Panda Security Report: Ransomware & Fileless Attacks are a Growing Concern

With cyberthreats continually evolving and proliferating, security professionals of all types, from CISOs to MSPs and other providers need to look beyond the reactive approaches to cybersecurity and embrace a more forwardthinking strategy, according to a new Panda Security Threat Insights Report 2020.
The Panda Security Threat Insights Report 2020 highlights data compiled by PandaLabs – the anti-malware laboratory and security operations center (SOC) of Panda Security, which has illuminated several emerging trends in the cybersecurity space. The report analyzed 14.9 million malware events in 2019, stopping 7.9 million Potentially Unwanted Programs (PUPs), as well as 76,000 alerts for exploits that intended to leverage vulnerabilities in applications, networks, or hardware in order to compile the main cybersecurity threats and trends.
The report found that the main cyber threat trends include:
- Ransomware, the notorious malware variant, is still persistent. A single click is enough to paralyze an entire network, doing away with security controls and backups to make as big an impact as possible in the shortest amount time.
- Fileless attacks are a growing concern. They are more difficult to detect, making it easier for cybercriminals to attack stealthily. Cybercriminals are changing how they attack, and their strategies no longer necessarily need a specific file to break into a network.
- Proactive threat hunting. This is now an essential solution for recognizing abnormal and malicious behaviors that exploit trusted applications.
- Cybersecurity solutions can no longer be based on one single technology. They require an approach based on layered technology, combined with a zero-trust posture to stop possible security breaches.
Below are more findings from the survey.
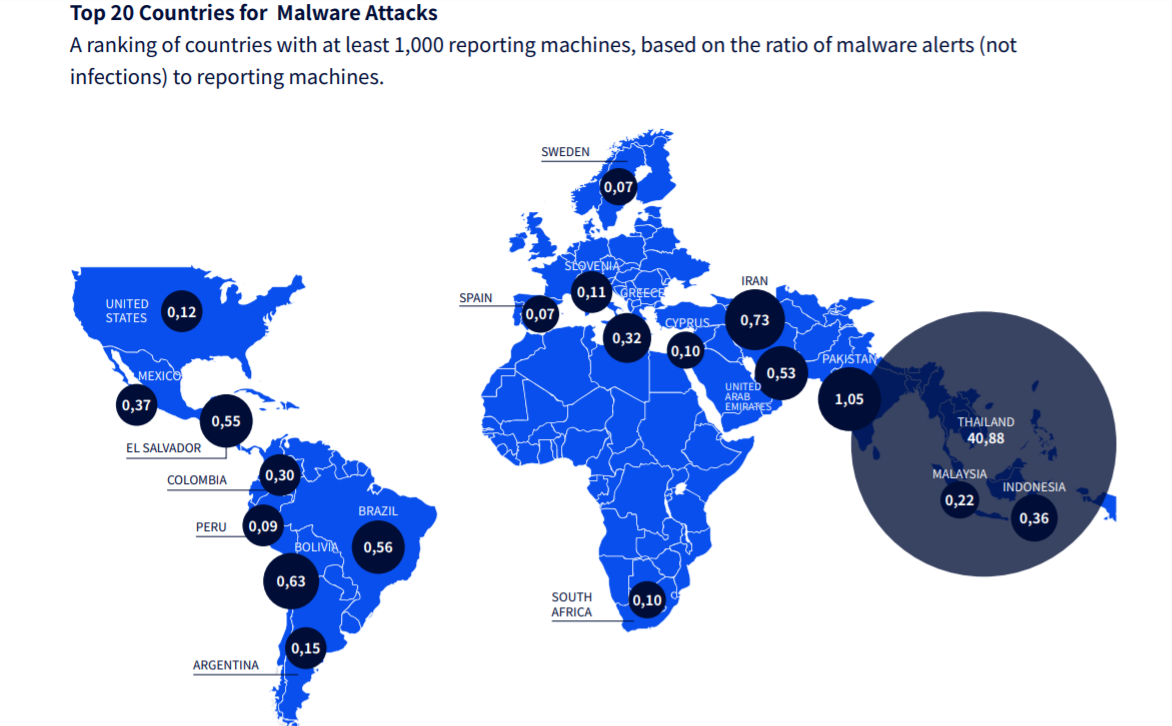
Global Hotspots: The Attackers or the Attacked?
From the data, there is a dramatic lead in targets in the Middle East and South America. However, Thailand leads the pack exponentially. This outcome may be expected, but the insight is double edged, says the study. These countries are good targets for a reason, as hackers have had success here in compromising systems, due to exposed, under-secured endpoints. It can be assumed that these targets are not the end goal, notes the study, but rather the source of other, even more sophisticated attacks on targets worldwide.
 *Image courtesy of Panda Security.
*Image courtesy of Panda Security.
