Mantraps: A Unique Solution
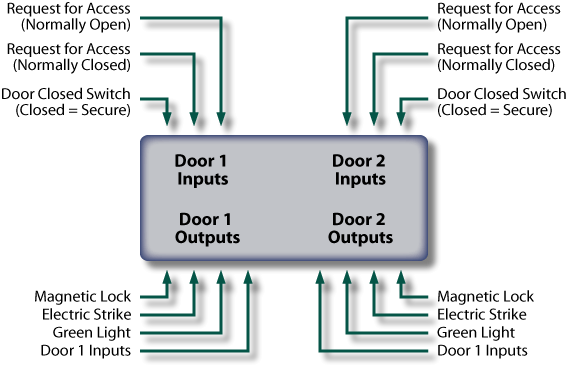
Mantraps limit access to secure areas within a facility while providing an effective means to physically detain unauthorized persons until security provides clearance. In its most basic form, a mantrap is comprised of a set of doors that requires the person to enter the first while the others are closed. Mantraps are typically manual swing doors forming a vestibule but can also use sliding doors or gates. Some mantraps use turnstiles or revolving doors.
Once inside the first door, the person cannot pass through the second door until the first door is closed.
This system provides security in at least three ways. It makes it difficult to forcibly gain entry by knocking down a single door; it allows time to evaluate the person in the mantrap before releasing him or her through the second door; and it allows entry of only one person at a time.
In large scale systems such as those found in casinos, healthcare facilities, government installations and large financial institutions, as many as 99 doors can be configured into a single massive mantrap system. The programmable nature of such large systems provides system designers and integrators with the flexibility to implement complex systems involving dozens of rooms and safe areas.

Typical mantrap configurations
There are a few basic mantrap configurations for different levels of applications.Mantrap systems employing air lock control are generally designed for minimum security applications where all of the doors in the system are normally unlocked until any door is opened. Once any door is opened, all other doors in the system automatically lock. This configuration provides easy entry or egress with no access wait time, but is the least secure as two or more doors may be opened simultaneously. Typically, this design incorporates door position switches to control the mantrap system.
Secure entry/free egress mantraps are more secure, allowing a faster method of egress through a combination of locked and unlocked doors. Exterior doors are normally secured and interior doors normally unlocked. A card access system controls entry from the exterior and an R-E-X device is used on the interior of the outside door. A valid access card will unlock the exterior door only if the interior door is closed. Unlocking the exterior door will lock the interior door. Once the exterior door is re-secured, the interior door is unlocked to allow access into the facility. Opening the interior door prevents the exterior door from being unlocked.
Restricted entry and exit mantrap systems provide the highest level of security. With all doors in the system locked, a door can only be unlocked by making a request for access if any other door in the system is unlocked. As a result, opening any door keeps all other doors secure. The more secure mantrap systems will buffer simultaneous requests for access to prevent two or more doors from being unlocked. The best designs use lock monitoring sensors in lieu of door switches.

Complex examples
A hospital recently used a Dortronics Systems (Sag Harbor, N.Y.) 4400 series mantrap control to limit access into the mental health areas. A vestibule with 1100 series magnetic locks and magnetic bond sensors on the interior and exterior doors secure the floor entry. Access is authorized through the key switches on each side of the secured doors. The mantrap controller prevents the second door from being unlocked while the first door is unsecured. A door prop alarm is used at every secured door to insure that each is properly re-secured after an authorized access. Each door is also monitored in the security office by a Dortronics 7600 annunciator/controller that will sound an alarm if the doors have not been re-secured in the allotted time period.A pharmaceutical manufacturing facility employs a mantrap control to insure a sterile environment. Magnetic locks with door position switches are installed on 2-door mantraps. While the doors are normally unlocked, the mantrap controller will lock the opposite door when any door of the mantrap is opened. The second door can only be opened after the first door has been closed.
Some facilities use a manned security station to monitor and control the mantrap entry. Opening an exterior door would lock all doors. A security video/intercom can monitor request for access. After viewing the individual requesting entry, security personnel can release the outside or inside door to allow entry into or out of the facility. Once the security vestibule is cleared, security then resets the system, unlocking both interior and exterior doors, ready for the next user. This configuration is also being used in conjunction with a card access system.
Several newly constructed casinos use a field-programmable mantrap controller with a card access system to provide secured entry into the money counting areas. These complex systems utilize magnetic locks with magnetic bond sensors and strikes for redundant fail-secure locking. Visual indicators are also supplied for traffic control. The systems are field programmable to allow for any number of secured rooms with multiple doors and may be adjoining with shared doorways between rooms. The systems are easily programmed without the need of ladder logic or other computer language knowledge using a simple dumb terminal emulator. Once enabled, the mantrap controllers monitor the status of doors and requests for access, allowing only one door to be unsecured at a time in any room.

Sidebar: More Alternatives? From Turnstiles to Exit Buttons
The University of Pennsylvania has almost 24,000 students located primarily within the 270 acres. Access control is a priority. For example, the University’s Harnwell House and other buildings have to be prepared for the thousands of students that use the facilities daily. Integrator SST of Norristown, Pa., realized the importance of campus safety and security. The university chose proximity card readers in six lanes of Port Washington, N.Y.-based Automatic Control Systems’ PNG390 ADA accessible Optical Portals. The prox cards act as student ID and dormitory access. To unlock the high glass barriers, that cannot be climbed over or crawled underneath, a student swipes his or her card at the front of the portal and it opens allowing just one person to enter.
Another solid access alternative is a control station that can handle myriad of devices and designs. DKS interior control stations from DoorKing of Inglewood, Calif., for example, can be installed into a single-gang electrical box. Lighted exit buttons provide free exit while key switch and keypad devices control entry through doors with electric or magnetic locks. Gate control devices provide manual operation and control of automated vehicular gates.
For More Information
Information for this article came in large part from Bryan Sanderford of Dortronics Systems, Inc., Sag Harbor, N.Y. More details at www.dortronics.com. Information on DKS stations from DoorKing, Inglewood, Calif., at www.doorking.com. Info on Automatic Controls Systems, Port Washington, N.Y., at www.automaticsystems.com. Also visit the Security magazine Web site at www.securitymagazine.com and use the LINX service, powered by Google, to get even more background on alternative electronic access controls such as mantraps, turnstiles and control stations.Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





