Charting a Final Course to Master Planning

Master planning when it comes to security operations calls for specific tools that chief security officers need to have and use.
You have done a lot of work. You know where you are now. You know where you want to go. Now you have to chart the course to get there. This month we will look at the actual security planning portion of the master security plan.
MITIGATION
The first step is to understand what is meant by security. Security is the state of being secure or safe. The organizational function charged with maintaining that state of being creates an environment of security by applying measures of three security components.The first is physical security.
This is the basic brick and mortar application. The walls, the doors, the locks, the lights, etc. Essentially this is the component that is common to all facilities. All have a building of some sort. Was security part of the planning process when the facility was built? Probably not. Therefore, some measure of retrofitting may be necessary.
Next is technical security. This is the electronic “widgets” that make up the various systems that enhance the security of your facilities. The technical security systems can include: video surveillance and recording systems; access control systems using cards, PIN codes, fingerprints etc.; various intruder alarm systems, intercoms and emergency communication systems; as well as the control center that ties them all together.
Finally there is operational security.
THE OPERATION
This is the human component of the equation. While everyone immediately focuses on security officers as the primary embodiment of operational security, they are actually an additional resource to the operational security plan. The primary component in an operational security program is the employees, and to some extent, contractors of the organization. The visitors to your organization even have the limited obligation to acknowledge and submit to the operational security policies while on your propertyIt can be argued that there is a fourth component that should be included. That component would be information technology (IT) security. The computer and network systems move, store and process the informational resources of the organization. The same three components of security apply to the protection of IT. The tactical application of those components may be different. Many organizations have individuals or teams that are in place to address IT security. If you do, invite the IT security staff to be part of your planning team. If your organization does not have dedicated IT security professionals, be prepared to include the needs and concerns of the IT department in your overall plan.
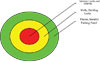
Planning involves looking at the facility in terms related to the layers of an onion.
TECHNIQUES AND TECHNOLOGIES
Your next task is to look at what security techniques and technologies will best meet your needs now and in the future. Look at your facilities and assets from the outside in with an eye toward building multiple layers of security. This concept has many names: concentric rings of security, security in depth, layered security, etc. The basic idea is to create multiple zones of security that will delay an intruder until help arrives, deter an intruder so that they reconsider their intrusion of your facility, and detect an intrusion so that mitigation actions can be taken.Acme Widget Manufacturing Company’s factory is located on a large tract of land in the suburbs. As a means of protecting their people, facilities, assets and information, Acme has implemented security-in-depth.
As you approach Acme you notice signs at the perimeter of the property that say “Private Property. You are subject to search by security personnel.” This is coupled with a fence and a security guard in a patrol vehicle driving through the parking lots.
Next Acme has entry doors that are staffed by security guards who control access to the facility. There are signs posted that list items that are prohibited in the building and all employees must wear a photo ID badge.
SPECIALTY AREAS
Finally, there are areas within the building that are important to Acme that are equipped with special locks. Even employees are restricted from entering these areas. Only those employees with an approved business reason are allowed in without an escort.At this stage, the plan will be directed toward the needs of the organization at the end of the plan’s life cycle, whether that is three years, five years, ten years or longer. Remember, the plan is a living document that can be adjusted as time marches forward to fit current needs.
After the final mitigation is complete, the planning team must prioritize the implementation of the plan. As stated earlier, very few organizations have the ability, or even the need, to implement the entire plan at once.
Perhaps you are creating a master plan for a school building in an area currently relatively free from crime. You want to be proactive by anticipating a need over the next three years to have surveillance system in place to create a secure environment for the students, faculty, and staff.
As we previously discussed, the plan will have sub plans to address the three prime components of security.

“Look at what security techniques and technologies will best meet your needs now and in the future,” advised Kurt Collins.
THE PLAN ACCORDING TO YEARS
The physical security plan is to ensure that all doors to the facility are in working order and ready to accept the upgrades to be called out in the technology plan. It will also address all of the issues related to the lighting around the facility to ensure that the cameras that are defined in the technology plan will work as desired.The technology plan is to have cameras at all doors and strategically located in the halls; ensure that only authorized personnel have access to the building and the public has the ability to use parts of the schools during non academic hours.
The operational components of the plan will address the staffing of the facilities by security personnel. The operational plans will also address security education and awareness of the non-security staff.
The first year of the plan may be:
- To repair all the doors so they close and latch properly.
- Install the infrastructure (cabling, some switches and some recording devices) for the video surveillance system.
- Install cameras to watch the primary entrances and public use areas (auditoriums, gymnasiums, etc.).
- Create security awareness program and present it to the employees.
- Install an intercom system so that visitors have to contact the main office before being granted access to the school.
- Hire guards to staff the main access points during business hours.
- Expansion of the video system.
- Installation of an access control system to eliminate the need to distribute and use keys as a daily access device.
- Expand the security guards to a 24 hour a day 7 day a week operation.
- Establish a security control center to control the video and access control systems.
- Expand the security awareness program to an annual event and publish a semi-annual security newsletter for the employees.
- Final expansion of the video system,
- Hire a security manager/executive to manage all aspects of the security operation.
- Reconfiguration of the main entrance to force visitors to access the school only through the office.
REVIEW
Congratulations! You have implemented your security master plan. But the process goes on. The plan will need to be reviewed on a recurring basis. The time frame is driven by the organizational dynamic rather than by any hard and fast rule. An annual review seems to work well for most organizations, but stay alert. If your organization experiences significant change, it might be time to dust off the plan early and take a look.During the review you will want to assess where the organization is on the original long range plan. Was growth better than planned? Worse? Or did the planners hit it on the nose?
How is security positioned to support the new organizational snapshot?
Since implementing the master plan, what has happened in the world to change the face of the plan? As we noted at the beginning, the attacks of September 11th radically changed the way the world looks at security.
REVIEW AGAIN
Now go back to your mitigation plan. Do you need to hire more security officers? What about cameras at the new facility downstate? Are you going to use the old headquarters building or sell it? What about upgrades due to newer technology?Make your adjustments and document the review.
You’ve made it. After many, often agonizing, hours of research and planning you have a master plan to guide you over the next several years and beyond. The implementation of the plan will have a positive impact on the reduction of security risk to your organization. Its implementation will make a positive impact on your ability to provide protection to your people, facilities, assets and information.
But remember, master planning is a process and the process has just begun.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







