80% of global businesses expect a breach of customer records in the next year
CREDIT: Trend Micro
According to a new survey, 80% of global organizations report they will experience a data breach that impacts customer data in the next 12 months.
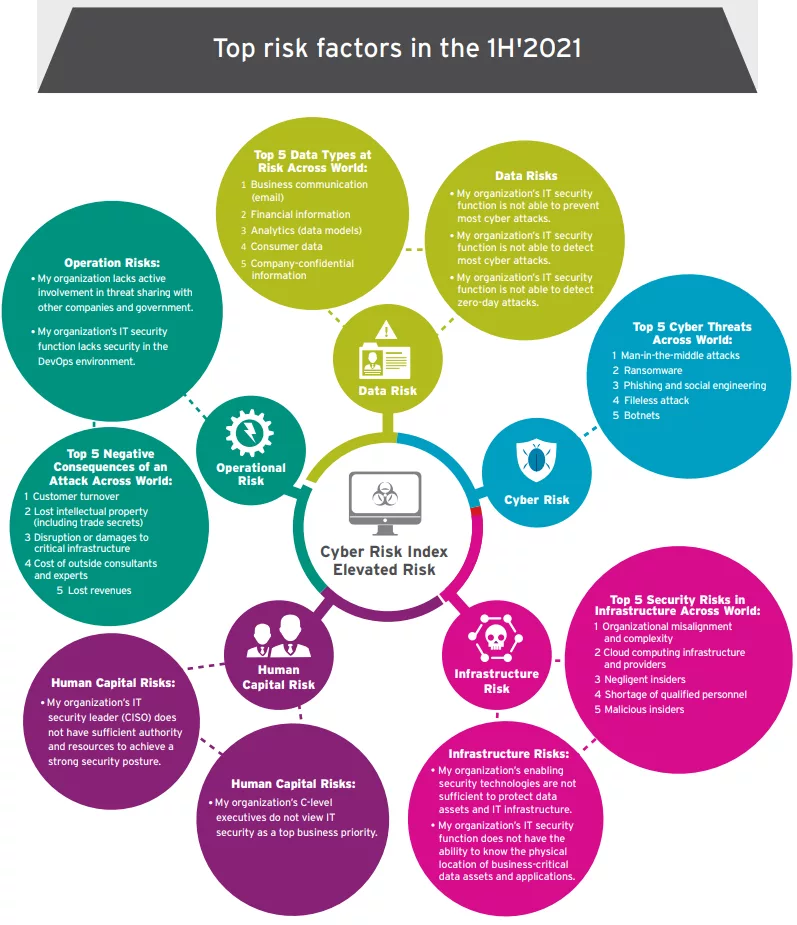
The findings come from Trend Micro’s biannual Cyber Risk Index (CRI) report, which measures the gap between respondents’ cybersecurity preparedness versus their likelihood of being attacked. In the first half of 2021, the CRI surveyed more than 3,600 businesses of all sizes and industries across North America, Europe, Asia-Pacific, and Latin America.
The CRI is based on a numerical scale of -10 to 10, with -10 representing the highest level of risk. The current global index stands at -0.42, a slight increase from last year, which indicates an “elevated” risk.
Organizations ranked the top three negative consequences of an attack: customer churn, lost IP, and critical infrastructure damage/disruption. This data, says Tyler Shields, CMO at JupiterOne, a Morrisville, NC.-based provider of cyber asset management and governance solutions, is surfacing in people’s level of fear. What the survey doesn’t get to, however, is understanding how much impact those same people think it’ll have on their business. If the impact to the business isn’t horrible, many people will ignore the problem, and that gets us nowhere when it comes to properly fix the global cyber security problem.”
Shields adds, “Creating accurate measurements of progress is the key. Understanding what your cyber assets look like and what risks they have at any given moment and then tracking improvement on that risk value is the key to combating the sense of impending doom. All you can do is drive to improve as quickly and efficiently as possible, and if you don’t measure your results, you will never feel like you are winning.”
Key findings from the report include:
- 86% said it was somewhat to very likely that they’d suffer severe cyberattacks in the next 12 months, compared to 83% last time
- 24% suffered 7+ cyberattacks that infiltrated networks/systems, versus 23% in the previous report.
