So What Does Your CEO Think? Partner. Skeptic. Friend. Enemy.


The boss is Tinamarie Sauter of Mallory Alexander International Logistics. Her security executive is Douglas Durden, manager safety, security and asset retention. A global logistics company, the firm provides integrated transportation solutions to a wide array of customers. Its network extends worldwide and the diverse customer base ranges from hi-tech shippers in the electronic and medical fields to shippers of general commodities such as paper, lumber and cotton. Security sensitive, the firm also transports fine arts, including valuable paintings, sculptures and artifacts.

Sharing business goals -- Douglas Durden, manager safety, security and asset retention, and Tinamarie Sauter, vice president and chief operating officer at Mallory Alexander International Logistics based in Memphis, Tenn., see value in protecting the business.
“Since the unfortunate events of September 11th the two – business and security -- have found the same path. Security has become part of our daily transaction process including system upgrades and employee training to support changes to TSA regulations. Globally, we have committed to partnering with our customers and vendors to reduce supply chain risk through Homeland Security initiatives such as C-TPAT and FAST,” observed Sauter, COO and executive vice president.
SUPPORT FROM ABOVE
Durden knows the importance of support from above and the pressing needs of the business.“Management and I meet regularly or when needed to discuss current and future security topics. I explain to management what I can or cannot achieve with my resources. Management is then informed of risks the company faces for taking action and for not taking action in reference security matters. A course of action is decided,” said Durden. He works to accomplish business objectives. “Good open communication ensures that the company’s security program is focused on company needs and management expectations. That’s what I see as a security executive’s top responsibility.”
Untraditional corporate relationships also showcase the importance of the relationship between the top dog and the chief security officer.
In a business in Louisiana, Rick Hight and Alvon Blumfield, owners of the Louisiana Renaissance Festival, had to first overcome Hurricane Katrina before working with each other to solve security problems and upgrade the company’s security technology.
Located about 25 miles northwest of New Orleans, the executives evacuated the faire site taking with them all of their computers and equipment before Katrina hit. Then they waited. Rick Hight, who handles security as tech manager, co-owner and general manager, finally got to survey the damage. He said the damage was minor, just a few roofs, a backdrop, and scattered debris.

Held annually between November and December, the festival entices patrons with fine food, exciting activities, action-packed events and great shopping. However, as with most events open to the public, the Louisiana Renaissance Festival is protected by video surveillance. With over 400 on-site workers and thousands of patrons through the duration of the event, packages began disappearing from the mailroom, and the Louisiana Renaissance Festival committee – at the urging of Hight and with the support of Blumfield, decided to implement a PC-based surveillance system.
The two executives worked together and their goal was much closer to crime prevention than business expansion.
No matter if the CEO team is big business or entrepreneurial, there is always a give-and-take between the chief security officer and the CEO or COO. In research by The Conference Board, Security Magazine and Maddry Associates, such relationships can shift among partner, skeptic, friend and enemy. What has emerged is the crucial need for security to make a strong business case for security to top corporate executives.

COST CENTER MENTALITY
According to a special Conference Board report authored by Thomas Cavanagh, security has traditionally been seen by corporate CEOs, COOs and CFOs as a cost center that contributes little or nothing to the profitability of the core business. “Making a business case for security expenditures has been one of the most difficult aspects of the corporate security function,” reported Cavanagh.A survey of top executives conducted by Maddry Associates for Security Magazine – when compared to a same-time survey of chief security officers conducted by Security Magazine’s BNP Media Research operation, found a sometimes disconnect between the CEO’s business focus and security’s operational focus. The differential is closing, however.
The Conference Board found that results of its survey reveal the centrality of risk in making the business case for security. Senior executives give most weight to security concerns on issues of operational risk, such as compliance and certification. Still, much less weight is given to security on strategic issues, such as competitive advantage, brand management, and growing new lines of business.
There is a warning in The Conference Board report, according to Cavanagh. In general, the most supportive executives were not the most influential, and the most influential executives were not the most supportive. As a result, some security directors appear to be politically isolated within their companies, facing a challenging search for allies when they need to gain support from upper management for new security initiatives.
Douglas Durden works the team at Alexander International Logistics to solidify strategies. “After policies and procedures are decided and agreed upon by management, presenting new polices and procedures to the company may require more than just my input. I work with a small team of co-workers to assist with the final product – Charlotte Patterson (Quality Control Manager), Mary Beth Couch (Compliance Analyst), Melzie Wilson (Compliance Manager), or Rusty Winfield (Global Transportation Manager), as examples. We have security guidelines to follow nationally and internationally. Having the above individuals as a resource of information to tap into need to pays off,” said Durden.

