Migrating to IP – Phasing In

A full IP solution may not be an immediate bottom line approach so plan a migration path.

IP transmitter/receiver modules transmit compressed
image data over the network.
How can enterprises take full advantage of this emergent technology without throwing away existing investment in installed systems?
Looking at the disadvantages of analog security video can best highlight the advantages of IP video. Traditional coax- or fiber-based video systems are limited in many ways. Installation costs over large areas are prohibitive and the number of monitoring stations is limited due to the investment required to replicate costly switching infrastructure. The analog matrix is the component that provides control room flexibility for analog security video systems, but this too cannot be easily expanded without adding new hardware and it is location dependent. Therefore overall scalability is limited.
Even though digital video recorders (DVRs) improved the recording capabilities of analog security video, it still has limitations. Businesses want a single, scaleable, integrated solution that provides high-quality video surveillance across any number of offices or sites – and this is what IP video delivers. With an IP-based solution, there is no need to worry that any future expansion will reach the capacity limit of the installed hardware; additional devices, such as cameras, monitoring stations and video recorders, can be incorporated at any point on the network at any time. The latest IP video systems use advanced compression technologies that enable DVD-quality digital video, with low latency that is indistinguishable from traditional analog. The extent to which a business might want to change to IP video is dependent upon the application, but typically it is when additional cameras, monitoring stations or recording capacity are required for an existing system, or when a number of systems on different sites are to be merged.

A typical networked video system simply requires a PC
platform and disk storage.
Planning Migration
A solid strategy, and one CEOs often appreciate, is to involve the IT department at an early stage in the planning process. Competent IP video products now feature much of the functionality with which IT professionals will be familiar, such as Simple Network Management Protocol (SNMP) for management purposes, integral firewalls, bitrate capping and diagnostic programs. These all ensure that the IT team can maintain full control over the network traffic generated and monitor system performance, and to simplify troubleshooting should difficulties arise. A properly planned migration is best undertaken in phases and can be contiguous or as demand and budget allows, thereby allowing for each phase to be “proven” before moving to the next. This has the additional benefit that older equipment can be retained and fully utilized until continuing support for it becomes costly or otherwise impractical. The migration process can be stopped or delayed at any point and the system continued with a hybrid setup.
IP alarm panels allow integration to other security systems
such as intrusion detection and access control.
Take a simple hypothetical example.
A system on a site has a mixture of 150 cameras, both static and PTZ. It has an Operational Control Center (OCC) with two operators and is conventionally equipped with a hardware-switching matrix with DVRs continuously recording all cameras. IP transmitter/receiver modules transmit MPEG-4 quality digital video, audio and control data over the IP network. The typical networked video recorder (NVR) solution simply requires a PC platform and hard disk storage. However, for more demanding fault tolerant applications, NVRs can in standalone units with removable hard disk drives.IP alarm panels allow inputs and outputs to be easily connected to the network for interfacing other security systems such as intruder detection and access control. In this example, the system needs to be expanded, following such requirements as:
- 50 cameras need to be added to the existing system.
- A monitoring point in the OCC needs to be installed for a further operator.
- Two of the organization’s managers want live views of selected cameras at their desks.
- Some additional security measures need to be installed at a remote car park.
- The site has an existing corporate LAN (Local Area Network).
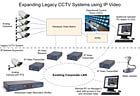
Phase ONE: Main Site
Because of budget constraints the existing matrix, operator stations and DVRs will be retained. Connecting new cameras into the system using the existing LAN rather than running dedicated coaxial and PTZ cabling from the matrix out to each camera location will create savings. Using IP transmitters (encoders) will allow complete freedom of camera choice. The additional cameras will be connected into the LAN via a transmitter, and the corresponding IP receivers (decoders) for each camera will be connected to unused matrix inputs at the OCC. The matrix outputs will be connected to further IP Transmitters, putting the existing OCC video feeds on to the LAN. PCs with monitoring software for the additional operator in the OCC and for the desk PCs of the two managers will be added.The system will configure to restrict access, ensuring that the managers are only able to access the cameras that they are authorized to view. The additional cameras will need an expanded recording capability. NVRs will be added to meet this requirement. Since this element, like all the others in an IP solution, is totally scaleable it frees the user from the constraints of simply expanding the existing DVRs. Using NVRs gives the user access to recorded video from anywhere on the network.
Phase Two: Car Park
IP cameras, help points, lighting controls and a barrier with a speech unit for visitors will be installed, providing additional security measures for the car park. In addition, access control for employees will be introduced, which is capable of being remotely operated or overridden from the OCC. To save on cabling costs and to get across the approach road a small, secure 5.8GHz wireless network will be used to connect all of these devices across to the main building and to extend the LAN. All devices and functionality will be controllable from the OCC, and from the same PC software used for monitoring.Phase Three: Full IP
The project has made full use of the original security video equipment up to this point; but when budgets become available migration to a full IP system can occur. This is justified on the basis that the maintenance of the matrix becomes more problematic with age, the recording capacity of the DVRs becomes increasingly inadequate and the user sees the many operational benefits from the developing IP video system.The original hardware matrix will now be removed, with the LAN and monitoring software becoming the so-called virtual matrix. An IP transmitter will be installed to each of the original cameras making them IP compatible. As the cameras are already cabled back to a common point at the main OCC, rack mounted IP transmitters will be used, resulting in a typical cost saving of 10-15 percent over standalone units. The IP transmitters and receivers connected directly into the matrix will be reused to connect some of the analog cameras to the network.
This example shows how easy it is to migrate an existing analog system to an IP solution. Even though it is a hypothetical issue, it is very typical of many applications. The progressive nature of the migration allows existing budget constraints to be accommodated and allows each phase of the project to be thoroughly tested; the user can be confidence that IP based security will meet the project requirements. Overall costs are kept to a minimum because significant parts of the existing security video infrastructure are re-used and future expansions can easily and inexpensively be added.
About the Sources
Security Magazine thanks Oliver Vellacott of IndigoVision and Dan McGinley of i3DVR International for material appearing in this article. More information on IP-based security video and migration and integration strategies, check out the LINX search tool, powered by Google, on the Security Magazine Web site at securitymagazine.com.
SIDEBAR
Business Strategy: Leverage Existing Equipment
A major drawback of IP video security solutions is that they fail to address those businesses that have heavily invested in analog components. What’s more, they fail to consider technology cycles that must realize a breakeven point in return on investment, observed Dan McGinley of i3DVR.Rather than advocate full-blown IP solutions, a solution can allow chief security officers to leverage existing equipment while gradually migrating from analog to IP. A true hybrid solution would represent the best of both worlds, both a reliable, real-time video system and viewing access to remote locations across the network. At any time, the operation could begin upgrading the network and add channels incrementally, recording their analog cameras while adding IP cameras and encoders at whatever pace desired.

Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!



