Metrics and ROI That Matters in 2020 and Beyond
If enterprise security continues to mature as a business function, in most enterprises, senior management will ask for a set of metrics to measure performance.

Why spend time, resources and money on your enterprise security program if you can’t determine whether it’s working or not? It’s just as important to establish the right metrics for a security program as it is to have such a program in place.
One of those metrics is salary and compensation. According to Jerry Brennan, founder and Chief Operating Officer of Security Management Resources (SMR Group), “The most common question asked by candidates when they are considering a new position is “What does the compensation look like?’”
We are partnering with The Foushée Group, a leading compensation research company that has produced the annual Security & Compliance Compensation Survey for 18 years. The survey is designed to provide accurate and timely compensation information on 78 security and compliance positions to companies who seek to market price their positions to the national market. The survey input is not based on self-reporting, rather the survey questionnaire is sent to Human Resources professionals, who review the provided job descriptions and match their jobs to the survey position descriptions. All data reported is aligned with the Department of Justice Safe Harbor Guidelines for reporting compensation information. No individual company data is identifiable, and the data is reported in weighted averages, median, percentile distributions and other pertinent data. Participating companies range in revenue size from less than $500 million to more than $150 billion.
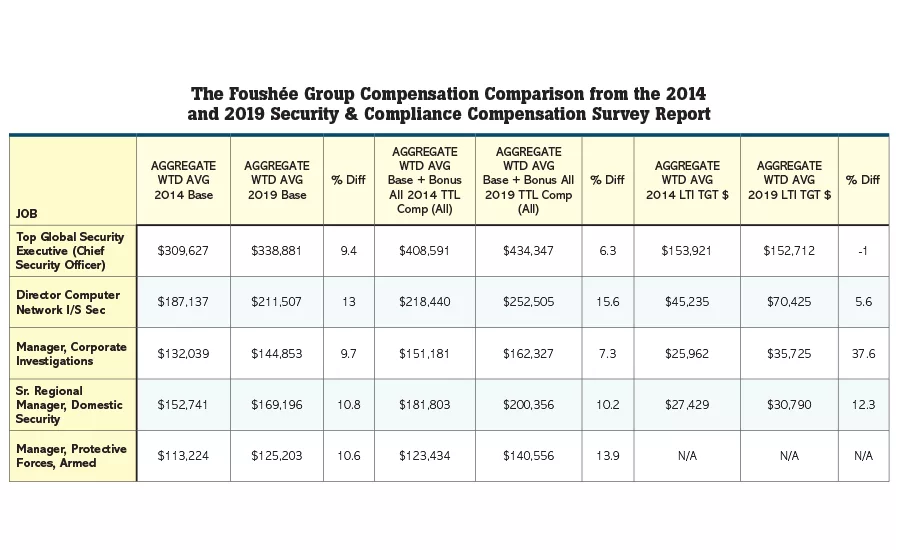
Compensation surveys are a snapshot in time, reflecting the data at the date of the information. We asked the Foushée Group to provide some trend data from the 2019 survey. Here are five enterprise security positions from the 2019 survey data:
- Top Global Security Executive (Chief Security Officer)
- Director, Computer, Network & Information Security
- Manager, Corporate Investigations
- Senior Regional Manager Domestic Security;
- Manager, Protective Forces Armed
In addition, The Foushée Group pulled data from the published 2014 survey and compared data points to the published 2019 survey for the same positions. All data points (weighted average, aggregate) include base salary, total compensation (base plus bonus) and annual Long-Term Incentive (LTI) target.
Top Global Security Executive (Chief Security Officer)
When comparing reported data from the 2014 survey to the 2019 survey, the CSO positions base pay weighted average in the aggregate increased by 9.4 percent over the reporting period to $338,881 annually. Base salary plus bonus increased by 6.3 percent to $434,347 annually. Bonuses are pay at risk and tend to vary based on company an employee performance. Most CSO positons are eligible for a LTI, usually paid in company stock over a set number of years. The LTI annual target decreased by approximately one percent over the reporting period to $152,712 annually.