- 21% had 7+ breaches of information assets, versus 19% in the previous report.
- 20% of respondents said they’d suffered 7+ customer data breaches over the past year, up from 17% in the last report.
“There’s no question that we continue to see high profile data breaches in the news and that this trend will continue,” says John Morgan, CEO at Confluera, a Palo Alto, Calif.-based provider of Cloud eXtended Detection and Response (CxDR) solutions. “Given the complexity of our computing environments, the only barrier between an attacker and the target is motivation. This is because the attacker community is commoditizing attacker technology and know-how the same way law-abiding businesses do. However, this is more of a call to action than a statement of ‘giving up.’ Innovations must continue with more secure architectures and practices, but a big change in philosophy is that organizations will not be able to rely solely on preventative measures as they must assume they will be breached and invest in technologies to detect and stop it before damages occur.”
Among the top two infrastructure risks was cloud computing. Global organizations gave it a 6.77, ranking it an elevated risk on the index’s 10-point scale. Many respondents admitted they spend “considerable resources” managing third-party risks like cloud providers.
The top cyber risks highlighted in the report were as follows:
- Man-in-the-middle attacks
- Ransomware
- Phishing and social engineering
- Fileless attack
- Botnets
Kevin Dunne, President at Pathlock, a Flemington, N.J.-based provider of unified access orchestration, says companies are becoming overwhelmed by the number of cyberattacks they are facing as cyberattackers get more courageous and exploit the increasing shift to cloud applications and infrastructure. “For now, many of the attacks come without consequence, and the cost to prevent the attacks seems to outweigh the cost of a data breach. However, that dynamic is beginning to change, as ransomware attacks cause multimillion disruptions to businesses. Additionally, privacy regulations like GDPR and CCPA are starting to result in government agencies handing out significant, multimillion-dollar fines for non-compliance.”
The top security risks to infrastructure remain the same as last year, including organizational misalignment and complexity and cloud computing infrastructure and providers. In addition, respondents identified customer turnover, lost intellectual property and disruption or damages to critical infrastructure as vital operational risks for organizations globally.
In addition, the study found that the main challenges for cybersecurity preparedness include limitations for security leaders who lack the authority and resources to achieve a strong security posture, as well as organizations struggling to enable security technologies that are sufficient to protect their data assets and IT infrastructure. “
Morgan suggests that organizations need to look into processes and solutions that better focus the security resources they have. He says, “Knowing that you cannot double or triple the security staff, they need solutions that can provide the same results by increasing efficiency. This requires a different approach to evaluating security processes and solutions. Rather than the key drivers being “Can a solution detect the latest malware, hackers, and threats?” they need to ask, “Can a solution show me what is relevant for me to investigate? And only what’s relevant.” Moving forward, we cannot let security issues hinder innovation. I believe a security solution does not just protect the data and applications we already have but serves as a foundation for innovations and applications to flourish. We must keep up the good fight; technology advancements are becoming essential to our survival.”
According to Dunne, organizations should focus their efforts on implementing an effective cyber defense program that addresses the following:
- Understanding potential threats and the latest exploits
- Enabling members of the business on how to be aware of possible attacks and avoid them
- Preventing risks by putting in place controls and reducing exposure through zero trust
- Monitoring all activity to highlight suspicious behavior
- Preparing for recovery from attacks and potential outages
He adds, “Though there is an ever-expanding list of exploits, fortunately, technology and consulting firms are working overtime to provide companies at risk with the latest and greatest tools and techniques to combat these attacks. Ultimately, cybercrime is a critical issue that must be addressed by almost every organization. As industries continue to face digital disruption, the ability to safely conduct business in the cloud is essential to success. Currently, we are at an unusual juncture where there is a lack of global oversight regarding cyberattacks and cybercrime. As the world starts to acknowledge that these cybercrimes harm business as a whole, there will be a push to come together and present a unified front against attackers. Once this level of collaboration is reached, there should be a clearer end in sight to the current cybercrime issues facing today’s business leaders.”
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




