Product Spotlight
Security technology: Mobile security solutions

In an increasingly mobile and remote workplace, mobile security solutions can help organizations become more proactive by managing, identifying and responding to security threats from the palm of their hand.
Security magazine highlights mobile security solutions, including video surveillance, access control, lone worker protection, healthcare safety, emergency response and more.
Arcules
Centralized Security Management of All Locations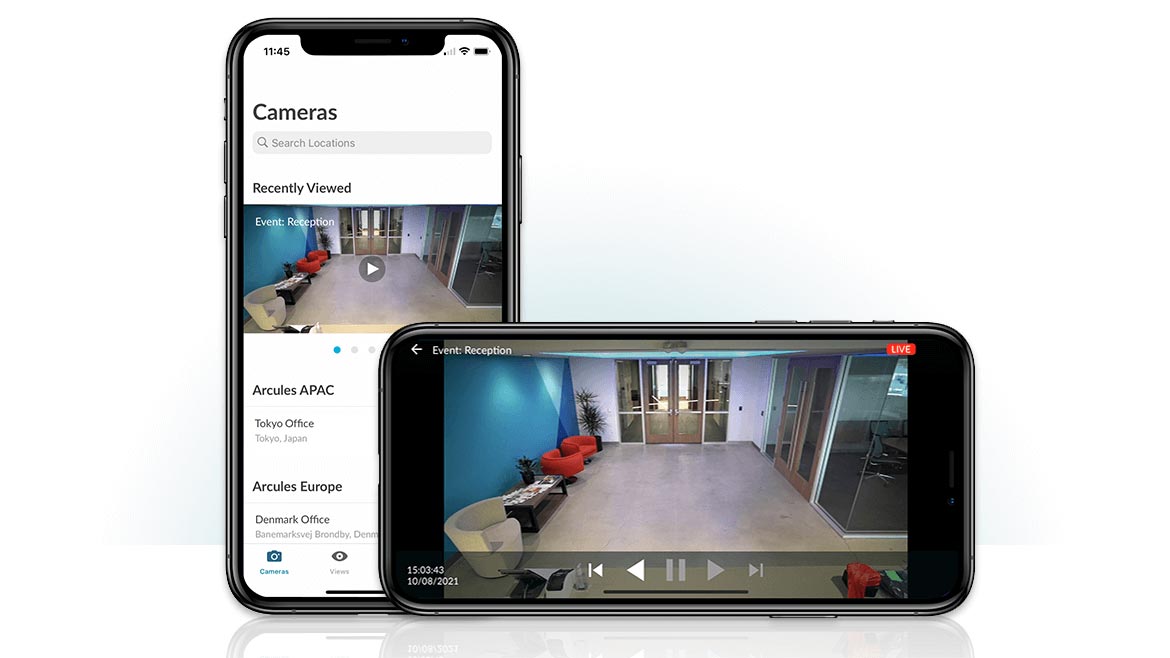
Arcules Unified Cloud Security Platform, a Video Surveillance as a Service (VSaaS) platform, is available via a mobile app. From the app, users can view security cameras, monitor live video and play footage from any device. Whether working from home, on vacation or away from the office, users can get notified of security events, from doors left open to environmental issues, and act on potential security incidents. Users can customize settings to receive notifications for important events and tap to view alarm events from a push, SMS or email notification; access personal and shared camera views; and view cameras by location. Image courtesy of Arcules
Find out more at www.arcules.com
Avigilon
Remotely Connect to Video Surveillance Feeds
 ACC Mobile 3 extends Avigilon Control Center (ACC) video management software to mobile devices, allowing security professionals to monitor ACC systems and respond to incidents from any location with network connectivity. The ACC Mobile 3 app provides remote access to cloud-connected ACC sites, alleviating the need for firewall configuration. With the ACC Mobile 3 app, users can sign in for access to an organization’s cloud-connected sites; view live or recorded video; stream live or recorded HD video; receive push alarm notifications to detect, verify and act on events such as motion or video analytic rule triggers; and review recorded video using the recorded video timeline. Image courtesy of Avigilon
