PCI Builds on Best Practices
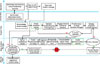
A sample process map for an incident.
Imagine explaining to your boss that Joint Terrorism Task Force agents will need a conference room in your facility and access to specific people, systems and records. Or say you take a phone call from the leader of one of your business units who tells you that a critical employee’s laptop -- an unencrypted one -- has been stolen. Or the systems operations manager calls you in the middle of the night to say that your data center is completely off all networks. Maybe it’s a worm or a virus, he’s not sure, but the network providers assure him that the circuits and routers are up and functioning.
These are things that happen to other people, right? I may have thought that once, but I’ve been in all three of the situations described above over the course of my career.
Thankfully, I’ve never had to experience the sinking feeling that comes with telling the CEO that I have no clue what my next step is going to be. Years ago, during my military service, I learned that Murphy really does rule: Whatever can go wrong, will go wrong. And today’s businesses and systems are so complex that it is impossible to remove everything that can go wrong.
So, how was I able to stand in front of my boss and know each time what my next step would be? Planning, plain and simple. You might call it an incident response plan, a contingency plan, an emergency response plan or something else altogether. Whatever you call it, it’s a plan to manage a crisis that has the potential to impact your organization – a plan that will save you when everything else is going incredibly wrong.
EMERGENCY RESPONSE AND BEST PRACTICES
Fortunately, there are best practices that we can use to build our plans. Having a best practices emergency response plan has prepared my organization to deal with a wide variety of situations and resolve them in ways that protected the organization, our data and assets, our employees and our customers to the best of our ability.There are quite a few different best practices to choose from, including the Hospital Incident Command System (HICS), the National Incident Management System (NIMS) or Carnegie Mellon’s Computer Emergency Response Team (CERT) practices, to name just three. Some are specific to certain industries, while others may apply more broadly across the business spectrum. You’ll have to choose which best practice to build upon by considering the best fit for your organization.
All best practices will require that you be prepared to do four things when faced with an emergency in order to return to normal operations and appropriately meet your mission of protecting and securing your organization.
- Report the emergency. Your organization has to know what constitutes an emergency and must have a means to report it to the person or team that can take action. You can’t afford to have a crisis brewing and not know it until it is beyond your ability to manage and control.
- Stabilize the situation. Once you know you have a problem, you need to declare an emergency, transition to crisis management and get the situation under control. It is critical that you stop the bleeding first. Then you can fix the problem.
- Remediate the problem. The firewall has to be returned to operation, the people whose data was on that laptop have to be notified – appropriate steps must be taken to mitigate the risk that this emergency represents.
- Analyze and improve. Once you have dealt with the emergency, you will need to analyze the root causes of your crisis and find ways to eliminate them. If you’re fortunate, this will uncover areas in which the organization can improve how it operates, perhaps gaining efficiency or demonstrating a greater level of due diligence to offset the negative impact of the crisis.
PAYMENT CARD INFORMATION BREACH
For many companies, the Payment Card Industry (PCI) Data Security Standard (DSS) will be the starting point for best-practices-based emergency response in information security. Like most regulations and mandates that require an organization to have good security practices, the DSS requires that governed organizations have an emergency response plan. Unlike many other regulations, however, DSS has real teeth in the form of sanctions and fines that can be assessed when you do not comply.The PCI Data Security Standard is all about pragmatic security best practices applied to the protection of consumer payment card data. If your organization accepts credit or debit cards for payment and processes those transactions, then you must take action in six categories to comply:
- Build and maintain a secure network
- Install and maintain firewall configurations
- Protect stored data
- Use and update anti-virus software
- Restrict access based on need to know
- Monitor and track all access to networks and card data.
COSTLY CRISES
Payment card data security breaches put the entire organization at risk. TJX, which reported a massive card data breach in January 2007, has taken a $12 million loss in a recent quarter, equal to 3 cents a share. And they forecast continuing losses of 2 to 3 cents a share in the future due to the breach. The Board, shareholders, CEO, CFO, and most operational leaders care deeply about losses like that.Further, if you are also subject to Sarbanes-Oxley, then corporate officers and the Board are personally responsible for having appropriate controls in place. If they don’t, the organization can face sanctions, fines and litigation that may cost millions, tens of millions or even hundreds of millions of dollars. The latest publicly available data from Gartner and Ponemon Institute estimate that information security breaches involving personally identifiable information costs an enterprise between $100 and $180 per record compromised. Therefore it is a critical element of appropriate enterprise risk management to have an emergency response plan for security incidents and make it an enterprise function.
