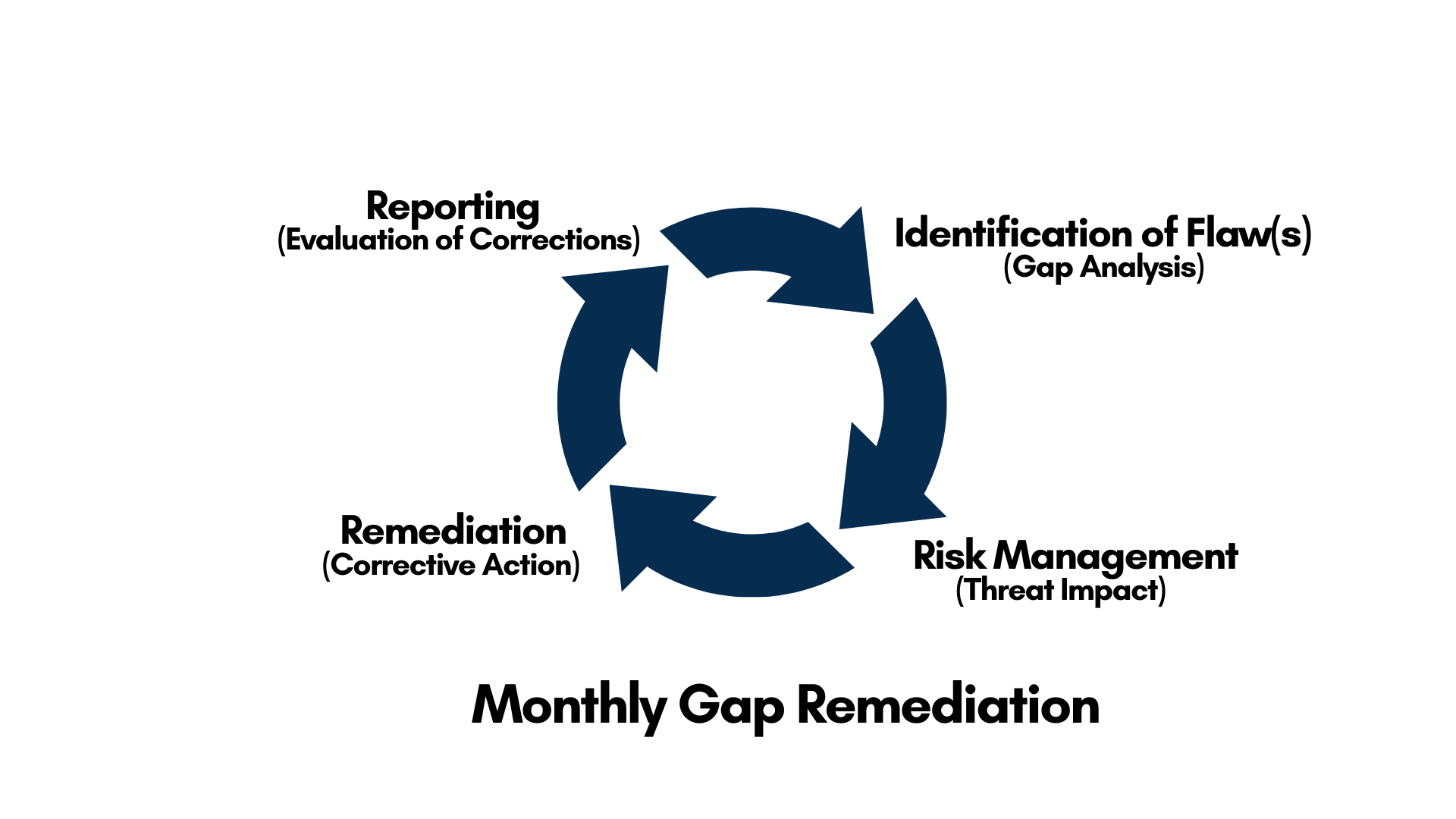
*Note: An organization’s Risk Assessment will include documented policies for the storage, transfer, disposal and reuse of data; logs and audits of software and hardware use and access; policies in place to address data transmission over the Internet through e-mail, private networks and private clouds; quality control of errors and failures, such as with altered, destroyed, recovered and backed-up data; and dynamic access and availability of data.
2. Ensure that Physical Safeguards such as locks and cameras are in place to limit access to workstations, networks, and servers. It's important to stress again that failures to lock up laptops, hard drives, etc. have led to numerous, costly data breaches.
3. Ensure that careful Technical Safeguards , including appropriate access controls and permissions, are being used to limit access to ePHI.
4. Secure a business associates agreement (BAA) with a compliant hosting provider . All HIPAA data handlers (covered entities) who host, receive, transmit, or exchange ePHI are required to sign a Business Associates Agreement - a HIPAA-mandated, legal contract that confirms a patient’s data will be kept confidential, both in transit and in storage on all servers.
5. Ensure your HIPAA-compliant infrastructure is governed by administrator controls which will authenticate user-access to the environment. A system of developing unique user IDs and passwords, as well as procedures for login, logout, decryption and emergencies, should be in play. Once a determination is made regarding the appropriate access and permissions for your team, admins can set these unique user IDs.
6. Ensure that data encryption (the industry standard) is being used to protect the integrity of data - in storage and in transit - on systems that contain ePHI.
7. Ensure that monitoring for vulnerabilities, backups, and audit/activity logs are being used to track ePHI access, or access attempts.
This is just a broad sketch of what HIPAA regulations require. Understanding what your particular organization will need to protect PHI is critical. A HIPAA hosting specialist will be glad to discuss with you what solutions will best fit your company, while helping you to keep your costs low. Best of all, we’ll help you avoid the temptation to say “I didn’t know,” because you thought ahead about what protections your clients really need.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