Director, Computer, Network & Information Security
Comparing data from the 2014 survey to the 2019 survey, the Director, Computer, Network & Information Security base pay weighted average in the aggregate increased by approximately 13 percent to $211,507 annually. Base salary plus bonus increased by 15.6 percent to $252,505, while those positions eligible for LTI, the target increased by 5.6 percent to $70,425.
Manager, Corporate Investigations
Comparing data from the 2014 survey to the 2019 survey, the Manager, Corporate Investigations base pay weighted average in the aggregate increased by approximately 9.7 percent to $144,853 annually. Base salary plus bonus increased by 7.3 percent to $162,327, while those positions eligible for LTI, the target increased by 37.6 percent to $35,725.
Return on Investment – What Is It and How Do I Get Some?

By Darrell Clifton,
Contributing Writer
Editor’s Note: Another valuable metric that our readers continually ask for is ROI. Here is part 1 of a 4-part series on this important metric.
When you are trying to purchase those security gadgets that make your job easier or your organization safer and more secure, you are generally asked to show a Return on Investment (ROI), which is not as complicated or unreachable as some might think. In fact, in enterprise security, we have a couple of advantages that our company’s revenue departments may not have. In a four-part series, I will outline some strategies that might help you show security's value and benefit to your organization.
First, let’s agree on how security budgets generally work. The things we buy (our expenses) are generally divided into two categories – Operational and Capital Expenses. Operational Expenses include items such as wages, supplies, leases, service agreements, uniforms, travel and more. Operational Expenses are generally recurring or ongoing. Capital Expenses, on the other hand, are usually improvements to the building or its contents and do not include labor, ongoing or intangible expenses. Examples of Capital Expenses are a new fire alarm, video system, emergency operations center, or report-writing software.
Operating Expenses do not require an ROI justification unless someone notices the hot tub that you billed to the company under “networking.”
When budgeting Operating Expenses, we are likely to compare to the prior year, quarter or month, and then explain the difference. For example, if supplies increased by 20 percent, you might have to articulate how the new photocopier uses more expensive ink cartridges or the additional staff are using more office supplies. ROI does not normally come into play for Operating Expenses because they are self-explanatory, but if it does, the strategies outlined here might still come in handy.
Capital Expenses are not monthly (usually), but more likely distributed quarterly or annually. At a certain time of the year, each department will be asked for their shopping list. This is where ROI comes into play, because Capital is like a loan from the company and ROI is how the loan will be repaid. Since enterprise security does not generate revenue in most companies, the return has to be explained or justified differently.
Because of tax laws and sustainability, your company will likely not let you use Capital for the following: additional staff; classroom training; overtime; travel to a conference or the conference registration; items below a certain dollar amount. These are expenses and they go in your operating budget.
Life Safety – Security’s Secret Sauce
Life Safety is a term used in our industry to describe the systems contributing to the safety and care we owe to our guests, customers and employees. A failure of our life safety system is not only a threat to the humans who rely on it, but they can be a liability for your company if it is not addressed.
Life Safety is also a state of mind or feeling that evokes both positive and negative emotions. A dark parking lot, for example, makes employees feel unsafe or even scared. A fire alarm that continually “falses” becomes an annoyance and therefore less effective.
We all know that a lawsuit filed after a criminal act on our property is less about the perpetrator or the circumstances and more about the conditions or physical safety measures that were in place or should have been in place to prevent it. It is our job to anticipate those acts and take action to prevent them.
A simple example is a dark parking lot. Our emotions tell us this is scary. Our experience tells us this is an environment conducive to criminal activity. These conclusions will be compounded if a violent crime actually occurs.
Let’s say you have a dark parking lot and you want to request some lighting. Your CFO might respond with agreement but may add that our parking lot has been dark for years and nothing has ever happened. You need to attack that argument on two fronts.
