Using Environmental Risk Mapping and Analysis to Enable Effective Decision Making
Uninformed is unprepared. Build your own metrics and maps in order to make thoughtful, business-minded security decisions.
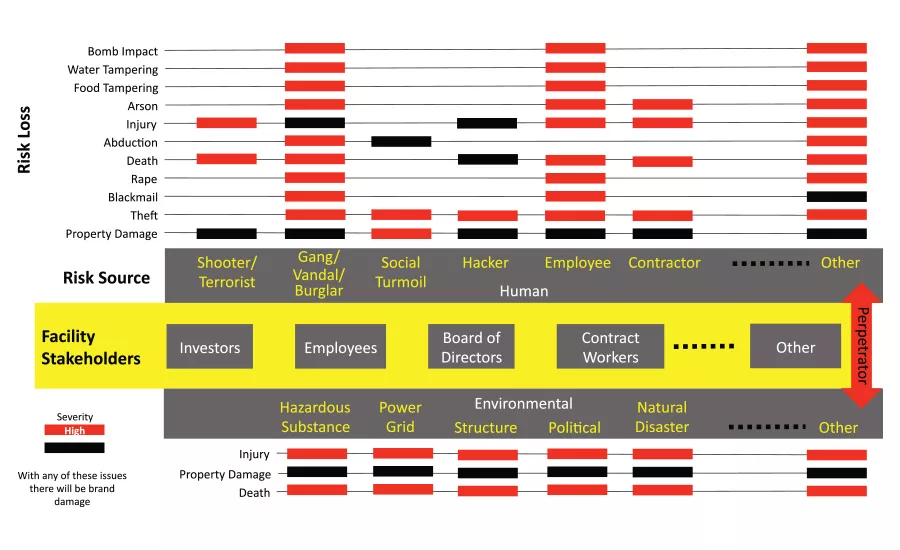
Figure 1
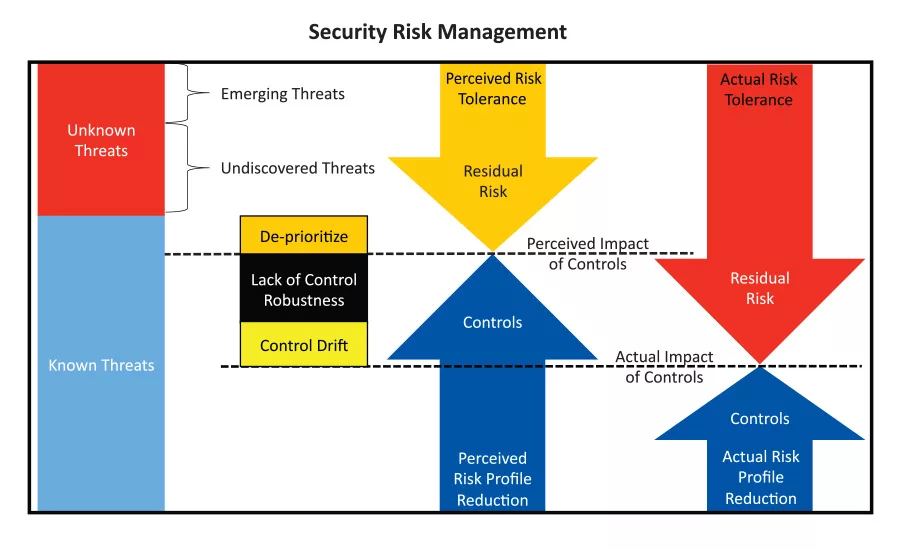
Figure 2
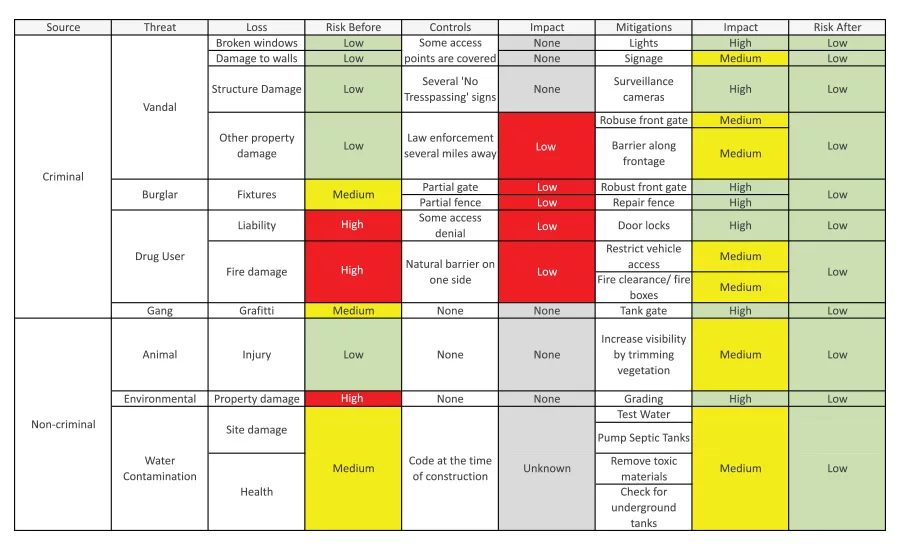
Figure 3. Simple FMEA section reflecting a risk mitigation phase on a remote camp property.
