Adding Security to Security Cameras

One of the most important requirements for Internet cameras is their ability to ensure a high level of security. The ability of such video streams to be transported over public, unprotected networks makes encryption critical in ensuring that only authorized viewers are allowed to see the images or control the camera.
Until recently, all security cameras were wired with coaxial cables carrying analog video signals in NTSC or PAL format. Each camera required the installation of an independent coaxial cable back to a security/monitoring station on premise.
The advent of the network camera1,2 offers the ability to connect IP cameras to an existing Ethernet local area network (LAN) infrastructure. The camera can even be powered using the same Ethernet cable using Power over Ethernet (PoE) technology3, thus eliminating the power cable and the requirement of a power outlet close by. The key advantage of the network camera, of course, is the fact that the video, audio and pan/tilt/zoom (PTZ) control functions can be accessed with equal ease from any computer on the internal LAN or remotely using the Internet. One or more storage servers connected to the LAN can provide archival storage and playback capability for the whole installation. The camera connection to the LAN can also be wireless, using standard 802.11a/b/g access points or routers.

For existing installations with analog cameras that need network access capability, video servers can be used to accept one or more NTSC/PAL camera inputs and provide a 10/100Mbps Ethernet LAN network interface.
Common selection criteria of network cameras are camera sensitivity, resolution, frame rate, compression technology and user interface features. But end users should not overlook the importance of security and protection of the camera, video stream and control link.
Analog cameras offer no capability to control authorization with regard to viewing the video output. In fact, for almost all of these cameras, the video output is always on and often quite easily tapped or substituted. The best way to guard against tampering with analog devices is through physical security measures. Further safeguards against unauthorized access are implemented at the head end monitoring equipment and/or video servers. However, hard-cable systems have one advantage in that any breach must also be accomplished physically and onsite.
Network cameras, on the other hand, must employ local intelligence, which provide a number of additional security measures. The video is digitized and compressed to Motion JPEG, MPEG2 or MPEG4 format. Control functions, including PTZ, are typically accessed using a Web interface with a browser. Since the viewer can be connected to the camera over the public, unsecured Internet, the camera itself must provide safeguards.
Cameras should be able to authenticate the source of the video and identity of the local or remote viewer, protect the confidentiality of sensitive video content using encryption, and guarantee the integrity of the video by ensuring that it has not been modified en route.
These security features can take advantage of one or more established protocols such as Secure Sockets Layer, or SSL, for a secure Web browser; secure Internet protocol, or IPsec, for transport; and Secure Real Time Protocol, or SRTP, for multimedia streaming. These protocols in turn are based on encryption standards such as Advanced Encryption Standard, or AES; Data Encryption Standard, DES or triple-DES; Public Key encryption standards; Message Digest, or MD-5; and Secure Hash Algorithm, or SHA-1. These security algorithms, in turn, require hardware cryptography acceleration in order to reduce the otherwise significant processor overhead.
Fortunately, cost-effective processors are now available that feature on-chip integrated security engines.
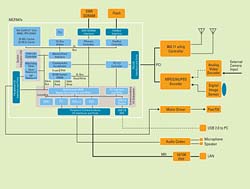
Security-enabled network camera
A block diagram of a network camera, based on the Freescale Semiconductor MCF547x ColdFire processor family, is shown in Figure 1.
The camera input can be from a CMOS or CCD digital image sensor, or an external NTSC camera. The analog NTSC camera input is first decoded and digitized into standard digital video format. The digital video is then compressed into Motion-JPEG, MPEG-2 or MPEG-4 format and transferred by DMA into the processor’s memory. A microphone or external audio input is digitized and compressed by the CPU using a software encoder such as adaptive differential pulse code modulation, or ADPCM. Audio output can also be implemented for intercom applications. The compressed audio and video streams are then packetized, optionally encrypted and sent over wired Ethernet or 802.11 wireless LANs.
Because the security risks associated with network cameras are electronic – digital rather than physical – most of their safety features are built into the device’s computer chip. Modern chip manufacturers offer numerous options. For example, the MCF547x features on-chip crypto engines that support DES/3DES/AES and ARC4 private key algorithms, MD-5/SHA-1/HMAC message digests and hardware random number generation. Its bus mastering capability utilizes the external high speed DDR SDRAM for fetching clear-text image and storing encrypted image output. CPU bus utilization protocols, as well as encryption keys, initialization vectors and audio compression/decompression data can be stored on the chip.
On-chip peripherals can include a PCI bridge, Fast Ethernet controllers, programmable serial controllers that interface to audio A/D-D/A, timers for controlling PTZ motors, high speed USB device interfaces that allow the camera to be used as a PC peripheral and other features.
The availability of new, integrated processors with crypto accelerators and enhanced security features can provide authentication, confidentiality and integrity of audio/video streams and control functions to finally ensure a degree of security necessary to make the network camera technology truly feasible. Certainly, as such systems gradually grow in popularity, network cameras will feature numerous security improvements. However, these collective capabilities are already ushering in a new generation of network cameras that can meet the security requirements of sophisticated modern and future applications.
References
1. “Network Cameras: Preparing Companies Move to Digital,” Fredrik Nilsson, Security Magazine, 05/08/2002
2. “Beyond the Camera,” John Mesenbrink, Security Magazine, 06/11/2003
3. www.motorola.com/files/analog/doc/support_info/ POWEROVERETHERNETHTML.htm?tid=tahs
www.motorola.com/coldfire
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