DON’T FALL FOR TECHNOLOGY
Durden added, “Technology is just another layer of security. The first layer of security is security trained, educated and dependable employees. Before adding technology, security executives should ask themselves how will this help me with my security situation, what are my options, do I need it right now or can it wait? If you determine that new technology is needed then know what you want it to do. You can buy a horse (fast but won’t last long), or a mule (slow but will last forever).”Agreeing with Durden, the Maddry Associates and Security Magazine surveys found that chief security officers gain political points when aligning with in-house colleagues and especially compliance and the information security function, areas that more CEOs see as essential to business continuity.
When The Conference Board asked executives asked how effectively their company’s security was aligned with their company’s business objectives, the most effective alignment was found on issues of operational risk, such as complying with government regulations (cited by 79 percent), protecting confidential information (74 percent), meeting certification standards (72 percent), and maintaining business continuity and ensuring customer safety (71 percent apiece). Limiting financial risk (62 percent) and defending against litigation (60 percent) were also viewed as areas where security was effectively aligned with corporate functions

Alvon Blumfield and Rick Hight, owners of the Louisiana Renaissance Festival, had to first overcome Hurricane Katrina before working with each other to solve security problems and upgrade the company’s security technology.
Metrics is a solid way to overcome objections and skepticism.
For CEOs, COOs and CFOs, the most useful metrics are those which enable these executives to determine how much a security problem will cost the enterprise in terms of liabilities or foregone business. From The Conference Board study, reinforced by the Maddry report, the most helpful metrics are the cost of business interruption, cited by 64 percent of executives, vulnerability assessments (60 percent), and benchmarking against industry standards (49 percent). Another group of helpful metrics are explicitly related to insurance costs, such as the value of facilities (mentioned by 44 percent), the level of insurance premiums (39 percent), and the cost of previous security incidents.
"Reducing risk can never hurt." Said Durden, “I evaluate and treat our loss exposures and develop plans to prevent it. Solving today’s security concerns will require knowledge as well as imagination - thinking outside of the box sometimes for answers. Pre 9/11, we were concerned about terrorists taking something out of containers. Post 9/11, it’s putting something inside containers. Mallory Alexander can and will with the support of upper management, knowledgeable managers, security smart employees and security minded customers/agents be better prepared for future security concerns. I want to do what all chief security officers want to do for their companies - save lives by doing our jobs, protect property, protect product and enforce government security regulations the best we can.”
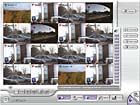
A PC-based security video system proved to be the Louisiana Renaissance Festival’s knight in shining armor. A hybrid surveillance DVR solution allows users to incorporate both analog and IP cameras with their system.
SIDEBAR: Business Knight in Shining Armor
Just imagine, medieval knights battling in the courtyard, kings and queens overseeing their subjects, jugglers performing, fire-eaters, sword fights and incredible food and drink, all that a renaissance festival should be. The Louisiana Renaissance Festival is not much different, offering an authentic medieval experience with Louisiana flair. Held annually between November and December, the festival However, as with most events open to the public, the Louisiana Renaissance Festival is protected by video surveillance. With over 400 on-site workers and countless patrons through the duration of the event, it is impossible to monitor suspicious activity with the human eye alone. Packages began disappearing from the mailroom, and the Louisiana Renaissance Festival committee decided to implement a PC-based surveillance system.A PC-based surveillance DVR proved to be the Louisiana Renaissance Festival’s knight in shining armor. AverMedia’s NV3000 is a hybrid surveillance DVR solution that allows users to incorporate both analog and IP cameras with their system. Each NV3000 card includes four channel video inputs, stackable up to four cards. The Louisiana Renaissance Festival currently has one PC containing four cards enabling 16 active cameras. Each camera has been placed in key surveillance locations, including the mailroom and the entry gate where images of every car’s license plate entering the facility can be recorded.
Remember the missing packages from the mailroom? The new surveillance system was able to capture video of a driver from one of their primary delivery companies stealing a package sent by a jewelry vendor. The clarity of the video as well as the ability to quickly search and find the event were key to solving the issue. The remote monitoring capabilities allowed users to access live surveillance and playback events from any Explorer browser or Web-enabled PDA.
The Louisiana Renaissance Festival plans to add another four cards to a separate PC, providing the ability to monitor 32 cameras simultaneously.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