ACC Mobile 3 extends Avigilon Control Center (ACC) video management software to mobile devices, allowing security professionals to monitor ACC systems and respond to incidents from any location with network connectivity. The ACC Mobile 3 app provides remote access to cloud-connected ACC sites, alleviating the need for firewall configuration. With the ACC Mobile 3 app, users can sign in for access to an organization’s cloud-connected sites; view live or recorded video; stream live or recorded HD video; receive push alarm notifications to detect, verify and act on events such as motion or video analytic rule triggers; and review recorded video using the recorded video timeline. Image courtesy of Avigilon
Find out more at www.avigilon.com
Brivo
Keyless Entry With Mobile Access Control
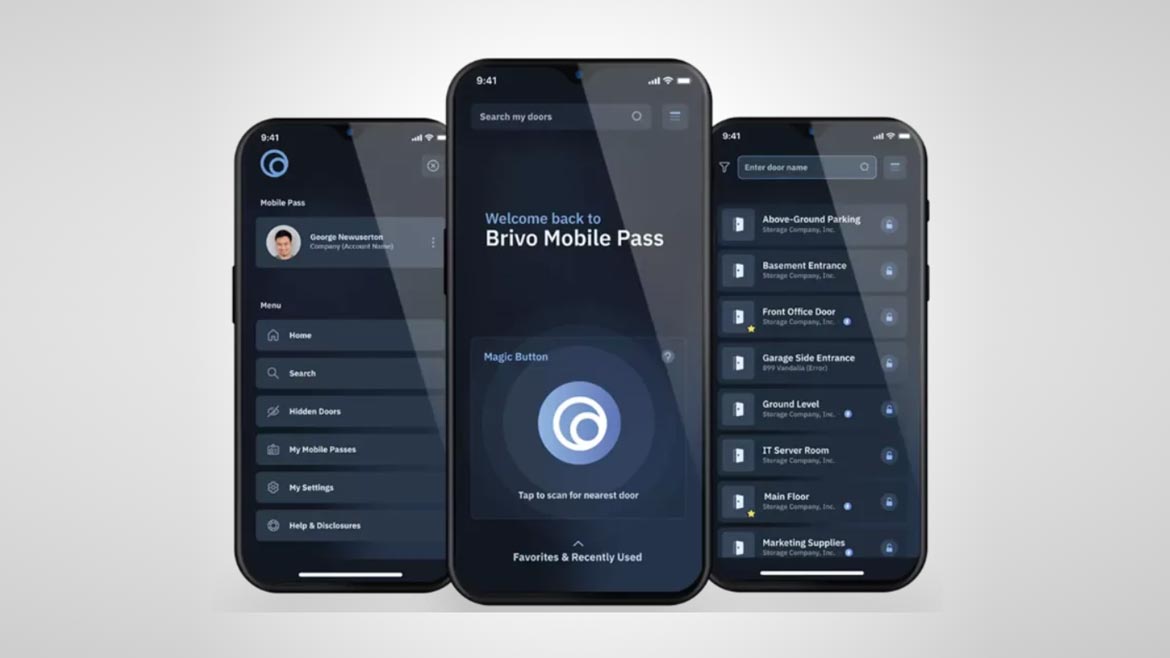 The Brivo Mobile Pass provides tenants, employees, residents and guests with an easy way to unlock connected doors. Property managers can use Brivo mobile access control management to grant necessary access and control the property. The app utilizes device biometrics like fingerprint and facial recognition for additional security. In addition, users can customize a health questionnaire to monitor and record the health of visitors before they enter the facility. The app features Brivo Onair Management, which allows users to remotely control access, assign and remove credentials, view access events, and lock and unlock doors. Image courtesy of Brivo
