Following the E-mail Trail

Who is to blame? Most IP thefts involve current and former employees.
The process of identifying security breaches often requires examining a variety of data and communications sources – from databases and network systems to laptops and personal digital assistants. Most valuable among all such sources is e-mail because it is a time-stamped, first person account of the sender’s statements and actions.
The automatic capture of e-mail communication in messaging systems creates a natural record of critical messages, conversational context and inherent communication patterns. It is a goldmine of information – but only the most progressive organizations are able to effectively access, analyze and benefit from this valuable data source.
The new haystack
E-mail has become the number-one source of evidence in corporate investigations, comprising more than half of all evidence. Yet, most e-mail investigations are conducted using labor-intensive methods that are expensive, inconsistent and often incomplete.It is estimated that each year a typical Fortune 1000 company will conduct more than 25 investigations in response to internal matters, more than 15 in response to litigation, and more than 10 in response to regulatory inquiries. Large corporations make these numbers seem small by comparison. For example, a Fortune100 technology company recently indicated it has received over 50 lawsuits so far this year.
This activity is fueling the rapid growth of the Electronic Discovery market, which will swell more than 40 percent this year to $1.5 billion. In addition, it is estimated that corporations will spend over $4 billion in 2005 in expenses related to internal investigations and e-mail analysis.
Despite the fast changing pace of e-mail messaging systems management, there is good reason for companies to jump on the E-Discovery bandwagon: e-mail analysis can be well worth the effort in uncovering fraud, protecting corporate images and deriving value from a natural data source.
The true security value of e-mail is its ability to be more revealing than traditional sources of information. E-mail is packed with data – information such as temporal attributes, attached documents, sender and recipient data, and a wealth of other metadata. This complex level of information produces more usable and reliable evidence than traditional paper sources.
E-mails are also usually more candid and accurate than other sources (e.g., individual’s own memory of events and facts). The conversational tone, patterns of communication and spontaneity of e-mail often give evidence a contextual background that is likely to produce a more complete picture of events surrounding an investigation. This information is far more powerful than data found from search engine results, standard paper trails or personal interviews.
Sifting through the stack
To take full advantage of the abundance of data inherent in e-mail evidence, security needs to be able to quickly locate and analyze relevant information. However, current methods are inefficient and fail to leverage the qualities of e-messages that make them so valuable.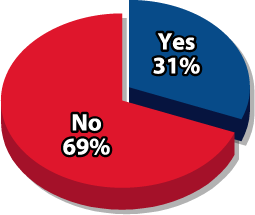
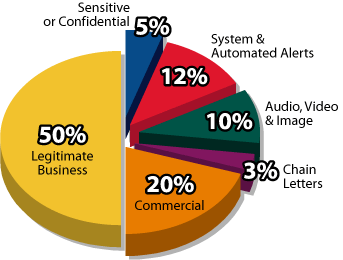
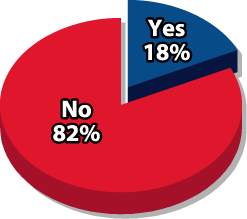
within a Spam Message (other
than unsubscribe?
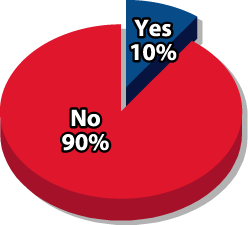
or Service as a Result of Spam? Source: Radicati Group & Mirapoint survey, March 2005
Survey from The Radicati Group and Mirapoint find end-users still engaging in bad email behavior. (PRNewsFoto)
However, monitoring and investigation are two separate issues. Finding suspicious e-mail triggers an investigation of the parties involved. This investigation requires the retrieval and analysis of a large number of historical e-mails to fully understand the situation and events. Monitoring technologies are not applicable to retrieval, investigation and analysis.
Search Technologies – Most organizations are now able to do simple searches to locate suspicious e-mail. But these searches are not analytical; they offer only a narrow view of an organization’s intellectual capital.
Search technology provides haystacks, but leaves it up to investigators to find the needle. Important evidence may be buried within enormous search result lists. These lists contain individual messages without any context or broad perspective of the overall information obtained. Users must also know in advance the exact terms to search for, which causes much evidence to go undiscovered.
Right mix of technologies
The next stage in the evolution of e-mail analysis will produce solutions that fully leverage the rich content and metadata in e-mail. In order to do this, unique and intelligent combinations of multiple technologies will be required. Merging diverse aspects of specialized search techniques, messaging systems, scalable computing architectures, guided navigation and multi-dimensional visualization of the analysis will result in a powerful new blend of essential investigative capabilities.With current methods, a company investigating fraud may turn to traditional search techniques. But what if the perpetrators are using evasive code words?
Traditional search tools would not readily identify these patterns and related terms. However, an intelligent software application that can search for and automatically analyze similarities, relationships, temporal contexts and other important connections within large volumes of e-mail would be able to identify the suspicious code words and link people, documents, events and other information relevant to the investigation.
In addition to being thorough, an effective e-mail analysis application must be usable. Even if a solution is well rounded, offering deep layers of analysis, the technology will not be adopted unless non-technical employees and investigators can be guided through the discovery process and directed to relevant information. Users must also be able to visualize the big picture, i.e., an application needs to be able to present its findings – such as relationships between people, time, events, documents and communication patterns – in a straightforward, understandable way.
Most importantly, e-mail analysis can no longer function as an outsourced service. With the types and sources of electronic evidence expanding, a comprehensive e-mail discovery solution must be able to collect, retrieve, preserve, process, analyze, review and produce evidence directly from a wide variety of enterprise content sources.
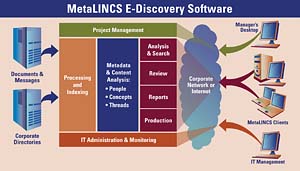
Sidebar: A Software Investigation
Analysis is the most critical aspect of the e-discovery process, yet most organizations continue to rely on manual reading and searching. The right analysis tool can cut investigation time and costs in half and produce more reliable and successful outcomes.MetaLINCS, a startup in Mountain View, Calif., recently released its E-Discovery application, a software application that automatically guides users through the discovery process for electronic messages. The software algorithms quickly analyze e-mail data sets and visually represent relationships between people, events, time and communication patterns, thereby expediting the discovery of relevant evidence in the correct context.
The application combines a diverse set of innovative features, including:
- Core Discovery – Processing, indexing, search, review, reporting and production.
- Visual Analysis – Presents visual message analysis of concepts, people, events,
time and communications patterns.
- Thread Analysis – Organizes all of the messages in a thread along with
all related threads.
- People Analysis – Groups e-mails based on both an individual and a topic,
and visually shows communication patterns, which helps reveal unexpected
participants in conversations.
- Related Concepts – Dynamically suggests additional key words and phrases
to analyze, ensuring a more complete investigation.
- Dynamic Directory – Automatically categorizes results into eight dimensions.
- Collaboration Folders – Queries and results can be organized, saved in folders, annotated and shared by investigation teams.
- E-Document Acquisition Engine – Extracts documents and messages from
diverse sources; normalizes, categorizes and indexes information; integrates
additional metadata from corporate directories.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!


