The sneaky security risk of overprovisioning the network

At the start of 2020, businesses set out to execute on the well-laid, carefully thought out plans they’d spent months developing. But just a little over three months into the year — those plans suddenly became void. The pandemic was a massive disruptor to the seemingly airtight 2020 strategies, and enterprises had to quickly pivot to make sure they were able to continue providing service to their end users. The network, a crucial tool for enterprise connectivity, became even more of a foundation for business continuity in the new remote reality. To manage unprecedented demand on the network, IT teams took to overprovisioning — adding additional capacity to the network — as a quick fix to maintain connections between employees, stakeholders and customers.
Network overprovisioning isn’t new; rather, it’s a common tactic used by IT teams to ensure performance is maintained throughout periods of unpredictable demand or network failures. Given networks act as critical infrastructure for businesses, even before remote work became the norm, overprovisioning was commonly used to maintain network continuity and ensure business continuity. Often, the cost associated with overprovisioning is much less than any potential losses due to network downtime. And within certain industries, those losses are beyond what could be measured from a monetary perspective. Take healthcare, for example; any issues in communicating with other providers or not being able to access certain information could be detrimental to a patient’s health and welfare. Regardless of whether the services are mission critical or not, network downtime or slowdowns can massively impact the quality of end-user experience.
The state of overprovisioning