It should be clear by now that operating the way we have always operated is not a strategy for business survival. A lack of discipline in timely security-oriented decision making promotes the status quo and results in tragic events that could have been avoided or minimized. Being aware of threats, especially those that are rapidly emerging, has become more difficult in complex environments. Furthermore, the efficient application of resources has become more of a challenge as security leaders want to mitigate threats while not interfering with operational efficiencies and compromising business financial performance. A more structured approach to fact-based decision making and risk awareness is needed.
Environmental Scanning
Sound decision making is based on environmental awareness. A method for environmental scanning can be deployed in a methodical way to ensure that awareness is accurate. This method may be localized within a defined scope. The defined scope may be geographical or by line of business (LOB) across workflows. In either case, a definition of the scope is needed to assure that the size of the discovery area is manageable and to assure that boundaries are understood to avoid creep and overlap. Once the scope is clear, a Risk Map can be applied to gain awareness of threats and indicate who may experience harm as a result. This is meaningful as it gives decision makers the ability to make more informed choices by organizing critical information. Figure 1 illustrates an example Risk Map.
While there are several methods used for environmental scanning, this mapping method can create context quickly on a single page by connecting threat loss types to any set of stakeholders. In order to create the scan, a clear understanding of the scope is necessary.
To create the Risk Map, first, stakeholders need to be identified. These are the organizations “assets” that will experience harm physically, emotionally and financially. Next, the “perpetrators,” or originators of the threats, can be listed in two categories: “human” and “non-human.” Other configurations are possible, such as “internal” and “external.” The map is customizable to make the most sense within the context of the situation. Some examples of non-human threats are environmental disasters like earthquakes, tornadoes or floods. Human threats can include employees as well as individuals from outside the organization.
Each of these threat types can incur a variety of harm types, or risk losses, on the stakeholders of the organization. These threats may have a direct (damage to property) or indirect (power outage) impact. This impact may harm stakeholders directly or hurt the business financially due to an inability to sustain business continuity. To the extent that harm to the human occupants is possible, consideration should be given to minimizing harm through risk mitigations and through contingency planning. Risk can be thought of as the capacity of the environment for unwanted outcomes due to an unmitigated threat source.
Simply, unwanted outcomes may be stakeholder harm or loss. The severity of the harm may also be mitigated through preparedness and a rapid response from local support agencies. The perception of loss may significantly exceed actual loss due to social sensitivities. When this happens, the words “catastrophic” and “tragedy” quickly come into play.
In the mapping, the color coding of the harm types in relation to the perpetrator reflects the severity of the risk loss, or consequences. As an option, frequency of occurrence may also be considered in the event that severity is not as relevant to the analysis.
Risk Tolerance
Risk tolerance may be described as the meeting point between risk that remains in play and the controls that abate the risk. Figure 2 describes this graphically. An organization may be assuming a risk tolerance that they may not be aware of. A situational awareness is, therefore, needed to understand the threats within the prescribed scope. The “threat-scape” is dynamic and will change based on internal and external trends. This is presented in the other column in Figure 2.
