Who owns AD security in your organization?

Background photo created by natanaelginting - www.freepik.com
Establishing operational resilience in the face of cyberattacks has become a top priority for organizations. As a core component of the IT infrastructure, Active Directory (AD) must be at the center of that process. But who is responsible for ensuring Active Directory is both protected and can be recovered quickly when a cyberattack occurs? In many organizations the answer is not clear, which can lead to missteps in detecting, defending against, and responding to cyberattacks.
AD is part of an IT organization’s Tier 0 infrastructure, meaning that it is a service upon which the company’s critical applications and processes depend. If AD isn’t running, many information systems shut down. AD is the primary authentication service for nearly all companies, and usually serves as the primary “source of truth” for the company’s identity management and authorization functions. AD provides endpoint configuration services through group policy. And AD-integrated DNS is a core networking service for most IT organizations. Nearly every cyberattack uses AD at some point in its evolution.
This combination of capabilities means that several groups within the IT organization will have interest in Active Directory’s care and feeding:
- The IT operations team: This team performs day-to-day administrative tasks in AD such as patching, joining and removing servers and workstations, resetting passwords, changing users’ profile information, running reports, and creating and deleting users and groups. They also typically manage AD server backups.
- The Windows Server team: In many organizations, AD falls to the Windows Server team to manage. This team is responsible for all the Windows servers on the network, and because AD is part of the Windows OS, managing it is a straightforward extension of the work they already do.
- The identity team: If the operations team doesn’t manage users and entitlements, an identity team has this responsibility. They manage the transfer of data and policies from the HR systems to AD, either manually, using scripts, or with some sort of a provisioning product.
- The security team: The security team typically sets security and access control policy and manages the IT infrastructure from a security point of view, making sure that systems are patched, network devices are properly configured, and deploying and monitoring endpoint detection and prevention tools such as antivirus. The security team also typically performs periodic audits and monitors the network for malicious activity.
In the “business as usual” scenario, day-to-day operations clearly fall to the operations group. The Windows Server team will handle normal maintenance, configuration, troubleshooting, upgrading, and so forth. The identity team, if it exists, will manage the automated provisioning of accounts and permissions. And the security team will set security policy and audit and monitor the environment. But who should develop the cyber-resiliency plans for AD? The answer is not necessarily clear.
Approaching the cyber-resiliency problem for a system as pervasive and as complex as Active Directory requires the involvement of all the groups that have both relevant knowledge and a vested interest in keeping AD secure. All the groups mentioned above should be involved. And there’s the rub: It’s a bit like the parable of the blind men and the elephant. Each group will have its own view of what Active Directory is, how it is used, and what should be done to make it more resilient. How do you get these disparate groups to achieve some consensus for an Active Directory security strategy?
Agree on a Framework
The first step is to agree on a framework for understanding and discussing the problem. The best approach I’ve seen is based on the NIST Cybersecurity Framework model, which divides the cyber-security universe into five buckets of activities:
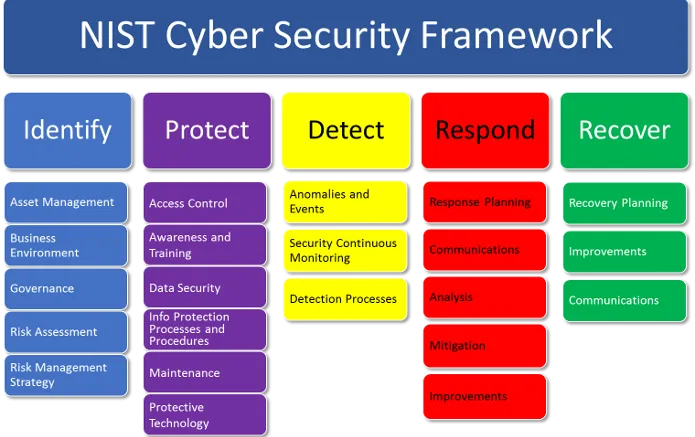
NIST Cybersecurity Framework 1.1. Image belongs to NIST
Right away, the teams can see where their normal responsibilities fit, and they can bring their knowledge and expertise to bear on developing a strategy that addresses all five activity categories.
Establish Priorities
The scope of security activities around Active Directory is both wide and deep, and trying to bite off the whole thing at one time has little chance of success. If the group hasn’t been given priorities from upper management or the business continuity/risk management departments, they must develop priorities themselves. This is a conversation that can be led by the security team because they should have some expertise in threat assessment and risk modeling. For instance, consider a situation in which the identity management team has a good process for provisioning users and access rights and the security team has effective monitoring in place. Despite that good groundwork in place, if there is no plan to recover Active Directory from a successful ransomware attack, developing an AD recovery plan should be at the top of the list.
Develop the Strategy and Projects as a Team
It’s easy to fall into the trap of delegating any particular cybersecurity project to the team that seems to have the most relevant expertise, but this is a mistake. We’ve already seen that the scope of Active Directory security spans all the teams, and each team can have valuable input into both the overall strategy and the individual projects. Continuing with the example of developing an AD recovery plan, it’s likely the Windows Server team will have the most expertise regarding the recovery of AD from backup, but the security team might have input into how to assess the backups to identify the most suitable one to recover from. The identity team will understand what should be done to re-synchronize the restored Active Directory with the HR system. And the operations team might understand what applications are most critical—and, therefore, which AD domain controllers should be recovered first. Involving the entire group will help ensure that the strategy incorporates all the expertise available. This approach has the side benefit of building trust and buy-in across the teams.
Keep Your Strategy Flexible
The threat landscape for enterprise IT changes on a monthly or even a weekly basis. One month, the most critical issue might be dealing with potential ransomware attacks. The next month, it might be determining the risk of your software supply chain. The month after that, it might assessing the damage done by threat actors taking advantage of vulnerabilities in Microsoft Exchange. While it is important to deliver security improvement projects on time, the overall strategy needs to accommodate the changes in the AD threat landscape.
What’s most important here is that AD needs to be resilient from both a security and operations perspective. After an attack, AD needs to keep the business running while protecting the environment from subsequent attack. It doesn’t take a village to develop a cyber-resilience strategy for AD, but it does take a concerted effort by multiple teams with a broad range of expertise. By starting the discussion now, you can avoid confusion, arguments, and rash decision-making in the midst of an attack response. Having clear roles for each team and good communication helps the organizations effectively prevent, detect, and respond to identity-related cyberattacks.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






