CEOs Grade Security: Wished-for Attention, More Scrutiny

Google CEO Eric Schmidt must be really devoted to enterprise security. In recent SEC filings, Google reported Schmidt pulled in all of $1 in salary in 2006 but received personal security costing over $532,700.
Corporate security got a black eye in a Hewlett-Packard dustup when, in 2005 and 2006, some of its board of directors started the ball rolling on an internal investigation that turned external and allegedly involved wire fraud and “pretexting.”
And pity poor Carol Meyrowitz, TJX CEO, who is contending with probably the biggest identity theft ever. (See this month’s News & Analysis on page 12.) She and her executives are now working with internal security and outside firms as a result of the unauthorized intrusion into their computer systems. “We are working with leading computer security firms to investigate the problem and enhance our computer security in order to protect our customers’ data. We are dedicating significant resources to evaluate the issue. Given the nature of the breach, the size and international scope of our operations and the complexity of the way credit card transactions are processed, the evaluation is, by necessity, taking time,” she recently wrote to the TJX Web site.

CSOs score higher with CEOs on traditional physical security missions while they are weaker in business-centric needs.
GOOD, BAD, UGLY OPERATIONS
Then there is the security headache the Wal-Mart CEO is facing in what at this time seems a rogue investigation that employed scanning equipment to allegedly gather text messages from employees and others.Of course, there are the myriad stock options backdating and accounting scandals swirling around CEOs and their boardrooms. Former CA CEO Sanjay Kumar was recently slapped with a 12-year prison sentence and HealthSouth’s founder Richard Scrushy, convicted of bribery, now knows more about electronic security after a judge ordered him to wear a GPS-based monitoring device when traveling beyond certain distances.
CEOs and security; security and CEOs.
There is no doubt: chief executive officers are more knowledgeable and appreciative of their internal security operations. About 84 percent of CEOs polled by the security research firm Maddry Associates on behalf of Security Magazine say they are more involved in the planning, impact and effectiveness of their organization’s security operation today as compared to only five years ago.
But at some enterprises and for a diversity of reasons, “there are unfortunately some CEOs that still don’t know the name of their chief security officer or security director,” observed Gerald Brandt, president, Gerald T. Brandt & Associates. A long-time security professional with federal law enforcement and corporate security stints, Brandt now has an even more unique perspective on the relationship of CEOs to security by providing what he calls a “security executive on retainer” service for national clients.
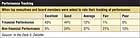
CEOs admit that it is more difficult to track non-financial performance, including security, as compared to financial numbers.
UNIQUE CEO POLL
To gain a specific understanding on CEO perceptions of security, Maddry Associates conducted a series of telephone and e-mail surveys with 100 chief executive officers and corporate presidents during a two-week period in early February 2007. Confidentiality was assured and individual responses were not identified by person or company.At the heart of the poll: 13 specific missions in which the CEOs were asked to grade their security operations with an A for excellent, a B for good, a C for average, a D for not as good as expected and an F for failure. While a few CEOs gave out F grades, when the 100 scores were added up, none of the 13 specific missions received less than a D. There is no surprise that CEOs polled rated their security operation high on elements such as securing property and protecting employees. But this may not be all good news, according to Brandt. “Especially when a security director has come up through the ranks in an organization, top management may have fixed an image” of him or her as patrolling the property and checking employee IDs.
In some areas where the chief executive may hold a more personal stake, protecting the brand, protecting confidential information and the supply chain as well as helping grow the business, CEOs scored the security operation lower.

Beyond theft and vandalism, more complex risks are threatening enterprises.
IN YOUR FACE ATTENTION
There are two actions CSOs and security directors can take in that case, advised Brandt. “Get in the CEO’s face; get face time with top management. Make your case as to your contributions in ways that match the chief executive’s concerns.” Warning of risks is one thing; demonstrating savings is another; but “getting the CEO to realize in a simple and effective way security’s many roles in the enterprise is quite another, and an even better approach,” according to Brandt.A second action to turn around the CEO, said Brandt and chief executives interviewed by Maddry Associates for the poll: Make true friends and partners within the enterprise.
“You have got to clearly understand the roles and dynamics among the CEO, the information technology department, the chief information officer (CIO) and security,” suggested Brandt. With technology jumping to the forefront of the security operation, security directors interviewed at the International Security Conference in Las Vegas in late March all pointed to IT as an influential colleague. “IT often gets more attention from the CEO because of the higher importance top company executives place in their dependence on information technology.”
Other external executives good for teamwork attention with the CEO include the human resources director, the facilities manager and the plant manager in the case of manufacturing enterprises.

