Five steps to secure your business – From the C-suite to the assembly line

As a security professional, you know that with organizational growth comes increased risk for cyberattacks. But it can be challenging to ensure security policies and programs don’t end up siloed between disparate departments, factories, warehouses, and management regimes—especially for large companies spread across international borders and harnessing complex supply chains and go-to-market motions.
This contributes to a diverse threat landscape and creates gaps that can be discovered and exploited by skilled cybercriminals.
For example, the 2013 Target cyberattack was made possible by a company contractor working in a small part of the company’s point-of-sale infrastructure. The contractor accidentally enabled a hacker to find and infiltrate Target’s financial systems and steal over 40 million customer contacts. In addition to the obvious erosion of customer trust and barrage of negative PR, Target ended up paying $18.5 million in multistate settlements and penalties.
In the years since, the need for uniform security policies and processes across the entire enterprise — from the boardroom to the home office, the assembly line to the warehouse — has become increasingly obvious.
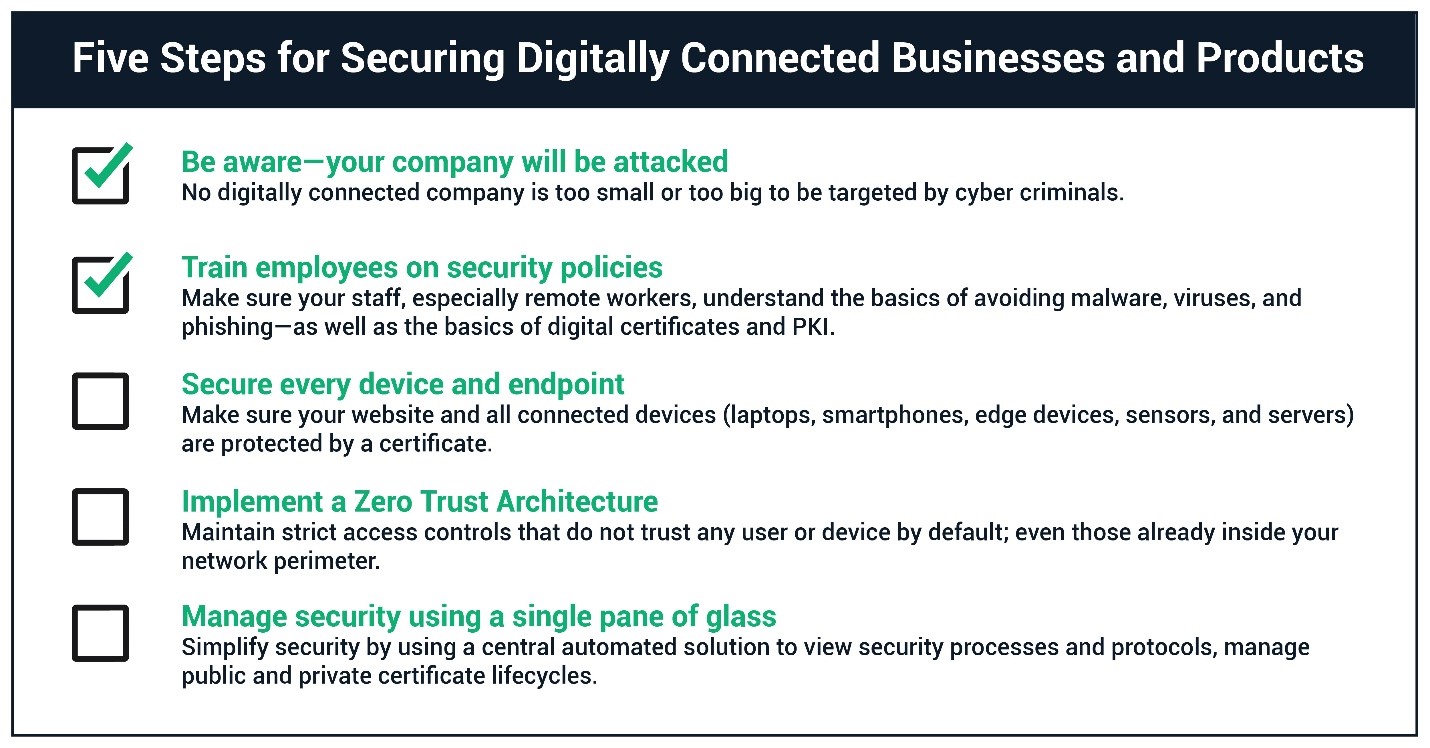
To get started, we have created a simple five step program for executives to ensure their organization is protected against the latest threat vectors and increasingly sophisticated cyberattacks.