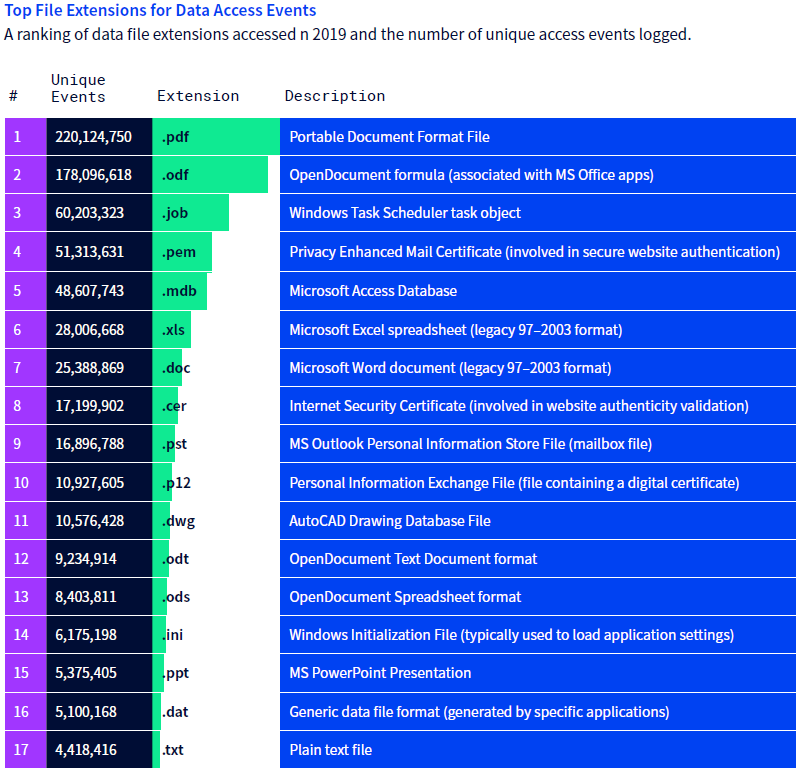
This data, compiled from endpoints running Panda Adaptive Defense technology, reveals the power behind certain file extensions—many of which are seen by users every day, found the study. And behind each of these extensions lies a vulnerability in the very nature of their file that can be exploited by bad actors to carry out attacks: the PDF, a ubiquitous file format used globally every day, tops the list—and with good reason: they have been notorious for decades in their ability to carry out malicious attacks and inject malicious code on application processes or used as a medium for phishing campaigns, with just one unsuspecting click by a user, says the study.
*Image courtesy of Panda Security.
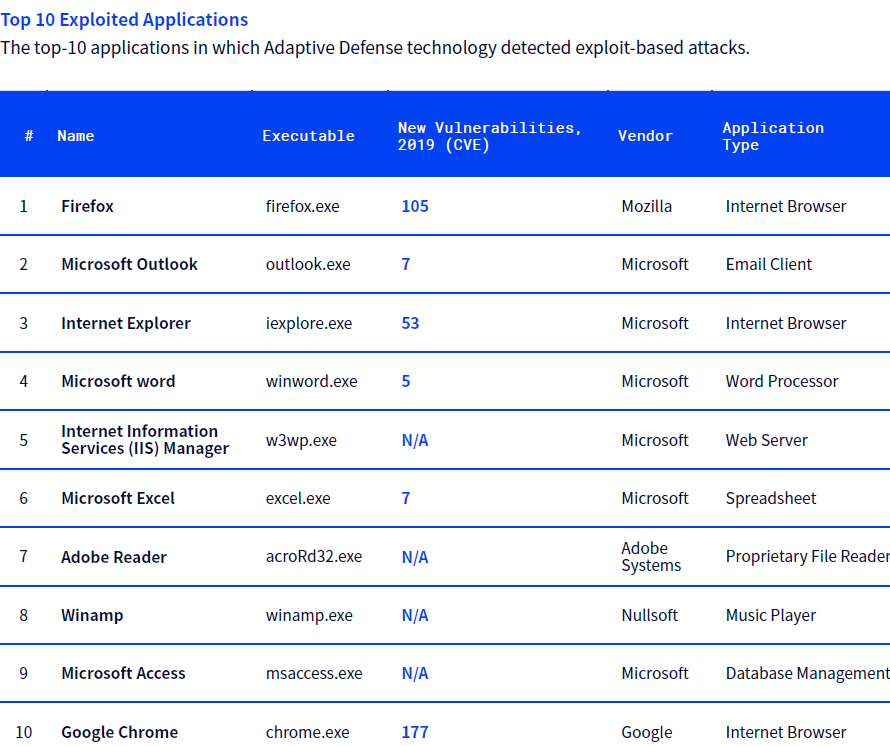
The New Threat: Fileless Attacks
New data confirms the global position on live hacking through the exploit and use of commonly whitelisted productivity tools, browsers, and OS components that are ubiquitous on the vast majority of endpoints worldwide, says the study. No application or executable on this list would ever be classified as suspicious, let alone malware, which make them perfect vectors for fileless attacks, live hacking, living-off-the-land (LotL) attacks, and more. This list (below) exposes the absolute necessity for antiexploit technology, say the researchers. Note that there is no one common denominator for why each of these applications are chosen by attackers. For example, Microsoft IIS is exploited for its ability to spin up countless websites, while Microsoft Office macros open up the ability for screen and key logging, which is why context-based behavioral analysis is necessary to detect these attacks.
*Image courtesy of Panda Security.
For the full report, please visit https://www.pandasecurity.com/mediacenter/panda-security/threat-insights-report-2020/
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