While some believe that benchmarking will increase the ability of the CEO to measure non-financial performance, including security, other more essential obstacles include skepticism and the challenges of accountability.
WHAT ABOUT THE GENERAL COUNSEL?
The Maddry Associates research shows another important and up-and-coming team member who should be on the CSO’s radar: the general counsel (GC).According to a KPMG survey, a significant number of CEOs look at their general counsel as the company’s chief of police, especially when it comes to ethics and compliance issues. In some recent incidents, in which CEOs have gotten into legal or stakeholder trouble, the general counsel has been a “two-edged” sword, reported the Maddry poll debriefings. Their general counsel has led some top executives astray when it comes to authorizing investigations or the handling of stock options or perks. At the same time, more CEOs report they are turning to a combination of CSOs and GCs to educate their management on business ethics as well as embedding security and general counsel personnel more closely into company operations.
For Gerald Brandt, the bottom line for a stronger relationship between the CEO and security boils down to two words. “Trust and interaction, and not necessarily in that order. In some cases, the security director comes in thanks to a relationship of trust with the CEO. In other cases, interaction can help build that trust.”
Other research reports complement the Security Magazine CEO study.
In a second ground-breaking worldwide survey by Deloitte Touche Tohmatsu (DTT), conducted last December following a 2004 poll, the giant accounting firm found that “many senior executives and board members are still in the dark about the overall health of their organizations and have a lack of high quality non-financial data that they can act upon.”

When it does come to measurements, cost, threats and value are inherent elements.
DISCONNECT
“The survey reveals a critical disconnect between rhetoric and reality in the boardrooms and management circles of some of the world’s leading companies,” said Deloitte CEO William G. Parrett. “The attitudes of CEOs towards understanding the value of non-financial indicators and measuring performance against them are more positive now compared to the last survey (2004), but it seems executives and boards are not yet prepared to take the next step and act. The majority of companies said they are under increasing pressure to measure these indicators, but the quality of non-financial performance information they receive is inadequate to meet their needs.”The results of the second survey indicate that 57 percent of the companies surveyed are under increasing pressure to measure non-financial indicators, and that a growing number of companies are indeed creating significant value for their organizations by understanding their underlying performance drivers through the use of non-financial measurements. Customer satisfaction, innovation and employee commitment are identified as key drivers of performance among the companies interviewed. Further, 83 percent of respondents say that the market itself is increasingly emphasizing non-financial performance measures.
The challenge for chief executives relative to their security operation is similar to the ways CEOs relate to more general non-financial performance measurements.
By paying attention nearly exclusively to financial performance, according to Martin Carver, chairman, president and CEO of Bandag Inc., an American supplier of tire products, many boards and executive teams miss some important insights. The fact is, said Carver, “it’s the non-financial metrics that are probably more important than the financial metrics.” For example, “What drives your cash flow?” Carver asked. “It’s your employee commitment. It’s your customer satisfaction.” But the problem here, “is that those things are extremely hard to measure and even more difficult to promote or achieve.” Consequently, wrote Carver in the Deloitte study, many boards and management teams “have very little insight into some of the most influential processes in their businesses.”
Another defining study from The Conference Board, Navigating Risk – The Business Case for Security, aimed at determining how the business aligns with security.
The top concerns include complying with government regulations and protecting confidential information. Ironically, the Security Magazine/Maddry CEO study found that chief executives see more value in the performance of security with compliance than for protecting confidential data.

The security profession is diverse; but, according to the Security Executive Council, types range from practitioners to visionaries. Chief executives, depending on the corporate culture, see value in all of the profiles. Chart courtesy of Security Executive Council
SIDEBAR: Compliance and Ethics
The Security Executive Council, with top chief security officers involved, sees leadership value in providing Council members with information so they can work more effectively with CEOs and enterprise colleagues.The group publishes reports including one on Corporate Investigations for Business Conduct & Compliance Professionals.
The report relates that business conduct and compliance professionals are responsible for the corporation's business strategies, policies, standards and practices related to the organization's compliance and ethics function. One area on their watch is potential workplace harassment or other violations of their organization’s human resources policies. The need for conducting or assisting in an investigation might arise from an anonymous hotline call, a complaint to the security professional or another colleague in the company.
The value of assisting with or completing a proficient investigation is to save the company money and possibly brand reputation damage.
Typically business conduct and compliance professionals are asked to assist with the following employee-related investigations:
- Harassment
- Discrimination
- Employee theft
- Workplace violence
- Trade secrets
- Wage and hour violations
- Whistleblower
- Employee discipline
- Wrongful termination
- Employee vs. independent contractor status
- Business ethics or business conduct
- Insider trading or securities violations
- Mergers and acquisitions, including due diligence
- Compliance with law or organization policy
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