First is Risk, which is measured by combining Likelihood and Severity. The likelihood of an assault in your dark parking lot will depend on your neighborhood, prior incidents and physical conditions. A little bit of research with the police or local news will help articulate likelihood. Severity is subjective but is easy to measure when violence is involved. Burglaries (which will also be reduced by lighting) are not as severe as an assault or other acts of violence. Therefore, Severity, when humans can be hurt, easily gets a high score.
Second is the feeling of Safety. Employees who feel unsafe traversing your dark parking lot are your best advocates. This does not mean you put ideas in their heads and tell them how at-risk they are going home at night, but it may mean tracking their comments and using them for your justification. Depending on your business, you may have documented comments from guests or visitors who will tell you they feel scared coming to your building after dark. This may even affect business or employee morale so if possible, get testimonials from your sales folks and Human Resources people.
The bottom line in this case is really not the bottom line. None of your executives want to have an environment where those in it are at risk or even feel unsafe. The Life Safety argument is compelling and effective for raising your request to the top of the wish list, so use it with sincerity. If your Life Safety request does not turn out to do all you promised, it will be harder to use it next year, so make sure your facts are not exaggerated.
In upcoming articles, we will outline more conventional ways to get you the things you want.
About the Author
Darrell Clifton, CPP is the author of Hospitality Security. He was named by Security magazine as one of Security’s Most Influential in 2011. After 30 years in operations, he is now an adjunct professor and consults for the Kolins Security Group. He provides expert testimony and training on all things Hospitality, including Hotel, Nightclub, Restaurant and Bar security. Contact him at darrell.clifton@kolinssecuritygroup.com
Senior Regional Manager Domestic Security
When comparing data from the 2014 survey to the 2019 survey, the Senior Regional Manager Domestic Security base pay weighted average in the aggregate increased by approximately 10.8 percent to $169,196 annually. Base salary plus bonus increased by 10.2 percent to $200,356, while those positions eligible for LTI, the target increased by 12.3 percent to $30,790. This position has the organizations largest geographic region security function reflected by the company’s operations in a particular area, says The Foushée Group.
Manager, Protective Forces Armed
The Manager, Protective Forces Armed base pay weighted average in the aggregate when comparing data form the 2014 survey to the 2019 survey increased 10.6 percent to $125,203 annually. Base salary plus bonus increased by 13.9 percent to $140,556, while most of those surveyed reported the positions ineligible for a LTI Grant.
Based on the data reported, says The Foushée Group, most security positions have increased base pay, bonus and long term incentives as companies try to maintain a competitive market positon. Many factors influence the reporting numbers, such as company participation, ability to pay, compensation philosophy and value of the position to the company.
The Foushée Group suggests that enterprise security leaders should participate in a compensation survey typically housed in their Human Resources group. The first question leadership should ask Human Resources is: “Are my jobs market priced annually?” and if not, why not? "In today’s market," says The Foushée Group, "a company cannot afford not to understand market conditions as it relates to human capital. If your company doesn't, you can bet your competitor does."
The Security & Compliance Survey
The survey solicits data and the competitive practices of 78 management, professional and technical positions) in the security and compliance field. Current security and compliance job families include:
- Classified Materials/Material Controls • Computer & Info. Security
- Console Operator
- Corporate Investigation
- Domestic Security
- Emergency Preparedness
- Executive Protection
- Global Compliance & Ethics Security Programs
- Global Security
- International Security Threat Analysis • Network Security
- Nuclear Accountability
- Physical Security-Unarmed
- Product Security
- Protective Forces-Armed
- Regional/Bus. Unit Security
- Regulatory Compliance
- Security Clearance
- Security Systems & Training
The 2020 survey launched November 13, 2019, and participant input is due to the Foushée Group by January 31, 2020. The report will be published on March 30, 2020. Extensions are available on an individual basis.
According to The Foushée Group, organizations may participate in the survey free of charge, however, there is a fee for the comprehensive survey report, which includes the hard copy and e-version of the report.
For additional information on participating in the 2020 survey and report, please visit www.fousheesurvey.com or contact Steve Walker at 239-282-1929.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





