What are the Odds? How Vulnerable are You to the Latest Vulnerabilities?

Cybersecurity vulnerability management is a continuous race against time that is being compounded by the proliferation of new devices and applications within organizations.
Between 2015 and 2019, data from exploit-db reveals that the number of distinct products with reported vulnerabilities increased by 150 percent. Over this same period, the weaponization time for the creation of exploits to take advantage of these published vulnerabilities dropped from being several months to almost immediately. This drastic decrease in patching time has resulted in a situation where IT departments are faced with not having enough resources to identify and remediate critical vulnerabilities while having to continue to manage day-to-day business operations.
The Common Vulnerability Scoring System (CVSS) v3.0 used by the National Vulnerability Database (NVD) provides an open framework for communicating the potential impacts of IT vulnerabilities. It's a quantitative model that uses several metrics to generate a consistent numerical score that provides industries, organizations, and governments with a common understanding of how serious a vulnerability is. These numerical scores are then lumped into five tiers (none, low, medium, high, critical) which are intended to help organizations properly assess and prioritize their vulnerability management processes.
According to the Q1 2019 Quarterly Threat Report published by eSentire, on average, high and critical severity vulnerabilities (using CVSS v3.0) existed in about eight percent of externally facing assets across a sample from the more than 650 small and medium-sized enterprises that make up eSentire’s customer base.
The good news for organizations? Even with approximately eight percent of externally exposed endpoints being vulnerable, during this same period, eSentire observed only one successful exploitation of an externally facing asset, which was the exploitation of an outdated and unpatched Drupal web server.

The data from eSentire also shows that the insurance, technology and finance industries were observed to have the most exposed vulnerabilities. Despite these three industries being the most at risk of being exploited, the nature and diversity of vulnerabilities varied from industry to industry. For example, technology, finance, business services and healthcare all require a broad diversity of services running in their environments, making them vulnerable to exploitation through a large number of different vulnerabilities. In contrast, insurance companies tended to have less diversity in their technologies, which result in being susceptible to just a handful of exploits.
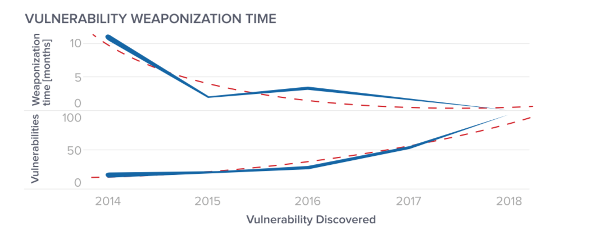
An analysis of the average weaponization time--the time between the discovery of a vulnerability and the publishing of a related exploit--results in an exponentially decreasing curve, while confirmed exploitable vulnerabilities tend to grow. Further, there is a decline in the average measure when multiple exploits have been published for a single vulnerability, or a vulnerability is discovered which happens to already have an exploit for it.
Additionally, the number of individuals or organizations focused on vulnerability research has grown (likely motivated by monetary rewards via bug bounty programs). Therefore, while the diversity of available products has increased, so has the number of individuals and organizations focused on discovering and responsibly reporting vulnerabilities. While this suggests applications are better secured, the scrutiny from researchers occurs most often after a product is deployed. Thus, the discovery and remediation of vulnerabilities remain a core aspect of good risk management businesses.
While regular patching is the best way to lower a company’s exposure to the risk caused by vulnerabilities, organizations should also be aware of gaps that may not be addressed by regular patching policies. These gaps can occur when researchers become frustrated with vendor responsiveness and publish their research independently of the vendor. Gaps also can arise when serious vulnerabilities are identified in applications or products outside the normal patching scope. An example of this occurred in February 2019 with the popular freeware archive tool WinRAR when a vulnerability was disclosed along with proof of concept code with exploitation in the wild occurring just five days after publication.
Limiting or restricting unauthorized applications can significantly reduce this risk but may not be feasible due to overhead costs or employee resistance. For example, eSentire found WinRAR present on 40 percent of endpoint customers, suggesting strict application policies are not adopted across the board. Organizations can compensate for this by maintaining an inventory of installed applications or the ability to rapidly retrieve this information from endpoints as needed.
To learn more about the types of vulnerabilities that impacting mid-sized organizations and what strategies you can implement to protect your business, download the Q1 2019 Quarterly Threat Report from eSentire.
Mark Sangster is an industry security strategist and cybersecurity evangelist who researches, speaks and writes about cybersecurity as it relates to regulations, ethical obligations, data breach incident response and cyber risk management.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!



