Biometrics as a Convenience
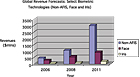
Let’s focus on implementation and adoption of fingerprint-enabled biometric solutions in the business world. The adoption of biometrics solutions has been primarily on physical access control and PC/network security applications in the business area. Adoption of more innovative solutions such as biometrically-enabled printers to secure confidential data is also beginning to take shape. Emerging application markets include biometrically-enabled transactional payment solutions and biometrically-enabled wireless devices for business use.
DOMINANCE OF FINGERPRINT
Fingerprint biometrics is the dominant biometric technology for business use. However, iris, face and increasingly voice verification biometric solutions have found niche applications markets as well. For example, a growing trend is the implementation of voice verification biometric technologies in financial institutions for remote access telephone services.PHYSICAL ACCESS CONTROL
Biometrically-enabled physical access control solutions are typically used to secure restricted access areas such as safe deposit lockers in banks. Regulatory activity in the United States, such as HIPAA compliance, has augmented the importance of finger-scan in healthcare institutions to protect patient data. In North America this has acted as a catalyst in the uptake of finger-scan in healthcare institutions in North America. For example, use of fingerprint-enabled solutions to access electronic medical records has resulted in increased activity in this vertical. Globally, implementation of fingerprint recognition systems for clinical data management is providing further impetus for growth. In addition, hospitals and surgical centers in Asia-Pacific are beginning to adopt finger-scan for physical access control systems in restricted areas such as Intensive Care Units (ICU).In addition, all geographic regions are beginning to experience high adoption levels of finger-scan for PC/network security applications, and will continue to do so throughout the forecast period. This is because of the need for higher levels of security to protect sensitive and confidential information. Use of finger-scan to secure access to drug development and clinic data trials is on the rise in all geographic regions.
LOGICAL ACCESS CONTROL
Corporate enterprises are beginning to use finger-scan authentication to secure corporate networks and prevent unauthorized access. Replacing IT systems that require employees to frequently change their corporate passwords by using fingerprint-enabled authentication is beginning to take shape. The main benefits of implementing finger-scan technology for a corporate enterprise include employee convenience of not having to constantly change and remember passwords, cost savings to the company from decreased password management, and improved corporate security.The use of fingerprint-enabled laptops, notebooks and IT peripherals such as mice, keyboards and USB flash drives is providing further momentum to growth. Major PC manufacturers have introduced silicon fingerprint-enabled laptops and notebooks since 2004. Demand is expected to grow significantly for fingerprint-enabled portable PCs throughout the forecast period. In addition, the development of finger-scan technology for applications such as online transactions in the medium to long-term are expected to pave the way for e-commerce activity. Innovative applications such as fingerprint authentication enabled secure online trading are in the nascent phase.
TRANSACTIONAL PAYMENT AUTHENTICATION
Biometrically-enabled payment solutions have forayed into the retail segment predominantly in North America and partially in Europe. North America is the most advanced in installing finger-scan enabled payment options and check-cash payment systems. Successful pilot projects have led to numerous retail stores implementing finger-scan technologies. Trials are being conducted in Europe and Asia-Pacific as well. The advantage of finger-scan payment systems for customers is the convenience of “paying with your finger” - the finger is linked to your registered account. For the retailer it results in reduced fraudulence and check-out queues. In specific stores there are loyalty programs in operation. The main benefit of a check-cashing solution is to lower fraud as verification of an individual ensures that the person says who they say they are before a payment is made.WIRELESS DEVICES
Fingerprint-enabled silicon sensors are the prevalent technology being integrated in wireless devices. Adoption of fingerprint-enabled cell phones is primarily being witnessed in South-East Asia, in particular in Japan and South Korea. This has encouraged mobile operators to introduce fingerprint-enabled cell phones globally but limited activity, has been seen so far. In addition, the release of fingerprint-enabled personal digital assistants that are more user-friendly and lower in cost compared to previous models is expected to increase usage from the business community.Increased penetration levels of biometrically-enabled cell phones are expected to raise confidence levels of both business and consumers to make payment transaction via cell phones. This is expected to pave the way for m-commerce activity.

In commercial applications, 3D facial readers such as this one from A4Vision and Premier Electronics Ltd. secure entrance areas of a building in combination with other security components of the installation. Speed and accuracy is a main requirement where an enterprise has high volume users.
Sidebar: Banks Bank on 3D Biometrics
Still new, three-dimensional face recognition is a modality of facial recognition methods in which the system uses the three-dimensional geometry of the human face.As a business or financial transaction tool, 3D face recognition can achieve significantly higher accuracy than its 2D counterparts by measuring geometry of rigid features on the face. This can overcome such pitfalls as change in lighting, different facial expressions, make-up and head orientation.
One approach: Implementing depth perception by projecting a grid onto the face and integrating video capture of it into a high-resolution 3D model.
Some European banks, seeking access control that operates completely without ID cards, keys or PIN technology, use 3D facial recognition of employees into bank buildings. Eliminating the risk of tokens and keys being lost, stolen or misused, this system uses only biometric verification methods with speed being a very important factor especially in the morning rush. At one European bank, 80 3D facial recognition systems are at entrances and combine with speed gates to ensure that there is no delay or hold up during peak times, especially in the morning when most of the 1,500 employees enter the building.
The 3D face recognition readers have been applied to physical access and time and attendance recording, too. The 3D facial recognition system directs structured, invisible light onto a subject''s face to create a facial grid of 40,000 measurable data points. Such systems perform multiple facial scans and comparisons against a database of stored images and corresponding data, performing accurate identification at sub-second speeds, from which authorized persons are confirmed for access.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