The Brivo Mobile Pass provides tenants, employees, residents and guests with an easy way to unlock connected doors. Property managers can use Brivo mobile access control management to grant necessary access and control the property. The app utilizes device biometrics like fingerprint and facial recognition for additional security. In addition, users can customize a health questionnaire to monitor and record the health of visitors before they enter the facility. The app features Brivo Onair Management, which allows users to remotely control access, assign and remove credentials, view access events, and lock and unlock doors. Image courtesy of Brivo
Find out more at www.brivo.com
Cobalt Robotics
Enterprise Mobile Video Chat for Robots
Cobalt Robotics’ enterprise mobile video chat allows enterprises to connect staff and visitors with a live employee from the organization or security team, or a backup from Cobalt’s Command Center. Each robot has a screen for communication between remote security specialists and people onsite. The Robotics as a Service solution includes more than 60 sensors, including day-night cameras, 360-degree cameras, thermal cameras, depth cameras, light detection and ranging (LIDAR), and badge reading capabilities. Over time, the autonomous patrolling robot can help organizations facilitate data collection throughout a facility to help get insights into security, safety and facility trends. Using machine learning, semantic mapping and novelty detection, the robot can identify and flag security-relevant anomalies such as people, sounds, motion, open doors and windows, and missing assets. Image courtesy of Cobalt Robotics
Find out more at www.cobaltrobotics.com
EVERYWHERE Communications
Helps With Remote Worker Safety and Duty of Care
