Rethinking "Red Flags" - A New Approach to Insider Threats
A whole threat and whole person approach to efficient and effective insider early warning is needed.

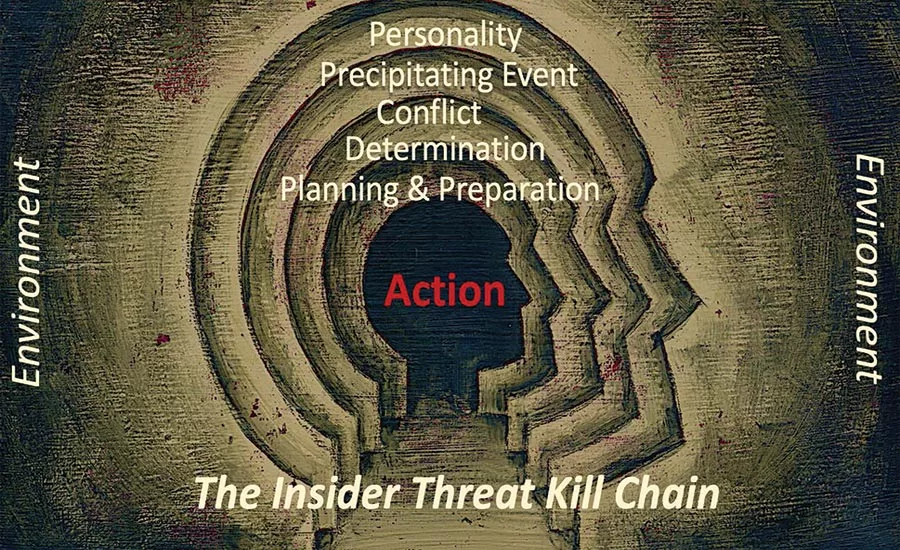
Indicators can be used to track, predict and stop attacks, but we first need to understand the “insider kill chain.” This is the path that an insider takes as they move toward action.

Malicious insiders pose an existential threat to any organization. Insider theft, fraud, sabotage and violence continue unabated. Victims are left damaged, sometimes terminally. Technical countermeasures only address part of the problem and are increasingly expensive, complicated and difficult to integrate. New regulations are adding additional requirements to overburdened staff. Throughout this all, insider program funding remains insufficient. The bottom line – the job isn’t getting any easier.
At the core of the insider mitigation process is the insider “red flag” methodology, a legacy approach that is increasingly failing us. The evidence is all around; insider incidents increasing in number and impact, most with abundant (but generally unactioned) “red flags.” How often do we look back following an incident and immediately recognize clear indicators? Far too many times.
The reasons for this failure can be found within most organizations. First, insider threat early warning programs often lack the attention, expertise, funding, incentive programs, information-sharing processes and programmatic approaches necessary to be successful. Second, organizational cultures often undercut the effectiveness of early warning programs through denial, privacy concerns, lack of accountability and a cognitive bias toward technical cybersecurity. Third, faulty assumptions such as “it won’t happen here,” “red flags are reported and responded to,” and “people will do the right thing” undermine the process. Finally, there is “social shirking,” meaning no one wants to be a tattletale, many folks avoid conflict and some pass the buck on this important issue.
But all is not lost! There is some good news – significant opportunities exist for stopping insider attacks, around which an affordable and effective early warning system can be created.
These opportunities are created by the simple fact that insider attacks are generally not impulsive in nature. Regardless of motivation, the insider plans for months or even years before action. And no matter how hard they try to cover their tracks, they leave evidence during the slow progression from idea to action. This evidence is observable; the changes in attitude and behavior are discernable and detectable.
More importantly, these relatively slight changes in attitude and behavior serve as predictors of how an insider will react to greater stress. In essence, minor events will showcase a natural reaction, allowing one to predict reactions to major events. By knowing that specific personalities are negatively affected by specific events, one can identify “tripwires” for more significant problems.
To summarize, insiders tend to slowly evolve toward action and often provide indications of their progression. Leveraged properly, these indicators can be used to track, predict and stop attacks.
The Insider Kill Chain
To exploit this behavioral evidence, we first need to understand the “insider kill chain.” This is the path that an insider takes as they move toward action.
The first stage is “personality temperament.” Essentially, this is the nature of person you hired. For our purposes, an important personality differentiation is whether this person is predisposed either toward “self-healing” or “self-destruction.” Elements that sway a personality toward self-destruction (and insider attacks) include violent tendencies, psychological imbalance, vengefulness, etc. Malevolent qualities known in psychology as the “Dark Triad” of narcissism, psychopathy and Machiavellianism can also increase an insider’s self-destructive nature.
The second stage is a “precipitating event.” Our focus is on stressors that create emotional change, such as personal or professional crises.
The third stage is a “conflict,” which is often a self-expression like dissatisfaction with a superior, colleague, or the entire organization.
The fourth stage is “determination,” which is often exemplified by refinement of a mindset like increased risk-taking, open hostility, social withdrawal, identification with violence, etc.
