A Practitioner’s Perspective: An SOA Approach
Web services-based, service-oriented architecture (SOA) environment has opened up a whole new world of opportunities for enterprise security.
An identity-enabled SOA facilitates the establishment of a trust relationship among the three entities by providing a mechanism to resolve identities across organizational boundaries. It also supports comprehensive, end-to-end auditing of transactions not only between entities, but also among each of the entities like physical and IT security systems. Physical and IT security convergence is no longer a concept; it is a reality and a vital necessity not only for reducing systems integration and implementation costs, but also for improving overall enterprise security management.
SOA APPLICATIONS
There are many reasons for using a Web services-based SOA approach for supporting systems integration. Web services-based SOA utilizes platform-independent programming, languages and protocols like Extensible Markup Language (XML), Web Services Description Language (WSDL), and Hyper Text Transfer Protocol (HTTP). WSDL is the standard format for describing a Web service.
An increasing number of physical security systems like the video surveillance system are migrating to the enterprise network. However, there is still a wide range of physical and IT security systems that are based on non-interoperable software applications.
While IP network-centric convergence has brought voice, data and video together on the same network, the Web services-based SOA approach has brought about the convergence of physical and IT security systems by enabling systems integration at the application-level. The Web services-based SOA approach to physical and IT security systems integration provides a level of flexibility that was previously impossible and has many advantages over previous approaches. The key benefits of this approach, however, are code reusability, application-level interoperability, enablement of seamless information exchange and simpler systems integration.
The primary objective of the Web services-based SOA is to provide an interoperable framework for integrating loosely coupled software components associated with location-independent, back-end applications distributed over an enterprise network infrastructure. The Web services-based SOA approach reduces the dependency on proprietary components. It also reduces costs for implementing new systems and applications by facilitating the reuse of existing solution components.
Using the Web services-based SOA approach for integrating disparate, mission-critical systems and applications also significantly reduces monitoring, security event management and incident tracking costs. Physical security systems, such as IP network-based, digital video surveillance systems and intelligent video management systems are also beginning to use Web services to interface with other security systems, such as alarm management systems, smart sensor-based systems, such as perimeter security systems and gunshot detection system, explosives detection system, as well as, physical access control system. This integration enables the creation of an overall enterprise security solution that is responsive and fully capable of intercepting potential security threats and effectively tracking events that occur. A good example of the business benefit of such integration is monitoring the physical movements of personnel and environmental conditions within a data center.
The Web services-based SOA approach can be used for integrating smart sensor-based, data center environment monitoring system as well as digital video surveillance and intelligent video management systems with a mail server. This can help in sending e-mail and paging alerts regarding potential problems such as unusual movement of personnel, or problems discovered in temperature, air flow and other environmental conditions, over the enterprise network to key personnel who are responsible for managing physical and IT security. Since the messages are sent only when there is a potential threat, this can also help in reducing the monitoring and incident tracking costs.
SOA Components and Security Mechanisms
There are two basic types of Web services-based SOA components: providers and consumers. Web services providers and consumers can be edge systems (consumers), which initiates service requests and target systems (providers), which respond to the service request made by the edge system. In a typical Web services-based SOA environment, a target system in one instance may be an edge system in another instance.
A Web services-based SOA is an open environment that is highly decentralized in nature and allows service composition, which may involve many different service providers and consumers distributed across different platforms in the enterprise.
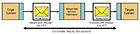
In such an open environment, a message may hop through various intermediaries (e.g., integration middleware) to reach the target system. This has certain security implications. To protect against potential vulnerabilities, the Web services-based SOA security requires a holistic approach that is based on a trust model. The trust model enables Web service providers and consumers - primarily physical and IT security systems - to interact with one another using a set of core services that provide the functionality necessary to support the model.
Figure 1 describes the message-level security mechanism in a Web services-based SOA.
The Web services-based SOA approach that is used for systems integration may involve a composite Web service that is basically built using multiple component Web services. A composite Web service supports a transactional application consisting of business functionality and information from various information sources.
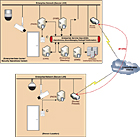
Using an Enterprise Service Bus (ESB)
The Web services-based SOA approach provides an application architecture framework. Figure 2 provides conceptual solution architecture of an integrated physical and IT security infrastructure implemented using an ESB-based SOA.
Web services-based SOA or an ESB-based SOA offers lower systems integration costs to meet the demands of evolving enterprises with changing business requirements. These approaches clearly provide the capability to integrate all aspects of physical and IT security, as well as facilities management, based on open standards-based architecture. With Web services-based SOA or an ESB-based SOA, a converged enterprise security environment can be created to enable organizations to effectively protect and manage their businesses.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