EVERYWHERE Communications’ software check-in capabilities can help monitor remote personnel who are in and out of cell coverage. Scheduled Check-ins give administrators the ability to tailor check-ins on an hourly, daily, weekly or monthly basis to address the unique needs of remote personnel and help simplify the duty of care process. Remote Check-ins allow personnel to create their own check-in recurrence directly when paired with a Garmin inReach device with EVERYWHERE software. If an unexpected situation occurs while outside cellular coverage, remote personnel can feel confident that their safety is being monitored even if they miss a check-in; initiate a new check-in schedule; or send a “not safe” report that triggers an alert and multi-channel notifications via SMS, email and automated voice call. Image courtesy of EVERYWHERE Communications
Find out more at www.everywherecomms.com
Interface Security Systems
Offers Personal Protection Monitoring Services
Interface Security Systems’ expanded suite of Personal Protection Monitoring services uses active radio frequency identification (RFID) tags from GuardRFID to protect infants from abduction, prevent mother/infant mismatches, and monitor memory care patients in healthcare environments. The expanded suite includes an infant security system for newborn infants in birthing centers and hospitals to prevent abductions and accidental pairing of the infant with the wrong parent and a management system for patients in hospitals, behavioral health facilities and memory care centers. The solution is deployed with GuardRFID’s RFID active tags and locating systems and integrated with onsite alarm systems and video cameras to provide alarm management and video verification of alarm events. The solution can be used to protect at-risk lone and mobile workers in retail, restaurant and hospitality brands. Image courtesy of Interface Security Systems
Find out more at www.interfacesystems.com
LenelS2
Access Control and Video From Mobile Devices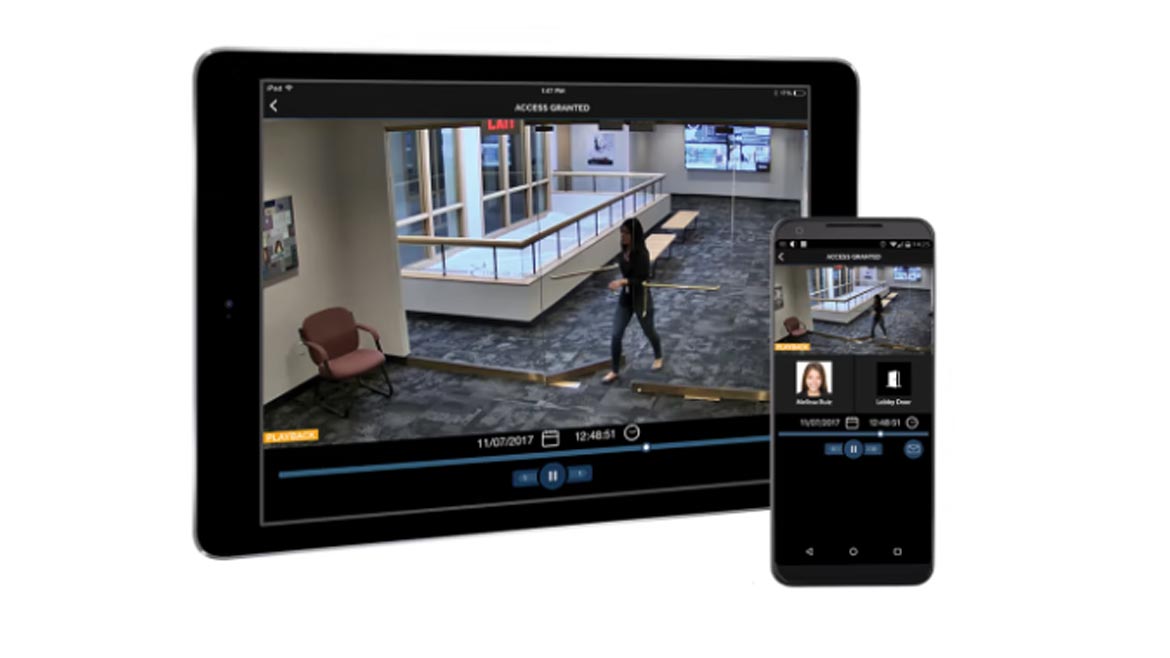