As mentioned, risks that are unknown are tolerated unawares. These unknown threats can be simply divided into two categories: emerging threats and undiscovered threats. The latter can be minimized through a robust environmental scan as illustrated in Figure 1. The former must by managed by being informed about threats on the horizon. A proactive approach to mitigating or minimizing these threats can also minimize the harm that could occur.
Another aspect of risk that is tolerated comes from the impact of the controls that have been implemented. A control may not be as influential on the risk profile of the facility as first thought. In some cases, a risk mitigation is just a patch with a limited life-cycle. These mitigations could be referred to as “window dressing.” When the influence of the control does not mitigate the threat completely, residual risk remains and should be listed on the risk register as acceptable. In some cases, the residual risk is understood and given further consideration to increase the impact of the control. In other cases, the residual is not understood, and so it is tolerated unknowingly.
Implemented controls have an impact on risk that may be known and measureable. When these mitigations are put in place, the threat profile is impacted, however, over time these controls may become obsolete based on changes in the threat-scape, or they may have a reduced impact due to a lack of discipline from stakeholders. An operational procedure that influences risk may not be as effective as it was initially due to process changes. If procedures are enacted and reviewed, then a discovery opportunity will happen that gives potentially affected employees the opportunity to revise threat mitigating procedures. This review process can prevent drift in the influence of the implemented controls. When there is drift, the risk tolerance becomes larger than expected.
Risk tolerance may be influenced by timing and resources. Resource allocation to the reduction of risk may be delayed. During the delay, a threat may turn into a tragedy. This tragedy will impact the brand reputation and may harm stakeholders in a variety of ways. Many stories of companies that have misjudged the risk-reward ratio appear in the media. A clearer understanding of the impact of decision making is needed. An awareness of the impact of tolerated risk can be informed by the experiences of companies who have committed wisely to risk reduction and those that have not.
Leaders are more informed about emerging threats than ever, and have the opportunity to be proactive. Steps can be taken to increase transparency and better secure facilities. Even as lone wolf attacks and the impact of terrorist groups looms on the horizon, mitigations can be put in place to deter and improve facility responses to these emerging threats. Response actions must be tailored to the locale to increase their applicability and effectiveness. Disciplined operations can better deter criminals, can more easily identify breaches and can effectively report timely threats to law enforcement. Mitigations, contingency planning and mature procedures that are followed and reviewed with the appropriate periodicity can buy time during a breach event and protect all stakeholders while facility occupants wait for an effective response from local officials. Oftentimes overlooked, local law enforcement officials, or people with a law enforcement background, may be very helpful in mitigating the loss of life prior to or after a breach.
While a mature security profile may be difficult to achieve overnight, a reasonable rate of improvement should be expected. A security threat audit may be helpful in discovering the improvement opportunities present at any given time. These opportunities can then be costed, prioritized and implemented to reduce the overall risk profile of the facility.
Security Assurance
Security assurance is a continuous endeavor that must be pursued with rigor and discipline. Once organizational leadership has a good understanding of the threats within the scope of study, various simple mitigations can be deployed to immediately impact the security of the facility. Perpetrators can be denied access to water wells, electrical boxes and propane tanks. Lighting, signage and video surveillance can easily make a difference by illuminating key areas of the property at night better enabling the monitoring illegal behavior. Access can be denied through relatively simple traffic and visitor management.
In some situations, a mitigation task may be more difficult and prohibitively expensive. In these cases, the facility needs to focus on providing a response to the event should it occur as the facility may be dependent on external intervention. A strong relationship with local law enforcement officials and agencies is beneficial in these cases. The risk event could be a forest fire, an earthquake, an active shooter, a blizzard, avalanche, flood or a power outage. Depending on the location and the event, compounding factors may result. For example, if the road to the facility is blocked, keeping suppliers away or keeping employees trapped at the facility, there may be a delay in restocking of needed provisions. Additionally, there may be the need for an evacuation or the need for emergency vehicles to gain access in the case of serious injury or fire. The distance to the nearest hospital may also need to be taken into consideration. How the organization responds to these scenarios could be a matter of life and death.
