How to Minimize Cybersecurity Failure? Plan for it
'If you fail to plan, you are planning to fail'

While there’s some debate whether Benjamin Franklin or someone else said it first, the advice remains solid for the modern cyber landscape. Yet, in today’s competitive environment, not only is planning critical — but so, too, is planning for plans to fail.
Because adversaries have the first-mover advantage and tailor attacks to penetrate defenses, accidental survival is not a sufficient plan. Instead, organizations should innovate to survive. In fact, innovation has become so important to defense today that there is a developing field of study around it, and one clear thread is: intentional innovation.
Innovate and Integrate to Survive
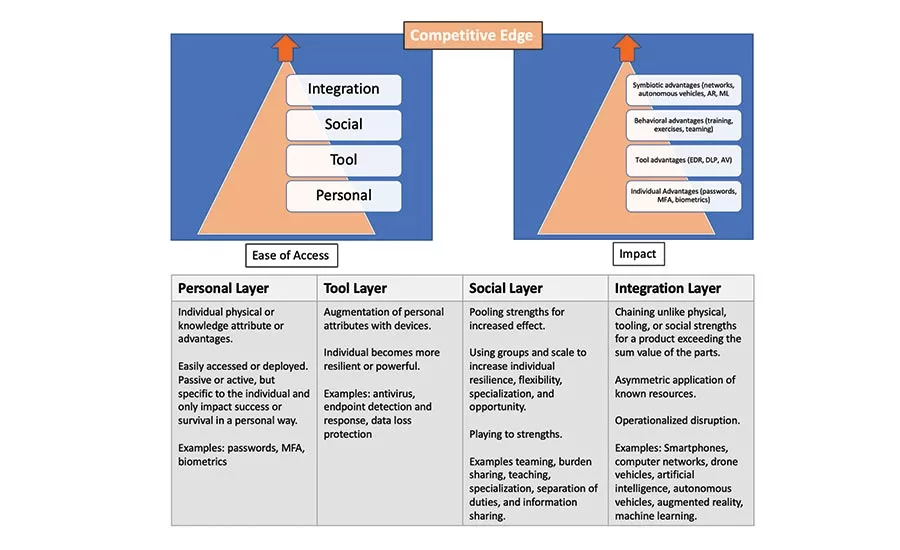
Survival innovations develop in a series of layers, starting with the easiest to access and deploy, and then building in impact from individual defense to environmental influence.
In the cyber world, the simplest personal advantages include unique passwords and biometrics. These unique, personal items help keep us safer in a singular and direct way and with their nominal protection in place, the next level is tools.
Tools, like encryption and antivirus software, increase protection by augmenting the power and efficacy of our personal defenses. With them in place, organizations can spend time on social behavioral activities, such as exercises and training. This development layer, which includes sharing of knowledge and tactics, creates numerical advantages across the population of users, and a culture of mutual defense awareness. And finally, when the culture is in sync, integration can happen.
Integration takes unlike ideas and binds them into a synergistic, multifaceted support system. New artificial intelligence (AI)- and machine learning (ML)-based systems function along these lines. And apart from cybersecurity, autonomous vehicles provide a great model of synergistic integration at work. They fuse complex vehicles, computers, radars and communications equipment for purposes well outside their original intent. It’s all about the asymmetric application of known resources, where a mixing and matching enables us to harness and operationalize the disruptive nature of integration.
Our world is already remarkably integrated and, barring catastrophe, there’s no going back. Thus, it’s important to embrace the benefits and risks. With integration, the time-honored, linear construct of “tools vs. defenses” gave way to dynamic concepts of strengths or weaknesses. Now, strong can only be defined as accounting for and responding to more survival variables or acting with more integration than competitors.
In cyberspace, malicious tools are generally created to autonomously hide, pivot and defend themselves — infiltrating network seams or gaps, going fast or slow as the situation demands, and with a variety of malicious counter-measures available to deploy. Effective defenses are semi-aware environments capable of acting against intruders at a scale and speed that exceeds human capacity; notifying humans of incursions; and applying some level of self-healing resilience. Yet still, integration creates gaps, and we could say that the most dangerous cyber threat is a human at an endpoint using tools. While humans inherently synthesize, the biggest threat is the intuitive leap. At times, an adversary will find a way to use common tools to create unexpected results — or worse, she’ll try unexpected things with great success. For this reason, defenders are one bright idea (or flight of fancy) away from a really bad day. Every. Day.
Emergency response and recovery plans exist because natural events challenge day-to-day operations. When storms and fires disrupted physical business operations, we created response plans. When we committed to electronic infrastructure, we planned for the same natural events disabling our systems. With new developments came new opportunities for both good and bad.
Today, committed, resourced human adversaries are attacking with greater frequency and precision than Mother Nature herself and unfortunately, every network will suffer a breach or attack. Malicious actors automate activities across the attack chain, use environmental events as opportunities or distractions for attacks, and even, create disasters to facilitate expansive, integrated operations.
Since integration will only increase, we have to integrate our defensive planning. Operational planning should include the anticipation of a worst-case disruption, as well as content on how to fail effectively and rise again, part of which is retaining sensitive information and business continuity in a cascade of contingencies. If Ben Franklin were a CISO today, he may say, “If you aren’t anticipating complete failure, you really aren’t planning at all.”
In his June 2007 Harvard Business Review article “How Successful Leaders Think,” Roger L. Martin focused on integrative thinking. In short, he defined it as employing an opposable mind or being able to think through problems without “choosing sides” in order to create the best choices rather than the obvious ones. Integrative planning is the intentional, applied version of this concept. By refusing to accept our existing, prepared solutions as inevitable end states, we can play out the entire scene — all the way to failure — and gain valuable insights along the way.
By untethering ourselves from the inertia of prior investments and past decisions, we gain the flexibility to consider new options and see opportunities across the full environment – technical, physical, policy and political – for comprehensive, integrated solutions.
Take and Break Plans
It’s recommended to take our plans and break them. Attack them until they fail, or artificially fail them. Take prized resources out of action and consider, “What then?”
For an integrative planning exercise, consider events that could possibly result in collapse, particularly if the event is unusual or unaddressed. Steer clear of probability for now. It’s a great tool for prioritization, but for a comprehensive response review, stick with the possible. Stress every response and recovery action not just to failure within its normal space, but from an integrated threat or surprise. For instance, do you make regular, encrypted, remotely stored back-ups? What happens if you need the back-ups and they are denied to you for any reason? Not likely, perhaps, but possible, and then what? Do you have a notional roadmap to recovery, an option to get back to production until you can solve the bigger problem? Maybe you should. This activity will give you a sense of how hard you need to push for things to fail and help you build a list of recovery considerations. It will also give you a sense of your strength and resilience.
Integrative planning is not to create solutions for every possible event, but rather, to identify what is absolutely critical and understand how it may be taken down from anywhere in your ecosystem, the impact of the loss, and what initial recovery steps might look like for your organization. Your worst-case plan need not be as solid or granular as normal operational plans and procedures, but an idea of the cost, scope and viable partners to help with a reconstitution of your most critical infrastructure will speed your recovery. Facilitate relationships across your organization and externally so, should the bad day arrive, your answer to “What are we going to do?” is a conceptual, living recovery roadmap, complete with a list of partners to call and a rough order of magnitude for costs.
As CISO Ben Franklin may also say, “Prevent disaster by examining failure.”
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