LenelS2’s Mobile Security Professional is an app for iOS and Android devices that allows both management and staff to operate access control and video management systems from anywhere. Users can switch between separate systems or partitions directly in the app. Mobile Security Professional is administered from a central location, and security actions are displayed at the command center. In addition to delivering live video and event-based video recording from LenelS2 VRx or NetVR cameras, the app allows for sharing of images via email or text message, displays event activity and video of interest, enables momentary unlocking of any door in the system, tracks evacuations, allows for management of multiple mustering points and more. Image courtesy of LenelS2
Find out more at www.lenels2.com
Resolver, a Kroll Business
Bolsters Security Operations Management
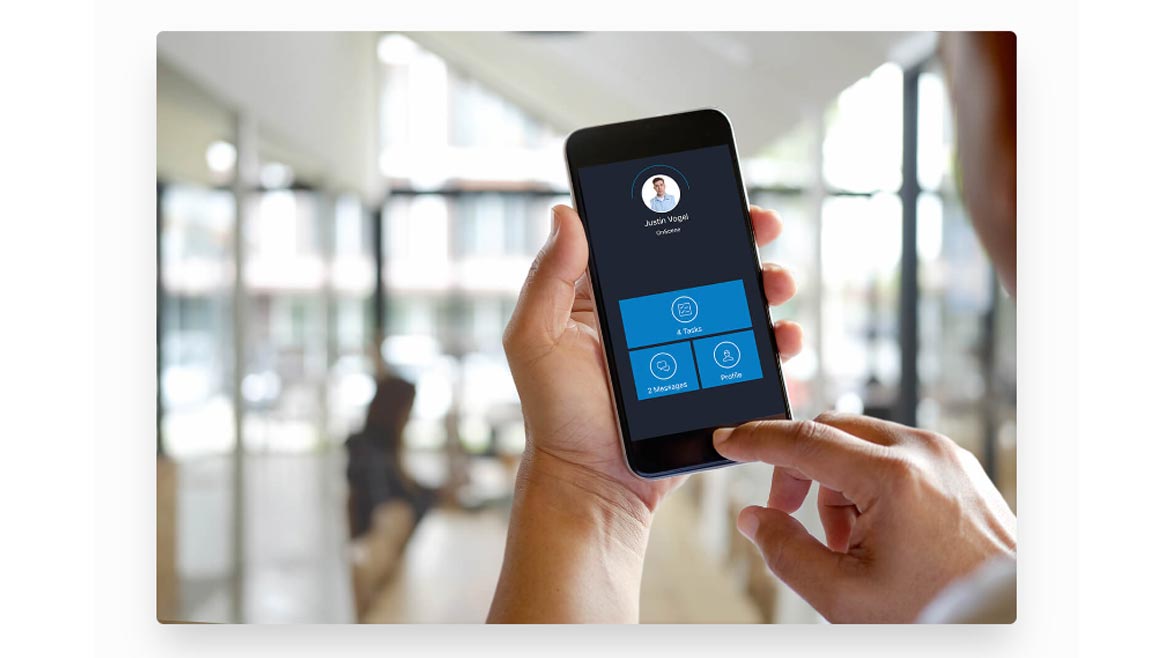
Resolver’s Command Center combines alarm management, computer-aided dispatch and incident reporting. The application allows users to plot alarms, incidents and guard locations onto real-time maps to see which personnel are available for incidents. Resolver’s Command Center is available on the Resolver Officer Mobile app for iOS and Android and allows security teams to connect dispatchers directly to officers and share dispatch details, locations and standard operating procedures to manage organizational safety. The Officer Mobile app also provides security officers with tools to respond to critical events, follow procedures and document incidents via their mobile devices. Image courtesy of Resolver
Find out more at www.resolver.com
Silvertrac Software
Streamlines Security Officer Operations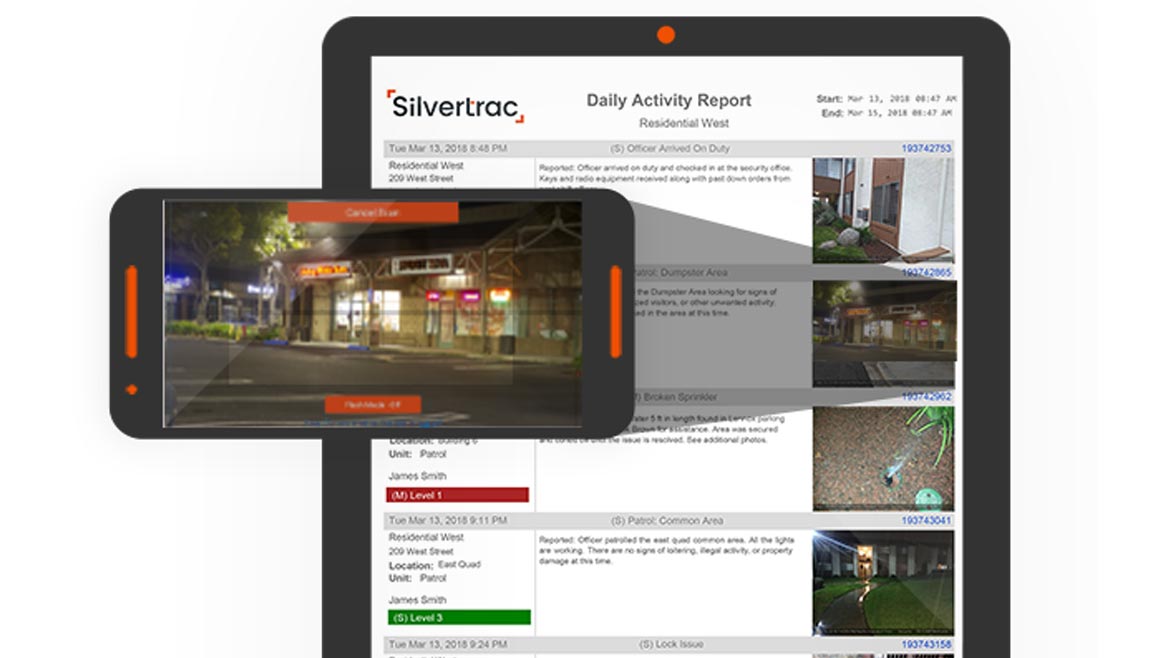