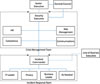
An example of the makeup of a crisis management team.
EXTEND THE PROTECTION FOR LITTLE EXTRA COST
Developing an emergency response plan to address the PCI Data Security Standards will require significant time and effort. Based on my experience, I’d estimate that it will take about 80 percent of what it would take to address your entire organization. You are going to need to gain executive sponsorship, create a plan, develop a team, and determine what parts of your organization and network the plan relates to. Given the potential cost and reputational impact of a PCI breach, you will need to invest in doing this right in order to mitigate those risks. For an incremental additional cost, you can build emergency response capabilities based on best practices that address your entire business.You can do this by starting at the more general level, and then applying your emergency response plans to your PCI requirements. Rather than creating a point solution that only addresses your PCI requirements, step back and look at all the regulatory requirements and risks that your business faces. Develop an emergency response approach that is broader and more general in nature. Then, within it, address any specific gaps from the PCI Data Security Standards. This approach will provide you with planning and preparation for a wide variety of emergencies that you may face, such as national security, network attacks, theft, and civil disasters. Since all of these broad risks also affect your PCI data, you are addressing your PCI requirements as well.
SENIOR-LEVEL BUY-IN
First, it is critical to establish emergency response plans and gain senior executive agreement and support. In an emergency, you will need to shut down systems, disconnect your networks, investigate employee actions, and purchase forensic services and identity theft services for your customers. You won’t be able to take these actions on your own, and you will not be able proceed without the highest levels of executive support. Before you ever face that emergency, with the necessary executive sponsorship, create a plan and a crisis management team, such as the team depicted in the sidebar.BEGIN CRISIS MANAGEMENT
The crisis management team needs to have the ability and authority to deal with a crisis. A crisis goes beyond a simple problem or incident – its scope can impact your entire organization. Consider the ChoicePoint or TJX breaches and the amount of money they have cost the companies, not to mention the public relations and legal impact. You will need a team of people who have executive authority and a broad range of skills, from business to security to legal to public relations, and potentially more.At the same time, you need people closer to the incident itself. These are people who can take effective action to identify the scope and magnitude of the incident, prevent further damage, and begin taking action to resolve it. They will operate under the direct control of the crisis management team, but are drawn from the part of the organization that is most directly involved with the incident. Again, a broad range of skills will be needed.
One final note. Have the crisis team report to the senior executive in charge under the direction and guidance of your general counsel or external legal counsel. This will protect your activities, to the greatest extent possible, under attorney-client privilege.
Fortunately for you, the PCI Data Security Standards are a natural lever to gain the sponsorship you require. Your senior executives are well aware that their business depends on processing credit card transactions, and they know what happened to TJX. They do not want to be on the front page of The New York Times. Nor do they want to tell shareholders, investors and Wall Street that a payment card data breach is costing the company 2 to 3 cents a share (or more) per quarter in expenses directly attributable to that breach.
EMERGENCY RESPONSE PROCESS MAP
Once you have sponsorship, you will need to define your processes and actions during an emergency. These must include how an incident is reported and categorized, how and when to declare a crisis, and steps to take to stabilize, remediate and improve the situation in order to return to normal operations when the emergency is over. The process map below is a good example. It’s derived from the actual process maps used by several enterprises that have dealt with security incidents successfully.Payment card risk must be managed at the most senior levels of your enterprise, including the board of directors. Board-level risks are risks that have the potential to damage the entire enterprise and/or the Board personally. Payment card security incidents, with their potential for significant financial and brand damage, constitute Board-level risk. If your Board is at risk, so are you. Make sure you have an emergency response plan and crisis management now, before the incident, so you aren’t standing in front of your CEO explaining that the enterprise is in crisis and you don’t know what to do.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





