RFID: Technology that Disrupts

Radio frequency identification or RFID will prove to be a disruptive technology for enterprises and their need to align security technology with their business goals.
Security applications including asset management and access control have been a traditional market for RFID technology. The early adoption of the technology enabled a significant evolution acclimatized to specific security applications. The percent of security applications in the total world RFID-based applications market is estimated at 33 percent according to Frost & Sullivan. The niche is expected to have a positive growth rate of 29.9 percent.
While the potential of the technology is quite evident, widespread adoption has been challenged by factors such as the cost of hardware, lack of standards, regional disparities of frequencies and investment, constant evolution of the technology and the need for upgrades. Apprehension centered on the security of tags represents a paradoxical situation since the fundamental rationale for RFID is to improve the efficiency of existing security applications. The challenge has, however, resulted in developmental efforts for in-built tag encryption and security features, thereby increasing end-user confidence.
High surveillance and security focused areas such as airports, embassies, military bases, laboratories, hospitals, museums, financial, educational and retail establishments represent high-demand RFID sectors. The basic feature of enhanced visibility and minimal human interaction extended by RFID systems complements the requirements of existing security markets.

Emphasis on homeland security
Homeland security concerns have been one of the biggest drivers for the growth of RFID. National security projects have driven widespread adoption and deployment in the wake of terrorist attacks in the United States and Western Europe. The largest RFID applications on the homeland security front center on aviation and documentation security.The business case for RFID is compelled by significant aviation security challenges with respect to logistics checks and explosive detection systems. Document security includes securing passports, visas, driving licenses and national identification cards. Large RFID pilots such as the San Francisco International Airport and the Hong Kong International Airport reflect the gaining popularity of RFID. Government-backed projects such as the National ID project in China and the use of RFID tags for certain documents in the United States hold promise for the accelerated adoption of the technology. Biometrics-based recognition modules also impact RFID with implementation of nationwide programs across the United States, Canada and all major European Union countries.
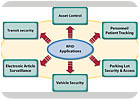
Exploring opportunities
The constant evolution of RFID into niche applications includes securing of currency notes. The European Central Bank, for example, has been proactive in experimenting with RFID to counter counterfeiting of Euro notes.There has already been an increasing trend of RFID for card access control applications. However, the cost of the technology is a significant impediment to widespread adoption among commercial security application markets. The trend of decreasing price levels is expected to phase out the challenge in the future. Price announcements towards the end of 2005 witnessed tag costs drop to approximately 10 to 15 cents for specific order sizes.
There is an increasing focus on integrating RFID with other data capture and wireless technologies to ensure a hybrid sensor-based network. Hybrid technology platforms increase the scope of existing security networks, enabling real-time track and trace applications. These security applications represent significant potential since there exists a stronger business case for item level tagging as compared to supply chain applications that are focused on the pallet and case levels. The interest evinced by major RFID participants such as Texas Instruments, Philips, Infineon, Transcore, Alien, Axalto, Gemplus and Savi Technologies mirrors such future potential.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