Recent research looked at the current state and perception of overprovisioning, asking 500 U.S.-based enterprise IT teams about the practice and found that 67% of respondents — more than two-thirds — overprovision in an attempt to quickly counteract performance issues rather than address the root cause of performance degradation. Unfortunately, this can have dire consequences for businesses from a security standpoint since overprovisioning increases the attack surface and makes networks more vulnerable to bad actors. And with ransomware attacks, breaches and security issues doubling throughout 2020 (not to mention, the costs associated with managing them are higher than ever before), a common practice that increases these risks shouldn’t be the “go-to” fix. It seems that IT teams know this: as shown in the infographic below — almost three-fourths of respondents (72%) noted that security is their biggest concern when it comes to overprovisioning, and 62% believe their network vulnerabilities increase when they do so. So if the awareness is there, why are teams still turning to overprovisioning?
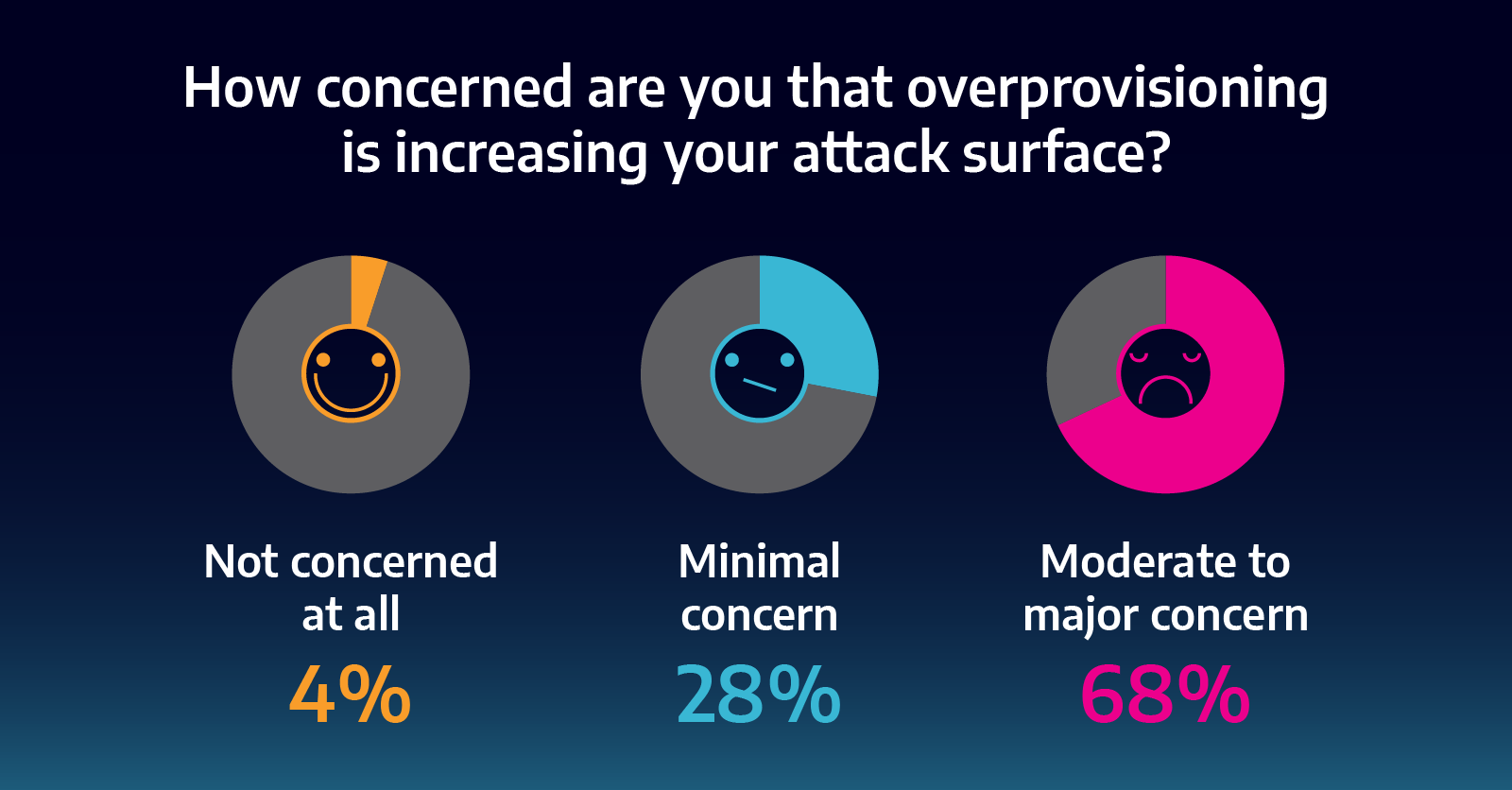
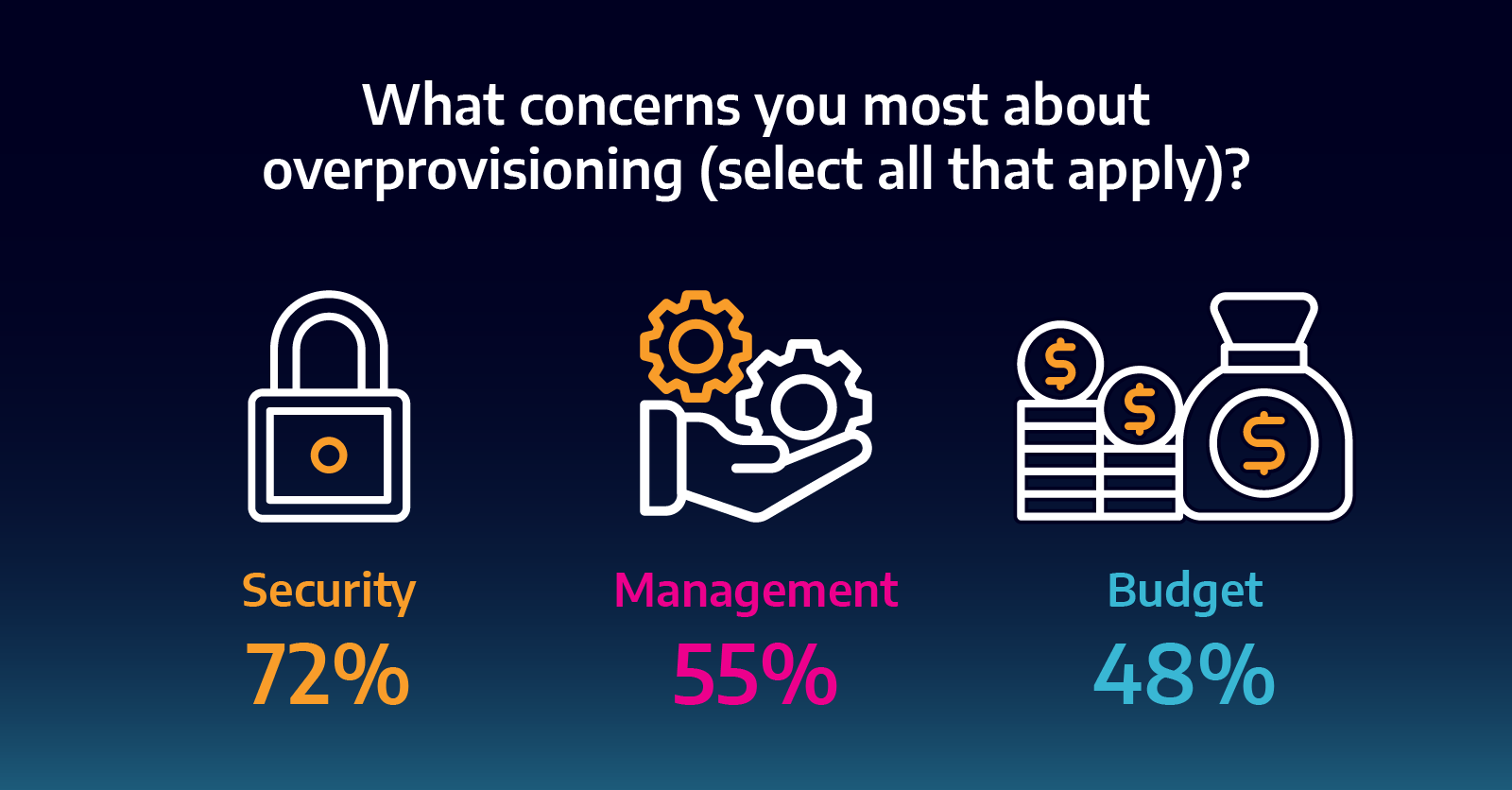 Images courtesy of Accedian
Images courtesy of Accedian
Be smart about network traffic.
The same research found that the challenges facing IT teams in addressing the issue centered around not having enough time (40%) and not having the right tools (36%). This makes sense; managing a potential traffic influx can be massively time-consuming, particularly without the right technology to help. Without this support, overprovisioning might seem like the only option to maintain service levels and ensure profits aren’t hit hard by degradations or downtime. But with the security risk greater than ever (and IT teams fully aware of this!), enterprises need to find another solution. The good news is that the right technology can help.
Think about network traffic like physical traffic. When highways become too congested, and traffic backs up, the first approach to fixing it might be to build more lanes. For a while, this might work. But soon enough, the increased supply will lead to increased demand; more cars will use these new lanes, and before you know it, it’s back to heavy traffic. Instead, more infrastructure teams are turning to adding smart technology — using sensors and algorithms to understand traffic patterns, proactively identify potential bottlenecks and reroute individuals as needed.
The same should be said for the approach to fixing network traffic. Smart monitoring technologies can ensure traffic flows smoothly, any impending risks are flagged proactively, and that security stays a top priority. The good news is that these solutions exist, and yet more than half (54%) of respondents reported not having network monitoring tools in their tech stack. That means it’s just a matter of education.
Lessons learned for 2022
We’re heading into the last few months of 2021, and enterprises are undoubtedly making plans for 2022. The biggest lesson learned from the past two years is to expect the unexpected and prepare your tech stacks for what might come. Businesses don’t know for sure what the next year will look like; what they do know is that maintaining enterprise connectivity and security is possible with the right tools. With the right network monitoring solution, overprovisioning, like other parts of 2020, can be something we finally leave behind as we enter the new year.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






