Optimizing Intelligent Video Integration
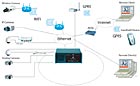
This diagram describes how an intelligent video solution operates as a balanced system. Different hardware and software components as well as number of analytics applications present new challenges for system processors and bandwidth consumption.
Video analytics-based systems test hardware processors, network bandwidth and hard-drive capacities in ways very different from standard digital video recorders (DVRs). As with any new technology, some basic questions must be asked to generate a clear understanding of each location-specific situation. There are some basic questions as suggested by Michael Zlatic of Arteco Vision Systems when considering intelligent video solutions (IVS).
Even more than standard DVRs, intelligent video solutions (IVS) requires a complete understanding of the job scope to insure the installation and setup process exceeds expectations with a limited number of surprises. The complete understanding has to do with managing the horsepower of the product and appropriately using where necessary. The limited number of surprises has to do with estimating processor use to accommodate the CSOs wishes, while also ensuring sufficient horsepower is provided to complete the task.
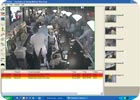
A first step is how many applications (analytics-based) will be activated on each video channel. Depending on customer requirements for violated areas, abandoned/removed objects, etc., the product must be configured with a mentality towards processor management.
PERFORMANCE NEEDS
Consider this analogy: An end-user wants to go from 0 to 60 mph in 4.0 seconds, but there are very few vehicles that can achieve this level of performance. The requirement should be for the performance to match the need. There is very little a technician can do to come close to “tweaking” out a 4.0 second 0 to 60 time with a Chevrolet Chevette. Like most things, IVS included, there is a limit to its capacity.First and foremost, a determination must be made as to how many applications (analytics-based) will be activated on each video channel. Depending on your requirements for violated areas, abandoned/removed objects, etc., the product must be configured with processor management in mind.
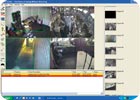
There are also bandwidth issues to consider when choosing the number of channels to be viewed on a live basis. Users can choose to actively watch the channels they deem most important, minimizing the overall effect on the network, while still receiving alerts from every camera. The preeminent IVS systems allow the user to control the rate of information transferred to remote client software sessions.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