To protect themselves against cyberattack, businesses need to implement the full spectrum of security policies and procedures. Image courtesy of Sectigo
Step One: Be aware that all companies, including yours, will be attacked. It’s clear that no company is too large or small to be targeted by cyber criminals or hackers. But it’s not just about stealing customer credit card details or financial assets. Every company has crown jewels of value to an attacker, be it intellectual property, customer contact lists, or logistical access to partner enterprises as part of its supply chain. The breaches of The Democratic National Party (DNC), the Office of Personnel Management (OPM), and Sony, made thousands of emails and sensitive documents available to the public. Privacy laws are now showing their teeth as well; British Airways was recently hit with a $230 million GDPR fine due to a data breach which leaked personally identifiable information for 500,000 customers.
Step Two: Ensure staff, especially remote workers, understand the basics of digital hygiene, and train them to recognize social engineering attempts like phishing. A 2020 Wakefield Research report pinpointed phishing as the biggest risk to data, systems, and operations due to employees working remotely. In addition to staff training, consider incorporating S/MIME certificates to verify sender identity and provide an additional layer of security to emails to help prevent socially engineered attempts from being successful. All digitally connected employees, from the C-suite to college interns, need to be aware of and willing to participate in a culture of sensitivity around corporate data.
Step Three: Make sure your web applications and all connected devices are protected by strong authentication, specifically with the use of certificates. The Target breach highlighted the fact that any IoT ecosystem can be infiltrated and exploited. It should not take hindsight to realize that handing out highly privileged credentials to a third party who manages HVAC devices is a bad idea, especially when those devices are on the same network as point of sale system devices.
As IoT continues to gain footing in our daily personal and professional lives, device-to-device authentication and user-to-device authentication by password are no longer sufficient. Rather, organizations and teams must use more sophisticated authentication methods, like no touch authentication and user identity certificates. At your organization, ensure employees are using the most up-to-date and advanced authentication methods available for the devices and services they use, and that the issuance of all identity certificates is automated. Lastly, be prepared to update authentication methods frequently in order to keep pace with the continuously evolving threat landscape.
Step Four: Incorporate principles of Zero Trust architecture, a model whereby trust is never granted implicitly. The perimeter-based legacy paradigm where internal devices were trusted because they were behind the firewall that only protected against external network access is no longer sufficient to protect an organization. Instead, with strict data access policies, ID management, and PKI, among other components, the Zero Trust model overcomes the fundamental flaw of legacy systems.
A recently released National Institute of Standards and Technology report entitled Zero Trust Architecture named PKI a logical component of the Zero Trust model. PKI identities serve as the basis of security for the shift to digital assets beyond the firewall, like the move to the cloud, IoT, and DevOps. To support a Zero Trust approach, the verification of digital identity has become critical, increasing the need for a consolidated, automated, and modern approach to PKI.
Step Five: Use a digital identity manager that offers a single pane of glass view for all your digital identities, security processes, and protocols. Make sure certificate automation for all different types of certificates, and also for all your certificate vendors, is included in and accessible through a centralized and easy-to-navigate dashboard. The right option allows you to access expiration dates and maintain cryptographic strength for public and private certificates while eliminating the potential for service disruptions. With automation, your team can avoid the labor intensive, technically demanding, and risky nature of manually managing–discovering, installing, monitoring, and renewing PKI certificates.
While we’re all familiar with the massive data breaches the likes of the DNC, OPM, and Target, millions more cyberattack happen every day on the web. Outages caused by lack of digital identity management and expired certificates can be solved through automation and visibility. Fostering a culture around the sensitivity of corporate data is essential to protecting your organization. Get started with these five tips today.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!