Silvertrac’s security guard management software includes a mobile guard app that guides officers on patrol throughout each shift via digital checkpoints and can be set up across multiple properties through the Issue Monitor. In addition to enabling officers to scan checkpoints using QR codes, barcodes or NFC tags, the app can send instructions to the phone for each hit; log GPS and time-stamp on each scan; show time left before each tour is due; and cross out each checkpoint as it happens. The Issue Monitor gathers scanned checkpoint data from the field and prepares daily activity and incident reports. Image courtesy of Silvertrac Software
Find out more at www.silvertracsoftware.com
Trackforce Valiant
Increases Security Guard Performance and Protection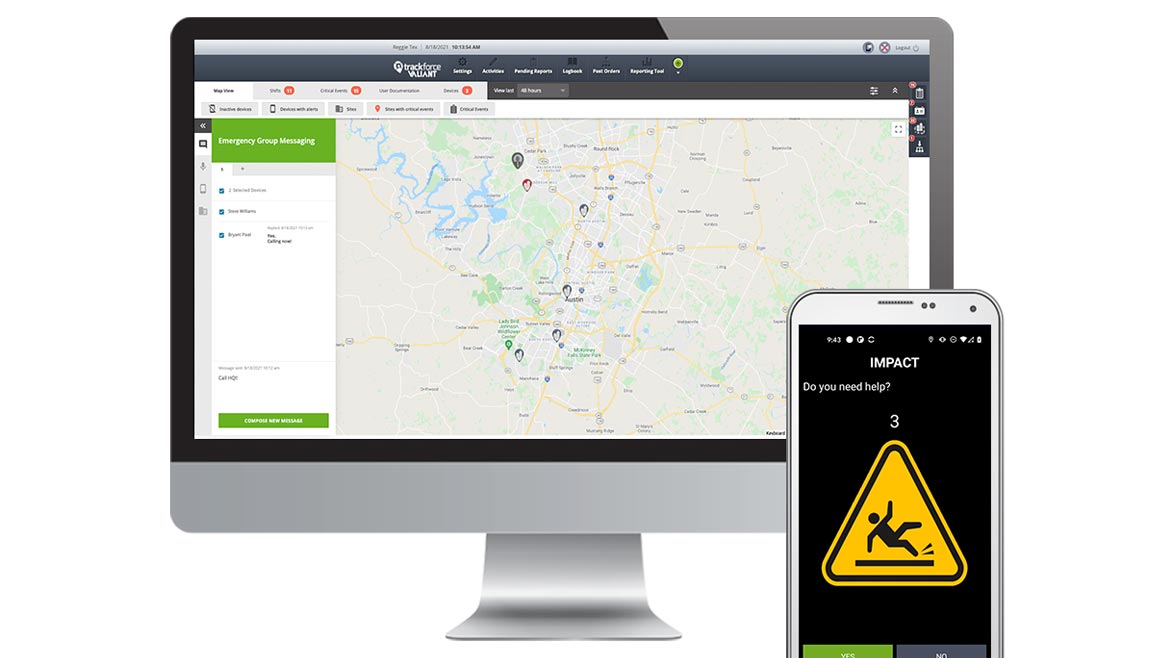
The Trackforce Valiant Guard Tour app is a configurable solution that enterprises can use to help conduct tours and patrols for security operations. The application, part of Trackforce Valiant’s guard management solution, can provide operational insight into a guard’s tasks during their shift and helps security teams stay focused. As guards conduct tours, for example, they are guided through daily tasks via the app, including post orders, logbook history, checkpoints and shift information. In addition, the app enables lone worker protection with manual panic alarms, true fall detection, phone tilt detection technology to indicate an emergency or requested assistance, and a danger zone timer to indicate a safe amount of time before assistance is required. Image courtesy of Trackforce Valiant
Find out more at www.trackforcevaliant.com
TrackTik
Tracks Frontline Security Teams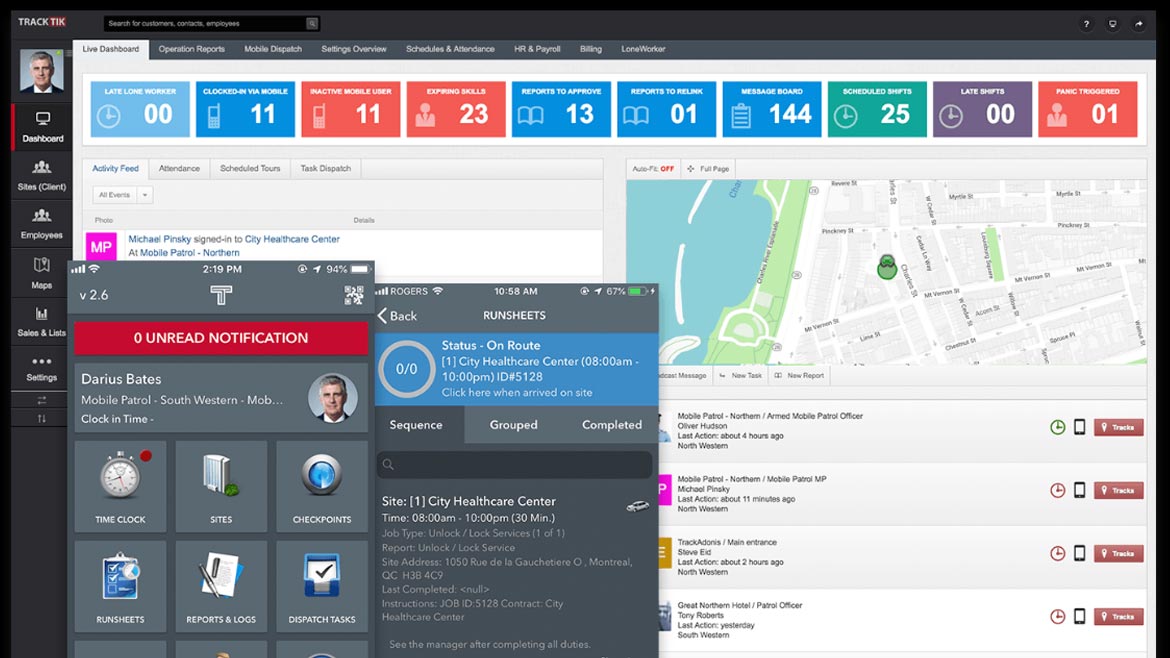
