Adding Surveillance Video to the IT Network
Security personnel are increasingly interested in moving traditional analog surveillance video systems onto corporate networks. By extending access to live and recorded video surveillance throughout the organization by authorized personnel, they can enhance the safety of employees and guests as well as the security of the organization’s assets.
In addition, by transforming surveillance from a system to a networked application, security operations can focus on safety and security while reducing costs. IT networks can lower costs, in part because the processes and resources already established by the IT department can be applied to the surveillance function. Among these are procedures for automatic equipment software updates, continuous monitoring and maintenance of storage and edge devices status, including connectivity.
Application availability can be improved with existing redundant system designs for disaster recovery and business continuity. The key for organizations to realize these benefits will be to unify IP-based video surveillance with infrastructure security. Achieving this integration requires the physical security group to partner with IT in addressing security issues holistically, allowing each group to focus on what it does best; in the case of physical security operations, that is ensuring the safety and security of people and assets.
When involved in such a convergence project, it is possible to run into some resistance from IT. After all, IT is understandably concerned about the performance, cost and information security implications of suddenly adding volumes of video content to the network, servers and storage systems.
Why the Interest?
With network-based surveillance, security personnel can view live and recorded video from any network-attached device throughout the organization. This keeps them on top of what’s happening in multiple places; officers are no longer physically restricted to viewing video from a limited number of monitors hardwired to a coax video system in a security control center. A network technology called multicast, along with advances in image compression algorithms, minimizes the impact of additional video on network bandwidth. Multicast essentially is a subscription-based broadcast to all authorized requesting parties. Rather than sending multiple copies of the same camera video through the network, which consumes additional bandwidth, multicast facilitates transmission of a single copy of the video through the network thereby reducing bandwidth usage.
With a fixed number of ports, matrix switches are limited in how many cameras they can support, and expanding them requires additional equipment and cabling. This has resulted in multiple surveillance “silos” throughout large organizations. By contrast, network-enabled cameras and recording/storage servers can easily plug into scalable and efficient IT network switches. With a packet/frame-based protocol, such as Ethernet, multiple camera streams can be aggregated at the edge of the network, which can then leverage the same single connection (port) for most of their transport over the IP network.
Network-based video also heightens security because it makes it possible to correlate information from other systems. For example, point-of-sale (POS) data can be linked to networked video so that the footage can be tagged and then scanned for transactions, such as refunds or “no sale” operations when cash register drawers are open. In other words, investigations can be conducted more quickly with event-tagged video.
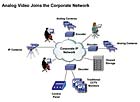
It becomes unnecessary to replace existing coax-based surveillance gear with the ability to send video from any camera to an encoder connected to the network. The encoder will digitize the analog video and network-enable it, even with old video control keyboards. Thus, you now have the ability to integrate different vendors’ proprietary surveillance systems so that they interoperate, using the IP network as the unifying platform (see figure).
Conclusion
It’s clear that the future of video is networked. The reasons are compelling: access to live and stored video at any time from any place and potentially lower capital and equipment maintenance costs. The transformation of video from a visual archive to an information resource means video can be integrated with the data mining and warehousing tools required by today’s security professionals. Making all this happen requires collaboration between the physical and IT security teams. A number of organizations have already begun walking the collaboration path.
SIDEBAR: Addressing IT Concerns
Concern ONE -- Security implications of video surveillance equipment on the network. While well designed IT networks and network devices (switches, routers, etc.) are highly secure, the IT team will want to understand the security capabilities of the surveillance equipment itself--cameras, encoders and storage systems. After all, these new network devices might be a target, or launching point, for worms, viruses or other malware that could impact network performance and deny service to corporate users. The IT group generally has policies that specify which systems can connect to the network and the level of security they need to meet.
In this case, it is important that the equipment has network security features that can pass IT’s vulnerability tests. If the supplier can demonstrate these capabilities, it will ease colleagues’ concerns about viruses and new attacks affecting the network.
Concern TWO --Storage requirements and associated cost could surge. Managing storage costs requires creating policies for necessary video storage and length of time the video is stored. Associating video with events will build rules for saving certain video based on correlations among the various events. This can significantly reduce storage requirements and associated expenses. Also, having storage managed by the IT group and leveraging their existing storage processes reduces overall storage equipment and management costs.
Concern THREE -- The amount of bandwidth, or network space, the video will consume. A single surveillance camera can generate 30-35 Mbps of raw (color, full-motion and uncompressed) video content. Adding video surveillance from hundreds of cameras to the network could overwhelm it. The added load could degrade network performance, create new management challenges for IT and require investments in additional network capacity.
There are a couple of solutions. First, conduct a threat assessment and situational analysis to determine the frame-per-second (fps) rate and resolution that needed for each camera. Second, choose an encoder or IP camera that will permit the frame rate and resolution to be set on a per-camera basis and one that will change either variable when a triggering event, such as “door forced” or “panic button pressed,” occurs. This will allow, for example, low-resolution 1 fps footage to switch to broadcast-quality 30 fps.
The right encoder will also allow a variety of video compression algorithms or codecs to be selected. The codec determines how the raw video is compressed (and decompressed) so that it uses less network bandwidth. Video encoders and decoders can use a high-quality MPEG-4 video compression technology that allows video streams to be switched over the IP network at up to full D1 resolution, and up to 30 fps, while consuming low bandwidth. Newer codecs, such as H.264, may provide additional capabilities for limiting bandwidth consumption.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






