Covergence: Encrypt that E-mail

With the constraints of regulatory compliance and the inundation of phishing and pharming attempts, corporate security executives, IT administrators and end users now seek solutions to protect the security and privacy of their e-mail. Solutions for encrypted e-mail are plentiful. But how does one match their needs with the most suitable solution?
End users must decide if they should be exploring ways to protect sensitive information through encrypted e-mail. It is even more important for e-mail messages sent among security personnel or from security to others be better protected, too.
Many vendors provide e-mail assessment services as an up-front way to introduce them and to help assess vulnerabilities in e-mail communications. Whether free or fee-based, an e-mail assessment can provide quantifiable statistics on the number of messages in a mail stream that contain sensitive information and need to be sent securely. They may also use content-filtering techniques that search for language specific to each specific industry.
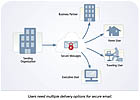
Interoperability options
Security working with IT will likely need to determine which domains that secure e-mail needs to be sent and received from, and decide if they need to exchange encrypted messages with trusted partners and suppliers. If so, they should look for a vendor with a solution that supports interoperability with other vendors’ solutions.A vendor’s solution may be based on several encryption methods or protocols (See Figure 1). Asymmetric, public key or PKI, systems often use PGP, TLS or S/MIME in their solutions. Common symmetric data encryption algorithms include 3DES, AES or RSA, which can be used within a public key solution. As a result of the many and varied methods of cryptography, many solutions are proprietary. The three-letter acronym that a solution is based on is important, but not more so than the features it provides.
Those who need to exchange secure messages with corporations that already have an e-mail encryption solution should look for a vendor that meets the interoperability standards defined for S/MIME, TLS or PGP. These full-featured gateway solutions provide for exchanging secure messages with partners and suppliers who have implemented another vendor’s solution. Messages may be decrypted at the gateway at the edge of a network and delivered plain text with a branded footer describing how the message was secured.
Transparency is key
User transparency is a key requirement for corporate-wide systems. End users should look for a system that uses corporate-wide policies implemented by their IT security administrators. Corporate-wide policies scan e-mail and attachments before they leave the mail server to verify if they contain sensitive information that needs to be encrypted. Users can depend on the system to decide when messages should be encrypted.These systems will add a footer to the message, indicating that it was secured by the sender for the protection of the recipient. While this is reassuring for both sender and recipient, decrypting secure messages on the part of the end user can become burdensome.
For business-to-consumer needs, end users should look for a solution that is easy to deploy and easy to use for recipients. Decrypting a message always involves a password, a key or both. The less complicated the encryption process is for the recipient, the greater the level of acceptance.
Retrieving messages from a Web portal over a secure link such as SSL is a widely accepted solution. If requiring users to log into a Web portal introduces too much uncertainly (e.g. fear of phishing), some vendors are now able to push encrypted messages directly into the recipient’s inbox.
Encrypting at desktop
In addition to encrypting and/or decrypting at the gateway, mail server and portal, some individuals will invariably require the highest level of security and flexibility, a desktop-to-desktop capability.When developing corporate-wide e-mail encryption policies, administrators typically must find a balance between policies that protect sensitive data within a range of industry-specific terms and the needs of individual employees within the company. With content-filtering policies, end users can meet the regulatory requirements for encryption of e-mail messages containing sensitive information. While these corporate policies will protect sensitive data, there will be individuals within the organization who have different needs not met by these general policies.
Specifiers should look for a provider with a solution that meets the needs of both types of users. For example, senior executives and users in finance and human resources may need to be able to ensure that specific messages they send are encrypted. This may be provided by a separate e-mail encryption method that is beyond the corporate-wide policies. These senders will need to download client software that gives them the power to encrypt (and decrypt) on demand. A user-specific encryption capability should be integrated within the overall corporate-wide solution.
Evaluating tradeoffs
The higher the level of security, the more complex it can be for users, support staff and IT administrators. Client software on the user’s desktop provides the highest level of security, but users become responsible for items like private key management, password management and downloading the latest version of the client software.While issuing thousands of messages to subscribers in a secure portal is efficient on the sending side, security staff must ensure that subscribers are informed up front about the security of the portal. IT can provide easily accessible online or live support if users have questions about the method of delivery or lose their login credentials.
For server-based solutions with corporate-wide encryption policies, end users should ensure that the content-filtering techniques are flexible and can be customized to the terminology that is specific to their industry. Those who can fine-tune their policies and the lexicons used by the search engine can achieve a higher rate of accuracy in selecting messages that do need to be encrypted, avoiding the high false positive syndrome.
Furthermore, those who understand the needs of their employees, customers, partners and subscribers, matching them to a choice of e-mail encryption solutions will be a successful and rewarding endeavor.
Links
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!



