Turning security into a frictionless experience
It’s evident that ease of use has become of growing importance in the security industry. It’s apparent on the system management side, where mobile applications have helped to simplify the ability to remotely manage video and access control solutions. And, desktop security applications have evolved from clunky platforms that required extensive training into an intuitive and graphic-rich user experience.
Now, user experience is at the forefront of the evolution of security technology, with devices being developed that both enhance and simplify the way in which people interact with security solutions.
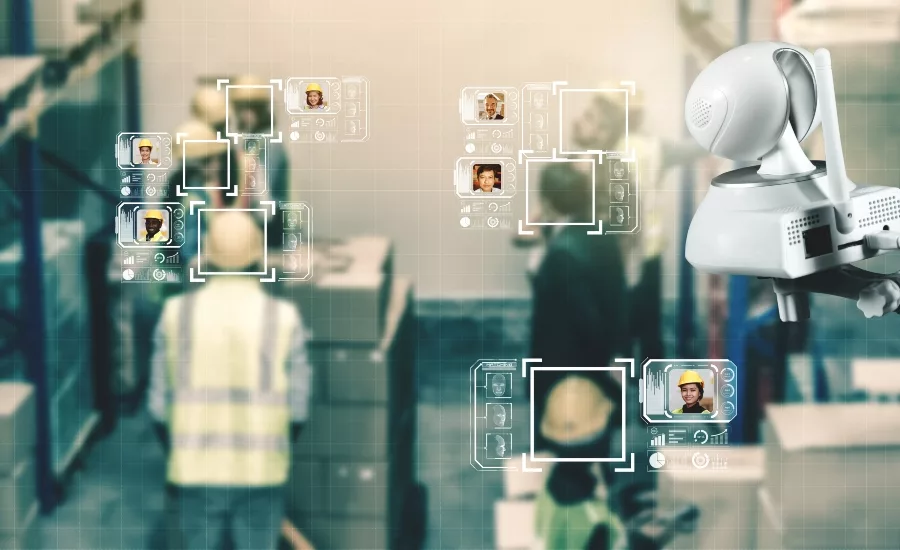
One significant advancement for the security industry has been the development and introduction of frictionless access control technology – a solution that alters and simplifies the overall user experience. Once considered science fiction, this capability is now a reality. Frictionless access control validates an individual and permits access into a defined area without the individual needing to stop and present a credential, radically changing how individuals gain access into a secure area.
In one scenario, a person would simply walk through a predefined area, while a combined surveillance and access control solution would use facial recognition technology to validate that person’s identity and determine if that individual has permission to enter that area.
This approach is a game changer for the security industry, offering the first ever unobtrusive access control solution that can also accurately manage large volumes of people. How is security becoming a frictionless experience?
Some frictionless access control systems leverage enhanced facial detection technology to differentiate between a real person and a photograph of a person. Two imagers in the surveillance camera help to create a 3D facial topography, which increases accuracy and reduces false positives. When integrated with an access control system, the result is a solution that automatically recognizes an individual in a database and determines whether that person should be permitted to enter.
None of this, however, would be possible without advancements in artificial intelligence, deep learning algorithms and faster processing speed, allowing these systems to accurately process multiple people in the same frame and the ability to detect and recognize individual faces from several feet away. Such high throughput is ideal for large volume areas such as high-rise corporate offices during the busy morning hours, airports to reduce the risk of card sharing and tailgating into security sensitive areas, and the gaming industry, where the system can flag persons of interest for an integrated access control system action, for instance, generating an alert when a VIP is identified.
In markets where hygiene is critical, a frictionless access control solution can eliminate medical professionals from needing to present a badge to enter an operating room after scrubbing up. It can also be used to protect highly sensitive areas, such as the pharmacy and medical drug cabinets and private staff areas.
Frictionless access control is also being incorporated into areas that require a second factor of authentication. Traditionally, multi-factor authentication has brought together two forms of identification to confirm an individual is permitted to enter a specific area. For example, this could include a person presenting an access control credential along with biometric fingerprint technology, or an identification card combined with a unique PIN number. However, having to present two items can impede the flow of traffic in high volume areas because two-factor authentication is typically more time consuming than when a person presents a single credential.
Incorporating frictionless access control for higher security areas accomplishes two things. First, it provides another multi-factor authentication method. And second, facial recognition technology provides an extra level of security and is less time consuming than entering a PIN number, thereby speeding up the process.
This article originally ran in Security, a twice-monthly security-focused eNewsletter for security end users, brought to you by Security Magazine. Subscribe here.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!