The fifth stage is “preparation,” often taking the form of reconnaissance, acquisition of materials, drafting of manifestos and other attack precursors.
Finally, there is the “attack.” This is the endpoint of resentment that has been building against an organization or system that the insider believes has unfairly treated them.
Just as there is a critical path or “kill chain” for each attack, there are critical stages of life. The ages between 35-45 years old are particularly relevant to insider threat mitigation. These are the ages known for reevaluation of life choices and life goals. For our purposes, this is a critical time because it is the highest point of the symbiotic relationship between one’s personal and professional lives.
Known commonly as a “mid-life crisis,” divorce and career change are highest during these years. As you can imagine, a strong partnership can carry someone through a bad work situation and a good professional situation can carry someone through relationship stress, but the simultaneous collapse of both often results in increased psychological vulnerability for the employee and increased risk for their employer.
Applying the Insider Kill Chain
So, how do you use the insider kill chain to your advantage? You do so by creating an early warning system that is more effective and efficient than the traditional “red flag” methodology.
Greater effectiveness is achieved by taking a holistic “whole person” and “whole threat” approach. A “whole person” approach is contextual and psychosocial, using personality, environment and precipitating events to identify insider risk. A “whole threat” approach addresses the common root causes that result in different attacks forms (data theft, fraud, sabotage or violence). It leverages common sense and objectivity to understand the insider personalities relevant to your organization, the precipitating events that can turn those personalities to malicious action and the corresponding tripwires that require your action.
Greater efficiency is gained by focusing on the incidents of greatest impact and probability by narrowing the attention to critical materials, data and processes and those with access to those items. Tailoring the system to your organization’s risk tolerance, culture and financial resources further enhances the likelihood of success.
But how to best observe and assess this behavior? Well, it turns out that humans are quite good at detecting insiders; they naturally create behavior baselines for everyone they know, they have a ‘sixth sense’ for deviations from those baselines (for anomalous behavior) and they can instantly evaluate actions within context. In fact, independent behavioral observation is a leading way that malicious insiders are discovered.
And remember, the insider kill chain takes place within your organizational environment – which you control. Just as you can design a building to enhance and enforce an organization’s security measures, you can design an environment to enhance and enforce your insider risk program. The bottom line is that you can have your organizational environment work for or against you.
The 13-Step Framework
To create a “whole person” and “whole threat” early warning system for your organization, this framework outlines best practices for knowing the predisposition, precipitating events and tripwires of potential insiders, so that you can better identify insider threats. The framework is designed with an understanding that there are areas that we control and areas we don’t. Some of you may be familiar with the Serenity Prayer: “Lord grant me the serenity to accept the things I cannot change, the courage to change the things I can, and the wisdom to know the difference.”
As noted earlier, we control the environment. To a much lesser degree, we control the personalities of those we work with – by who we hire in the first place. As the environment is where we can administer the greatest mitigation, the framework is focused on building in the strongest insider threat countermeasures allowable by your organization’s culture, capabilities and resources.
The 13-Step Framework
- Step 1: Determining your early warning program goals. The intention is to know, understand and help your people focus on realizable achievements, match your organizational culture and resources, determine what is not achievable and create milestones for desired progress.
- Step 2: Advertising your program. The goal should be open and transparent. To achieve this, one must clearly state what they are doing and why, and provide opportunity for questions and recommendations. This will help avoid claims of hidden agendas. By highlighting the co-dependency of employee and organizational success, you can promote the value of the program to employees. To make your points, consider using accepted norms like the public security program slogan “See Something, Say Something,” or sports analogies like “what’s good for the team is good for the player.”
- Step 3: Creating an empowered stakeholder team. Put simply, you should “crowdsource” your insider threat program by including representatives from the C-suite, legal, human resources (HR), informational technology (IT), administrative, financial, compliance, security and the general employee population. Supported by a C-suite “champion,” this team can help you implement cross organizational communication and information sharing. As 70 percent of insider attacks occur within 60 days of an employee leaving the organization, it is critical that HR immediately notify of voluntary and involuntary departures and anomalous employee behavior.
- Step 4: Identifying your critical materials, products, data and processes. Often referred to as the “crown jewels,” this list is usually longer than you think, as it should include anything that can be monetized or used by attackers to create harm.
- Step 5: Identifying everyone who has access to your critical items. This is also a longer list than you think, and includes partners, vendors, suppliers, cleaning crews, etc.
- Step 6: Determining the early warning capability of your partners. This includes your vendors or clients with access to your critical materials. Remember that attackers look for the weakest link, which could easily be one of your partners.
- Step 7: Determining your leading vulnerabilities. These are the insider attacks of greatest probability and incidents of greatest negative impact.
- Step 8: Determining your most relevant insider attacks. These should be discernable by your response to step 7 (identifying your leading vulnerabilities), which is in turn based on steps 4 through 6 (what are you trying to protect and who has access to those items). These could be sabotage, intellectual property/sensitive data theft, insider fraud, unintentional insider threat and workplace violence.
