GAO: DHS and selected agencies need to address cybersecurity shortcomings

The US Government Accountability Office (GAO) reviewed how 3 agencies—the Federal Aviation Administration, Indian Health Service, and the Small Business Administration—used cybersecurity tools that identify the hardware and software on their networks and check for vulnerabilities and insecure configurations.
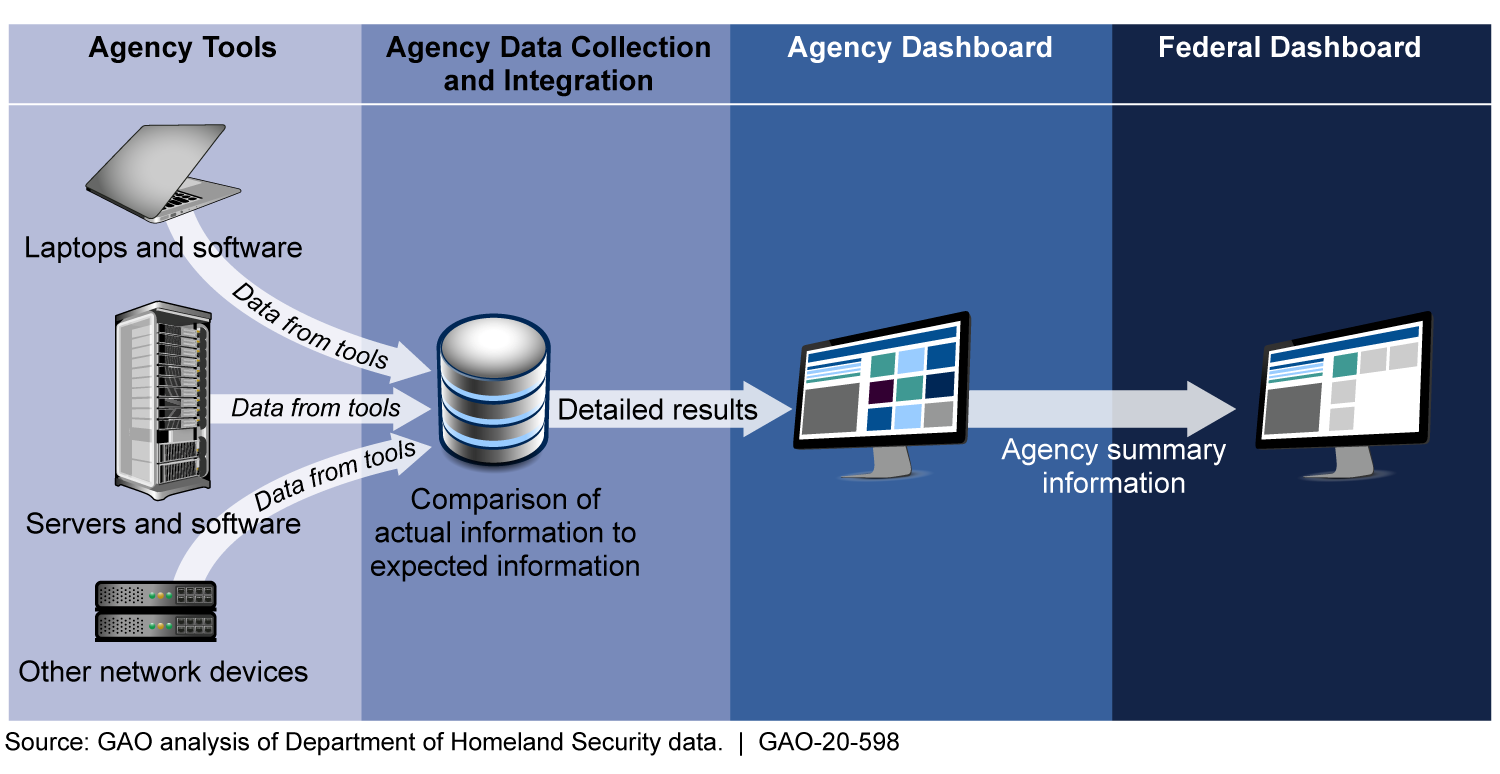
As depicted in the figure, the program relies on automated tools to identify hardware and software residing on agency networks. This information is aggregated and compared to expected outcomes, such as whether actual device configuration settings meet federal benchmarks. The information is then displayed on an agency dashboard and federal dashboard.
Continuous Diagnostics and Mitigation Program Data Flow from Agencies to the Federal Dashboard
According to the results, while agencies reported that the program improved their network awareness, none of the three agencies had effectively implemented all key CDM program requirements. For example, the three agencies had not fully implemented requirements for managing their hardware. "This was due in part to contractors, who install and troubleshoot the tools, not always providing unique identifying information. Accordingly, CDM tools did not provide an accurate count of the hardware on their networks. In addition, although most agencies implemented requirements for managing software, they were not consistently comparing configuration settings on their networks to federal core benchmarks intended to maintain a standard level of security," says GAO.
The agencies identified various challenges to implementing the program, including overcoming resource limitations and not being able to resolve problems directly with contractors, GAO says. "DHS had taken numerous steps to help manage these challenges, including tracking risks of insufficient resources, providing forums for agencies to raise concerns, and allowing agencies to provide feedback to DHS on contractor performance."
GAO, in turn, is making six recommendations to DHS, including to ensure that contractors provide unique hardware identifiers; and nine recommendations to the three selected agencies, including to compare configurations to benchmarks. DHS and the selected agencies concurred with the recommendations.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