TrackTik Guard Tour is a mobile and web-based software that can connect field personnel to management and clients through a suite of guard management tools and business intelligence modules. The TrackTik Guard Tour module enables users to look at operations and develop a security strategy that maximizes the value delivered to stakeholders. Working with stakeholders, users can identify their most valuable assets and tailor guard tours accordingly. In the app, users can define what happens at each checkpoint for a security officer, including logging, displaying a message, opening a report form, asking exception questions, or triggering incident alerts. The mobile support is compatible with iOS and Android and works using a variety of checkpoint types such as NFC, barcode, QR code, Aztec, GPS and manual check-ins. Image courtesy of TrackTik
Find out more at www.tracktik.com
911inform
Benefits First Responders During Critical Events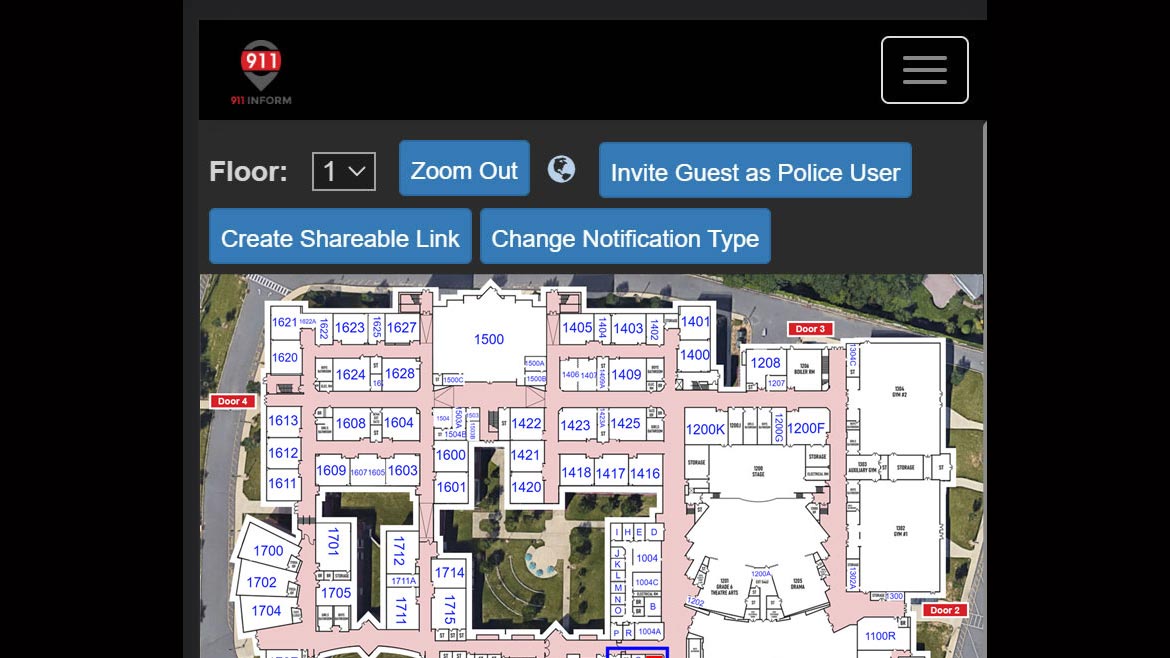
911inform is a notification and emergency management service that provides police dispatch, first responders and key building personnel with bi-directional communication and controls to manage a crisis situation. The app can be implemented across a range of industries, including hotels, malls, schools, hospitals, municipalities and large public spaces. The solution leverages location technology from mobile devices to designate a pre-configured area, or geofence, to alert predefined parties with incident intelligence in the event of an emergency. First responders do not have to download new applications or software on their devices; they can open a one-time access link to launch the event interface. End users can customize and determine how to share data with public safety answering points (PSAPs), private security and/or relevant facilities personnel. Image courtesy of 911inform
Find out more at www.911inform.com
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