- Step 9: Understanding the insider profiles most relevant to you. Your answer to step 8 should help you develop a watchlist of the profiles and trip wires most relevant to your situation. The idea is to get into the head of the attacker and understand what sets them off, how they would strike out and how they would plan their attack (see below for common insider profiles).
- Step 10: Determining the early warning “sensors” available to you. These folks are in position to spot your designated tripwires; particularly the HR, IT and Security departments. HR can highlight performance and behavioral issues, IT can highlight network anomalies and Security can highlight policy violations. Line managers and employees can provide firsthand observations of unusual behavior. Public record checks can reveal arrests, foreclosures, etc. Finally, potential insiders can highlight themselves through requests for managerial assistance, organizational change or conflict mediation.
- Step 11: Increasing the awareness, appreciation and use of profiles and tripwires. This means educating your managers on personality types and the impact of precipitating events and how to spot indicators of a negative response to an event – known as the “tripwire.” Managers need to understand that behavior and of behavior observations do matter. A simple and private reporting mechanism is valuable. Some organizations may want to consider making reporting of anomalous behavior required of employees. While not a small step, such a policy tends to eliminate employee ambiguity and personal judgement and reduces missed indicators.
- Step 12: Determining how you will respond to a potential problem. While specific activities are situation and organization dependent, there are a few notable best practices to consider. First, predetermine lines that if crossed, require further action. Second, maintain an objective perspective of the situation, starting with the premise of innocence, using observation as a starting point for further information collection, not judgement. Finally, predetermine status that if achieved, active monitoring will end (reverse tripwires). As stated earlier, the intent is to focus on employee welfare. This will enhance morale, positively reinforce stakeholder buy-in and coworker reporting and make the attorneys happy.
- Step 13: Instituting continuous program improvement. This means conducting continuous evaluation, tabletop exercises, “red-team” exercises, soliciting employee feedback and recommendations and incorporating appropriate changes.
Insider Threat Profiles
To augment the framework, the following are general descriptions of the insider attack types and their commonly related insider profiles. Each profile is made from the personality characteristics, critical events that negatively affect them and the tripwires that should prompt action.
Unintentional insider threat. These insiders act without malicious intent but become a threat through negligence or outside manipulation. Common personality characteristics include being flighty, unfocused, disorganized, scatter-brained, stressed and strained. Common precipitating events include new personal or professional distractions. Common tripwires include personal cell phone/computer overuse, unwittingly providing sensitive information to outsiders, discussing sensitive matters with uncleared personnel, leaving sensitive documents or devices accessible to others, posting confidential organizational details to social media sites and consistent failure to meet deadlines.
Intellectual property/sensitive data theft. These insiders seek to benefit themselves or others by stealing valuable data or materials. They may be working alone or in collaboration with an outside malicious actor. Common personality characteristics include entitlement, narcissism, anti-social behavior and a desire to control all things. Common precipitating events include a negative personal financial event, failed promotion effort, poor performance review, unmet career aspirations, resignation or termination.
Common tripwires include “borrowing” office items for home use, attempting privilege escalation, conducting questionable downloads, violating cybersecurity policy, working out of profile hours, transferring data and/or printing during out of profile hours, stealing inventory and bringing unauthorized recording equipment into work.
Insider Fraud. These insiders seek personal gain through their attacks. Common personality characteristics include egotism, entitlement, privilege and self-importance. Common precipitating events include significant additional expenses, negative personal financial events and unmet career and/or lifestyle aspirations. Common tripwires include living beyond one’s means, debt collection, violations of financial policies, intentional data manipulation, use and/or close association with a known supplier, minor fraudulent expenses, violations of insider trading, demonstrating excessive control over financial duties and exhibiting shrewd or unscrupulous behavior.
Sabotage. These insiders strike out against an organization with intent to harm its functionality. Common personality characteristics include anger, vengefulness, vindictiveness, disengagement and destructive behavior. Common precipitating events include confrontation with management, poor performance review, failed promotion effort, demotion, workplace embarrassment and termination. Common tripwires include the testing of security procedures, defacing company website pages, “accidentally” breaking a component in a critical machine, contaminating a clean room, altering enterprise software, misconfiguring products to cause failure and workplace harassment or violence.
Common personality characteristics include aggressiveness, emotional detachment, confrontation, control-seeking, disengagement, lack of remorse and strain. Common precipitating events include a negative family or relationship event. Common tripwires include emotional outbursts, failure to communicate and/or work in groups, bullying, difficulty taking criticism, boundary violations, refusals to work with others, violent threats, physical altercations and reflections of extremist beliefs.
Workplace violence. These insiders seek to strike out against the organization to cause bodily harm to people within the organizations. Common personality characteristics are aggression, emotional detachment, confrontation, disengagement, strain and a lack of remorse. Common precipitating events include negative family or relationship events. Common tripwires are the same as those for sabotage, which includes emotional outbursts, failure to communicate and/or work in groups, bullying, difficulty taking criticism, boundary violations, violent threats, physical altercations and reflections of extremist beliefs.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