Beyond physical controls, a suitable and robust set of operational procedures need to be a part of the organization’s employee handbook. The effectiveness of the procedures must be known. When procedures are coupled with documented drills, they can be tested and reviewed. The results of the drills should be documented so that further enhancements to the controls can be considered and implemented to mitigate weaknesses that have been discovered, or to improve on the execution of the procedures. The contents of the procedures may need to take into consideration, and accommodate, that fact that the response time from law enforcement or an ambulance may be longer than expected if the property is in a remote location. These factors, and many others, must be considered as part of the overall threat mitigation plan.
Risk Mitigation
The FMEA (Failure Mode Effects Analysis) tool is a well-known risk management tool. This tool can be used to reduce the risk profile of the facility. An example of some of the risk threats and their associated mitigations are shown in Figure 3. An annual review of the FMEA is necessary to help the organization keep up with both internal and external changes to the threat-scape. It allows for measurable and predicted outcomes that promote an evolutionary path for security within the scope being considered.
In this case, the FMEA has been simplified by excluding risk numbers. A more quantitative approach can be used if preferred. By using “low,” “medium” and “high” as a scale, or applying a traffic light tool, the facility leadership can easily reflect the associated risk level, as well as the impact of the mitigation, in the table. The perpetrators can be divided into two categories: criminal and non-criminal, as indicated in the left most column. The perpetrators are further broken down in the next column to the right. The list is localized based on the types of criminals that may be present in the area. The loss threat can then be listed along with the risk level at the point in time of the evaluation.
There may be evidence of the loss threat already on the property (ex. graffiti) thereby validating the data point. An on-site discovery process is beneficial. A new owner should ask people familiar with the history of the property about previous incidents or activities there. For example, it may be good to know if an underground fuel tank was ever installed as there may be leakage and ground water contamination. Additionally, insurance or law enforcement reports may be available that contain relevant information.
Moving to the right, the existing controls and their impact are listed next. A brainstorming activity with stakeholders, best practices from other locations, and input from local law enforcement may result in a good initial threat mitigations list. The community generally is interested in keeping criminal activity away. As a result, suggestions and assistance may be readily available from them if they are asked to participate. The impact of these mitigations on the potential risk threats are then listed. The projected impact of the mitigations listed can be assumed prior to implementation. This helps with prioritization if there is interest to impact the risk profile quickly.
In summary, the FMEA allows decision-makers to know what has to be accomplished to improve on the risk environment. It makes it easy to see who will be involved in and affected by each action. Decision-makers are able to quantitatively consider alternatives, prioritize and sequence actions. The tool provides a holistic approach by listing all known factors. This visibility also enables knowledge about combinations of threats or actions that may be dependent on each other. A baseline view is known as the current situation is made clear. Furthermore, a preliminary understanding of the influence of actions is documented.
Security Maturity
The improvement in the maturity of the security plan can now be reflected as the difference between the strength of the new mitigations as compared to the strength of the initial controls. In the event that the new mitigations are not meaningful or locally applicable, they will have a low impact on the overall risk profile of the property and may create a false sense of security. The organization leadership team will have to decide, based on the mitigation cost-benefit ratio, what mitigations to apply and in what order to influence the risk profile of the facility. The list of action items can be prioritized, approved and funded by camp leadership for implementation. A Gantt chart is a good project management tool to track the completion of each task on time and in the appropriate sequence. Tasks in the Gantt can be costed, timed and sequenced. Dependencies can be captured.
These fact-based tools can be used as a document of reference to influence decision-making and promote resource allocation to achieve the best result. Additionally, these living tools can track the effectiveness of decisions and be updated through iterative efforts to continuously reduce the potential for harm. Holistic tools create clarity in complex environments and keep risk form being moved around within the organization. The tools create consensus and unity around a common goal. These tools also challenge decisions that are made on “gut feel” and allow for broad input from all stakeholders. Empowerment encourages engagement and buy-in thereby increasing the chances of success. The overall goal of change is to reduce the chance of occurrence of harm or reduce the impact of a threat, should it occur. Aside from the probability that peace of mind can influence productivity, we must also consider that the security profile of our work environments may influence our physical, financial and emotional well-being.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




.webp?height=200&t=1724459676&width=200)
