Go Proactive for Healthcare Identity
The early days
Over the last five years, security has become increasingly more complex. Smarter viruses and worms, increasing malicious attacks, keyloggers, phishing and polymorphic spyware require security managers to take a more dynamic approach in protecting their organizations.Early security assessments and action plans were basic in nature. This was due to the fact that when these plans were written many of the security rules were not released. Therefore, there was no way to understand the exact level required to meet compliance standards. For this reason, security recommendations and implementations took shape as a proactive or reactive approach. Which plan took place depended on the vendor, their product and how well they convinced an already confused audience.
These two approaches served as a foundation by providing better security for organizations in the beginning as they increased security and security IT infrastructures compared to what many originally had. Because of the continuing increase in electronic and physical risks to organizations, sole dependency on one of these earlier approaches could present problems for the organization.
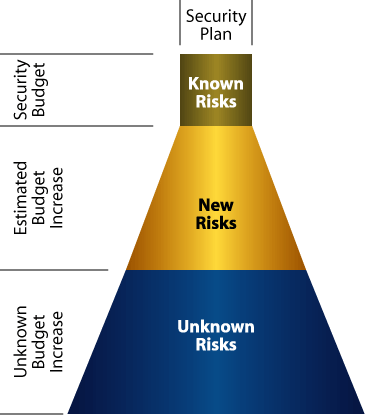
The Proactive Approach (shown in the chart here.) can also be known as a reverse funnel. This approach implements measures to prevent known risks before they occur. It can make it difficult to provide accurate returns on investment, since the investment is returned only if the known events occur. This model can have high cost of ownership if implemented and managed internally, since organizations have to support the cost of the hardware and software and employ qualified personnel to manage the environment. This approach also can prove difficult to smaller organizations that do not have adequate budgets to employ qualified multi-functional personnel to support a 24/7 operation.
The Reactive Approach depends on the implementation of a series of tools to generate a maze to slow down or prevent access to critical information. This approach may remove the use of certain early detection tools, such as intrusion detection, and depend more on off-the-shelf and manageable products. In addition to the cost of implementing the required products, this model has associated risk based on the fact that even if one event occurs within the maze, propagation rates within the network can prove to be a costly annoyance at best, or, at worst, a catastrophic event for the organization.

Dynamic security model
Even with baselines determined and many of the rules and deadlines now being finalized, unknown risks ensure that security models and HIPAA rules will have to remain dynamic. Today’s healthcare organizations need to implement a dynamic or adaptive security model to stay ahead of the continually changing security environment and requirements.
Healthcare organizations today can and should take advantage of all-inclusive services that will provide them with a controlled dynamic model. In implementing a dynamic model, the managed security services provider (MSSP) serves as a filter between the healthcare organization and the world. The MSSP provides a security utility infrastructure that provides services to generate forward-looking protection from known risks and serves as a barrier from potentially catastrophic events. Experienced providers are technology agnostic and work with pre-integrated products.
Summary
Today’s healthcare organizations can not afford to be unprotected, especially with the continued escalation of security threats entering the marketplace each year. Even though penalties for security violations will not start until after 2008, healthcare organizations must show diligence in protecting themselves today. Penalties of $100 per violation or a maximum of $25,000 per calendar year will not remove the direct impact for being reported as a non-compliant organization and could be overshadowed by the collateral damage caused from credibility loss or increased civil litigations. These risks are unnecessary for healthcare organizations, which need to concentrate their resources on their core competency by providing the best healthcare services available to their customers.Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





