Integrated Solutions
Building access control for a safe, stress-free campus post-COVID
With the right modern access control solution, campus security can access innovation, streamline processes and enhance campus safety beyond the pandemic.

Tashi-Delek / E via Getty Images

Despina Stamatelos. Image courtesy of Stamatelos
Ensuring a safe and stress-free environment at higher education campuses has always been a challenge. When the COVID-19 pandemic began in early 2020, things became even more difficult.
For colleges and universities, striking a balance between securing buildings and spaces while allowing students and staff to freely move through campus wasn’t enough anymore. As mass lockdowns and social distancing requirements came into effect, security professionals at higher education campuses were forced to adapt quickly, restricting building access to an as-needed basis, enforcing and monitoring new occupancy limits in buildings, and ensuring everyone adhered to safety protocols.
To fulfill developing health mandates and keep students and staff safe, many security teams relied on existing access control technologies. But as new regulations came out and building access policies changed, some higher education security professionals faced an all-too-familiar reality: their legacy access control systems weren’t designed to keep up with these modern-day problems.
Higher education security leaders looking to invest in access control technology can employ the following criteria during their search, and discover tips on how to maintain safety on their post-COVID campuses into the future. We’ll also share some key features to help all campus security teams build a safer, stress-free environment for students and staff in a post-COVID world.
How COVID-19 Put the Spotlight on the Limitations of Legacy Access Control Technology
In the past, security professionals across higher education facilities dealt with the system limitations of legacy access control solutions in the best ways they could. While some conceded that controlling doors and cardholders was enough to keep a campus secure, others found workarounds or waited for budget increases to make small upgrades here or there.
No matter the strategies for managing legacy access control equipment, the COVID-19 pandemic showed campus security teams just how much those older solutions were holding them back. Disjointed and closed systems kept them from implementing tools to better track occupancy levels or remotely adapt door schedules and cardholder privileges. Older proximity cards and touch readers created vulnerabilities and could be difficult to manage and access across multiple sites.
Now, looking ahead at a post-COVID world, many higher education facilities are ready to make changes. They want to move forward with greater ease and adaptability and invest in access control solutions that help them remain proactive as regulations and campus life evolve.
Why Open and Scalable Access Control Solutions Help Campuses Move Forward
Upgrading a higher education access control system doesn’t happen overnight. It’s a big undertaking, and that alone can dissuade many universities and colleges from moving to newer solutions. The key is to invest in a modern access control solution that allows for a phased implementation. Typically, this requires two critical features: openness and scalability.
With an open-architecture access control solution, security professionals may keep some access control technologies and implement a new software solution to manage cardholders, devices and information. This gives them access to more modern capabilities which help operators streamline day-to-day tasks while reducing the total cost of ownership.
Later on, as more budget becomes available, campuses also get the flexibility to phase out older technologies and implement newer solutions such as touchless readers, mobile credentials, biometrics and more.
Where openness provides broader access to the latest innovations, scalability allows a security team to upgrade access control with one system, building or campus at a time. This means a security team can easily pilot a new solution before full-scale deployment or simply upgrade the most critical sites first.
Opting for a scalable solution will also support the unique requirements of an expansive higher education campus where devices and cardholder numbers can often reach hundreds and thousands, enabling fluctuation and future expansion.
Tools for Managing Access Control and Occupancy in a Post-COVID World
With an updated access control system, security teams can begin taking advantage of solutions that streamline workflows and processes, better address COVID-19 protocols, and improve the flow of movement on campus.
For instance, a security team could extend a modern access control solution with a physical identity and access management (PIAM) system to automate access requests and heighten compliance.
Instead of manually managing temporary access to secured areas, a PIAM system allows users to assign access rights based on roles, attributes, departments or specific security policies. Should internal policies or regulations change, users can modify which groups can access certain buildings or areas.
The PIAM system further simplifies access requests from staff, students or visitors to various areas on campus. For example, should a faculty member invite a guest lecturer into a specific class, they can make that request using a web-based application to ensure the guest gets temporary building access.
Everything from the initial request and the vetting from decision-makers to the granting and de-activation of rights can be automated through the PIAM application. All user activity is also logged, which further strengthens security and accountability.
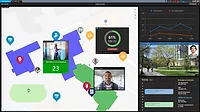
With a modern access control solution, security teams and facility managers can also take advantage of occupancy tracking reports to manage COVID-19 protocols and boost compliance.
Staff can use modern access control systems to track individuals or count people in certain areas without compromising privacy. They can then monitor live data to see what’s happening in real time or set occupancy thresholds within the system. They can also receive notifications when threshold limits have been reached in the cafeteria, library or gym and quickly restrict more people from entering these areas to abide by regulations.
Three More Ways to Reduce Touchpoints and Enhance Safety Across Campus
Upgrading access control is the first step to becoming more adaptable to changes in the higher education environment. It removes barriers to innovation and allows security teams to remain agile and evolve their risk mitigation and access strategies as needs arise.
Here are a few more ways security professionals across higher education facilities can leverage a modern access control solution to ensure ease of movement on campus while enhancing COVID-19 safety measures for students and staff:
- Proximity and COVID-19 contact tracing reports: Pull access control reports to identify all people at increased risk of being in contact with contaminants or contagious individuals.
- Mobile credentials, biometrics and touchless readers: Implement mobile credentials and minimize the touchpoints throughout campuses by installing contactless and biometric readers.
- Contactless evidence and data sharing: Avoid the physical hand-off of documentation and speed up the transfer of information with internal stakeholders, external agencies or industry regulators by using a digital evidence management system.
Ensuring Privacy and Partnering With the Right Vendor
Though helpful at ensuring COVID-19 protocols, tracking and tracing people on campus has heightened privacy concerns. With more devices being connected to networks than ever before, people are also hyper-aware of the rise in cybercrime and the risks of their personal information ending up in the wrong hands.
To build and nurture trust with faculty and students, higher education institutions must focus on choosing trusted vendors committed to privacy, cybersecurity and transparency.
These vendors typically engineer solutions with privacy and cybersecurity in mind. This gives security teams access to various tools such as end-to-end data encryption and multi-factor authentication to protect against threat actors. It also allows authorized individuals to define user access and privileges to restrict who can log into physical security applications and what they can see or do.
Security teams can enable add-on features such as video anonymization, which blurs identities in the footage when using cameras to track occupancy, or real-time health monitoring, which alerts operators to devices falling offline or other system vulnerabilities.
Security professionals should consider the following questions when deciding between providers:
- What tools does the vendor offer to help uphold privacy and data protection?
- What certifications does the vendor have, and what steps are they taking to comply with privacy legislation themselves?
- How transparent is the vendor about their data policies and practices? How do they mitigate and communicate vulnerabilities within their enterprise or solutions?
- Does the vendor offer solutions where privacy and cybersecurity features are enabled by default?
- Does the vendor solution allow us to standardize privacy and cybersecurity processes across different buildings, campuses and regions?
Building a Safer Campus Experience Beyond the Pandemic
Navigating health and safety mandates and restrictions during the pandemic has been challenging for everyone. Higher education institutions that implemented more modern and flexible access control solutions have had a leg up over others. That’s because they have been able to remain agile, deploying new purpose-built solutions that help them adapt to regulations.
As health mandates continue to evolve and a new normal sets in across higher education campuses, security professionals will need to keep up. That requires moving away from the limitations of older access control technologies, one phase at a time.
Choosing an open and scalable access control solution from a trustworthy and forward-thinking vendor is critical. This sets the right foundation for a higher education institution to access innovation, streamline processes, and enhance campus safety well beyond the pandemic.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!