Defining synthetic identity fraud once and for all

I had the honor of serving on a Federal Reserve committee this past winter to define synthetic identity fraud. The result of this effort was the release of a paper that defines it for the industry, an essential step forward in the fight against this pervasive threat.
Fraudsters Thrive on Imprecision
Synthetic identity fraud can be a perfect crime. Fraudsters can simulate information and find loopholes to register that information in credit systems. It often goes unnoticed because there is no consumer victim contacting a lender to report a fraudulent account. Financial institutions often treat losses tied to synthetic identities as credit losses because they lack any ties to real consumers who report a stolen identity. This makes it hard for banks to identify and remediate in their fraud queues.
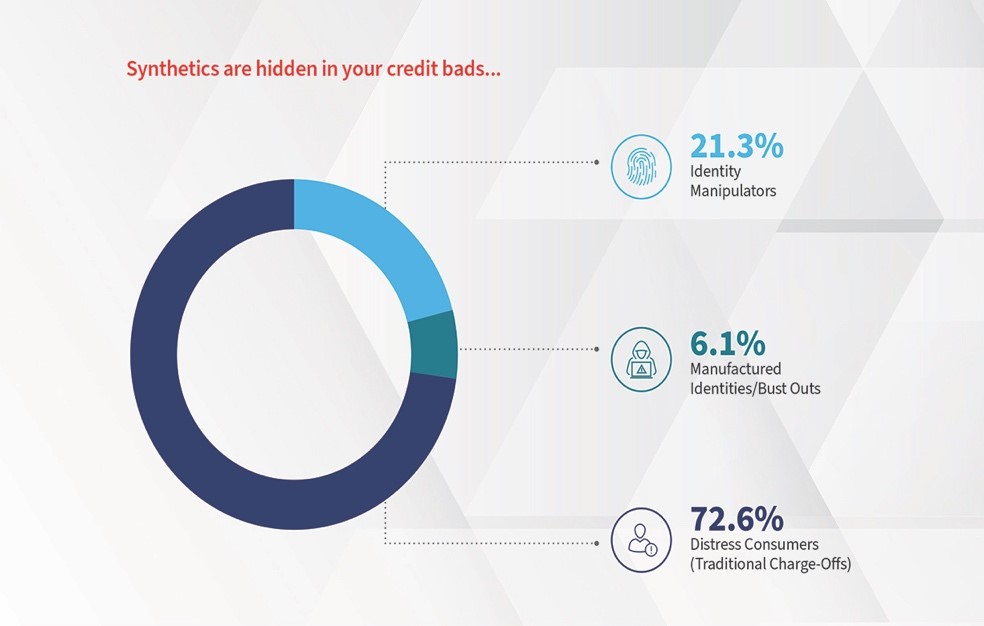
Fraudsters simulate positive behavior to entice lenders to offer them credit and ultimately default on that credit. As a result, they “hide” among credit defaults. The figure below* shows the proportions of credit charge-offs that are likely synthetic identity fraud from one such portfolio. In this study, roughly 21.3% of the defaulting consumers engaged in some form of identity manipulation, and 6.1% of the charge-offs were truly fabricated identities.
One of the best ways to fight fraud is clearly understanding identity patterns at various stages of the fraud scheme. One obstacle in achieving clarity is that companies don’t share a common language and definition in their fight against synthetic identity fraud. The fraudster needs to only find one gap in the system by luck, cleverness or both. We can’t develop unified strategies to combat synthetic identity fraud if we can’t define it. The Federal Reserve’s unifying definition adds much-needed clarity and consistency.
Confusion Drives the Lack of Consistency in Defining Synthetic Identity Fraud
As defined by the Federal Reserve, synthetic fraud comes from “the use of a combination of personally identifiable information to fabricate a person or entity in order to commit a dishonest act for personal or financial gain." This definition is intended to be common across industries. The Federal Reserve closed a gap in how affected industries should think about synthetic fraud. Fraudsters who utilize synthetic identities are most successful when they take advantage of a weak link in a company’s fraud defenses. Fraudsters rely on confusion and inconsistency, so lack of definitional clarity helped fraudsters thrive in a variety of ways.
First, a fraudster does not care if they are stealing from a bank, credit union, insurer, government, payment processor, individual, or other entity. Fraudsters like varying their targets because they know that different industries are less coordinated in their response compared to two entities from the same industry or institution. This helps fraudsters hone their methods while also subverting institution or industry-specific fraud reduction efforts. Synthetic fraudsters vary their schemes across industries. When fighting fraud, fraud mitigation teams and analysts in different verticals may use the same term, but they are fighting different types of fraud, which prohibits consistent response to these schemes.
Second, confusion also stems from the industry trend to define and manage first-party fraud and third-party fraud by different processes. First-party fraud indicates a fraud that a consumer executes in their own name. Third-party fraud involves a consumer who is the victim of a fraudster, such as through identity theft. Businesses often manage these two types of fraud differently in industry workflows. This means that synthetic identities — which are third parties committing first-party fraud on fake identities — do not fit cleanly in either workflow. By mixing synthetic fraud with typical first-party fraud or third-party fraud workflows, one can miss the nuances of synthetic fraud entirely.*
Third, an issue lies in the gap between fraud controls and credit risk management controls. A synthetic identity is generally a highly curated ‘consumer’ who pays their bills over time until they stop paying. When a low-risk and high-revenue consumer stops paying their bills, the account management workflow will usually push the account towards a collections queue, not a fraud queue. Therefore, it’s common to see collection portfolios littered with these sorts of synthetic identities — consumers who seem to have stopped paying their bills suddenly. There is little feedback to the underwriting team to flag these forms of identity manipulation because they are flagged as uncollectable rather than fraud write-offs.
Finally, the fast evolution of fraud creates a series of variants that get increasingly more complex. Internal definitions of synthetic identity fraud may become either outdated or overly generalized after fraud analysts identify them, or worse, analysts may start using very broad definitions of synthetic identity fraud under an “all else” mindset. This sort of catch-all performance definition becomes self-defeating and further confuses the synthetic identity fraud concept, making it harder to define and prevent.
The Advantages of the Federal Reserve Definition
There is real value in the Federal Reserve’s official guidance on the elements that are most critical in identifying synthetic identity fraud. This helps make the definition consistent for all credit issuers. The definition is also high level and lays out the relevant information for diagnosing.
The definition lays out four use cases: credit repair, fraud for living, payment default schemes and other criminal activity, such as money laundering and human trafficking. It is critical to note that they are all characterized by different schemes and fraud types. The definition also lays out a series of identity and behavioral markers of this type of fraud. This is important because the combination of identity elements with behavioral elements helps differentiate synthetic behavior from other types of fraud and non-fraud behavior. The Federal Reserve definition also supports a certain amount of flexibility and interpretation. If the Federal Reserve laid out specific criteria, fraudsters would likely have pivoted to make the definition obsolete quickly.
What’s Next?
The definitions from the Federal Reserve are clarifying but stop short of mitigation methods. This is important because laying out specific mitigation methods can be self-defeating. Doing so would equally hard code responses and inform fraudsters on what screens to bypass to be successful. Since fraudsters tend to evolve and change approaches, we need to use strong forensics and data mining to identify variants that may emerge. Methods to address synthetic identity fraud should focus on disrupting the fraudster’s business models. This forensics approach can help fraud analysts better understand a broader picture of identity.
*Metrics are from LexisNexis Risk Solutions proprietary data sources.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!









