Call It a Transition
What is sure to be seen this fall at security industry conferences such as ISC East in New York City and ASIS International in Atlanta is change – more analytics software as well as networking. At the same time, some new technology will emphasize the concept of “at the edge,” where more storage and intelligence builds into the cameras.
A SHIFT TO NETWORKING
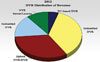
For example, research from MultiMedia Intelligence, the transition to networked video surveillance is driving a proliferation of product categories in the digital video surveillance market. Among the segments the firm identified in the DVR market are embedded DVRs, PC-based DVR, hybrid network video recorder (NVR/DVR), embedded NVR and NVR with network-based storage.Traditional embedded DVRs still dominate the overall video surveillance storage market, comprising 62 percent of the nearly $2 billion DVR market in 2007. However, growth has shifted to networked storage products. MultiMedia Intelligence expects the hybrid NVR/DVR segment, which supports both analog and Internet Protocol (IP) camera inputs, to be among the most compelling segments for chief security officers and other buyers.
“The hybrid NVR/DVR market reflects the broader surveillance market,” according to Mark Kirstein of MultiMedia Intelligence. “IP surveillance cameras are growing quickly, but will not supplant (more traditional) CCTV cameras any time soon. Both analog and IP cameras will co-exist for a substantial period of time.”
The NVR category is growing quickly as well.
However this segment is split between two sub-segments. The software virtualized NVR category largely reflects a software-based solution, as the hardware tends to be industry standard network storage equipment. The embedded NVR category features a stand-alone hardware NVR, much like the traditional embedded DVR form-factor.
OTHER CONCLUSIONS
- The DVR market is migrating to higher compression video codecs; MPEG-4 and H.264, as well a dual-codecs.
- Increasing channel counts, migrating from 4 and 8 channel DVRs to 8 and 16 channel DVRs
- While CCTV cameras are currently the largest semiconductor segment in the video surveillance equipment market, by 2012 DVR/NVR equipment will become the largest semiconductor opportunity.
SIDEBAR: Convergence Gains Traction
There’s no doubt that video surveillance systems and other edge devices provide an intelligent migration path to a network platform. For years, networked systems have proven to increase efficiency and productivity across many business applications, and are prevalent in our everyday professional and personal lives. The video surveillance industry is finally joining the network for a number of reasons – the most driving influencers being the simultaneous advancements in imaging technologies and IT-based disciplines. The “convergence factor” has actually gained traction.It has admittedly been a struggle for manufacturers of video surveillance devices to embrace the network domain as it involves a whole set of different technical parameters than they’ve been exposed to in a prior analog world, according to Frank DeFina of Panasonic System Solutions Company.
Early IP video products were entry-level products primarily designed to supplement analog-based systems for specialty applications. One of the biggest inhibiting factors even then was limited bandwidth to accommodate high resolution video with fast frame rates. Although bandwidth remains an issue for IP video systems, the implementation of large capacity networks with advanced new video surveillance and processing advancements like H.264 compression result in better bandwidth utilization and management for these edge devices.
New developments in CCD sensors, HD quality optics and improved bandwidth management greatly enhance image definition and overall image performance. As a result, cameras with smaller megapixel counts (for example 1.3 megapixels) effectively outperform their larger bandwidth hungry counterparts (cameras with 3 megapixels). It may seem to defy physics, but the results are clear. These new imaging solutions will further elevate the performance of megapixel cameras and ultimately increase the application of more sophisticated software capabilities.
Imaging advancements like these are the catalysts energizing the development of supplementary technologies driving the networking trend. Video analytics is a perfect example. New megapixel cameras provide volumes of detailed video data that allow video analytic middleware to perform more complex operations with greatly expanded policy-driven features. In addition to the surveillance benefits these applications deliver for live viewing, they also greatly improve forensic investigations of recorded images as a result of the amount of data recorded, and ability to mine data and metadata embedded in detailed video images.
True high definition quality IP cameras with minimal bandwidth requirements are the next systems breakthrough – one that will surely further accelerate the acceptance of networked systems. In the meantime, the security industry is living in a hybrid world with some users at either end of the IP and analog extremes. As a result, manufacturers must continue to push the envelope with new developments in systems products and technology that satisfy the wide range of end user needs. At least until the next new trend in video surveillance and infrastructure technologies sets the industry in a new direction.
SIDEBAR: Law Enforcement and Cost Savings
With the rising crime rates in Savannah, Ga, beginning to have a tangible impact on the safety of residents, tourists and the local economy, local government and law enforcement officials sought new solutions to their growing problem. Like many cities across the country, Savannah turned to public video surveillance systems as a counter measure. They selected Tropos Networks as the wireless broadband network vendor and their solution partners including On-Net Surveillance Systems Inc. (OnSSI).“Similar to Tropos, OnSSI is based upon industry standards which made them the ideal choice for this project,” said Denise Barton of Tropos Networks.
IP video cameras were installed in key locations throughout the city and connected to the Tropos MetroMesh routers to provide law enforcement officials with real-time video monitoring capability for crowd control and live viewing of suspicious or criminal activity around town. This capability has effectively reduced police response time without the need for additional law enforcement officers on the street.
Video from all cameras is recorded and delivered to users using OnSSI’s NetDVMS enterprise-class management solution software. In the control room at central command, OnSSI’s NetSwitcher enables instant access to video from any camera, which can be routed or automatically pushed on-event to any video wall monitor or networked PC. NetSwitcher eliminates the need for matrix switching hardware and allows full utilization of high resolution IP cameras by providing digital PTZ on live and recorded images. The system’s touch-screen user interface utilizes dynamic maps for intuitive navigation to sites, facilities and individual cameras, eliminating the need for camera codes or groups. This allows for efficient monitoring of the entire camera system by fewer operators, as well as faster training, leading to reduced manpower and operational costs. NetSwitcher also incorporates video content analytics for automated detection of exceptions, such as motion into restricted areas.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







