Data Breach Report: Cloud Storage Exposes 270,000 Users’ Private Information

Led by cybersecurity analysts Noam Rotem and Ran Locar, vpnMentor’s research team recently found a serious breach in an open Amazon S3 bucket owned by secure cloud storage provider Data Deposit Box.
The leak exposed detailed information about 270,000 private files uploaded by customers through the company’s secure cloud storage service. The database also revealed personally identifiable information (PII) of customers, which could have serious consequences for those affected.
Data Deposit Box is a public company that offers secure cloud backup storage services to individuals and small businesses. The business is based in Canada but has over 350,000 users spread across 84 countries. Data Deposit Box allows customers to continuously backup an unlimited number of devices to their accounts through the company’s app and web portal.
The research team identified Data Deposit Box as the owner of the database and reached out to the company to share their findings and provide guidance on how to resolve the issue. Once they received a reply, Data Deposit Box responded quickly to secure the data. The company assured the vpnMentor research team that they are currently working with their customers to ensure their data is safe going forward.
- Date discovered: December 25, 2019
- Date owners contacted: December 30, 2019
- Date database closed: January 6, 2020
Example of Entries in the Database
More than 270,000 files were exposed in the data breach, with leaked files dating back from 2016 to the present day. The research team was able to view sensitive user account information, as well as some of the stored contents. Examples of leaked private user data include:
- Admin login credentials, including usernames and unencrypted passwords
- IP addresses
- Email addresses
- GUIDs (globally unique identifiers for resources)
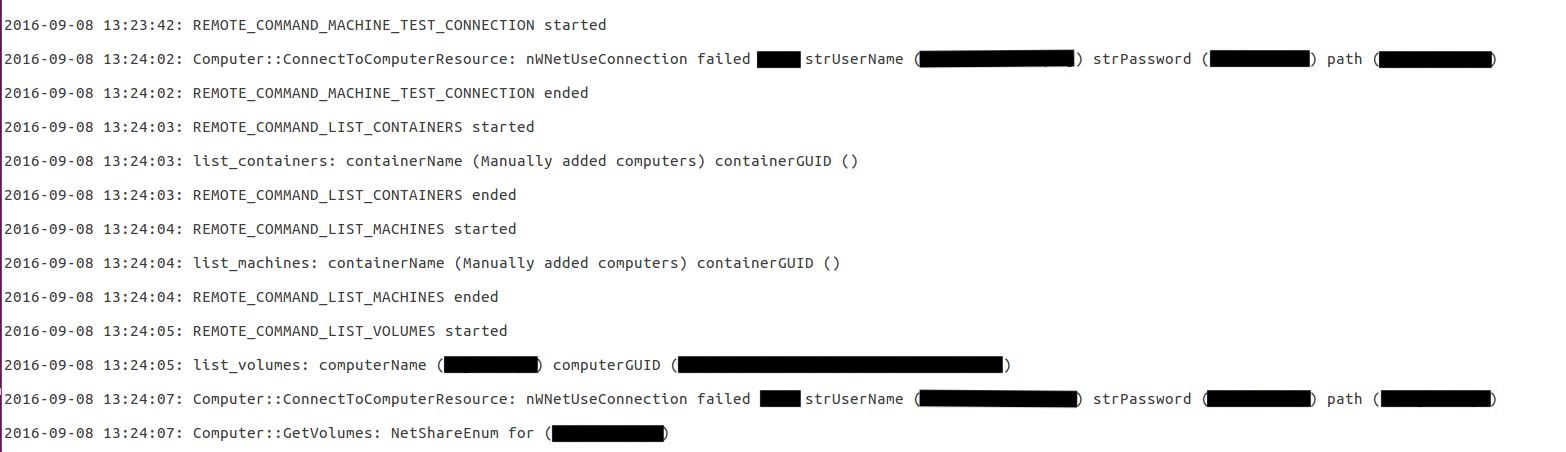
They were able to view users’ login credentials in plain text. In the image above, the censored text contained unencrypted administrator usernames, passwords, and users’ local computer name and GUID.
You can see an example of an email address exposed in the breach in the code here:

Through the leaked database, they were also able to view some information about users’ stored files. This included each file name, type, size, the date last modified, and the file path on the user’s local disk. An example of this can be found below.

Data Deposit Box isn’t the only cloud storage provider impacted by this. "Whenever a serious data breach occurs, it can have consequences for the entire industry. Competitors in the cloud storage services industry may find it more challenging to convince customers to trust them. These companies may need to do more to prove to customers that their service is truly secure," says the research team.
For the full report, visit the vpnMentor blog.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





