Central vs. Distributed
Centralized architecture means that the control panels, associated power supplies, input, output and reader control modules for each access device are located in a central location. Distributed architecture requires the associated power supplies, input, output and reader control modules be installed in close proximity to the access device. Assuming components are of equal quality, either system will provide the same performance capability and reliability.
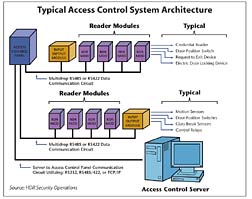
Most access control system components connect to a door access control panel via a multidrop RS485 or 422 serial communication circuit. Due to the technical capabilities of this communication protocol, the access control device can locate several thousand feet away. This bridge is common to both centralized and distributed access control system architecture.
An example of a centralized architecture: an access panel in a locked and secure room – common practice in many typical commercial buildings. The advantage of the centralized approach includes the ability to monitor and/or control personnel who enter the room. This limits the accessibility to the critical data communication circuits between the door access control panels and control modules. It also enables a service technician to troubleshoot the electronic components at a single location.
The disadvantages of the centralized architecture include the routing of all circuits associated with the devices controlling the door. These circuits could include: card reader, door contact, request to exit device, lock power or any other input/output device specified to operate with the system. Depending on the number of reader locations, this could equate to a large quantity of cable required to manage a single location.
Advantages of remote or distributed architecture include the reduction of cable quantities required from the door access control panel to the remotely installed control modules. Minimal lengths of multiple-conductor large-gauge peripheral cable are needed. The reader control module would generally be installed in a locked, tamper switched enclosure above the finished ceiling on the secure side of the controlled door, which provides convenient troubleshooting and testing of the controlled door.
Distributed Approach
Distributed architecture is also convenient for adding a remotely installed control module onto an available data communications circuit, to minimize the installation costs of potentially long cable runs back to the access control panel location.As with the centralized method, the remote installation or distributed method also has its disadvantages. These disadvantages include the necessity of a device location plan, and the potential damage from construction trades or building maintenance. Each service person must know the exact location of the remotely installed control modules, eliminating the need to hunt through a customer’s ceiling and potentially damaging fragile finished ceiling components.
Construction trades or building maintenance staff performing work in an area adjacent to communication circuits could damage these components. Damage to the data communications or power circuits supplying the control modules could prohibit the control and monitoring of the peripheral devices from the point of damage. This would result in an interruption of security coverage in the affected area, requiring an emergency response from a service technician to repair the damage and restore the system to normal operation.
Both centralized and distributed access control systems have their advantages and disadvantages. The access control design professional can be a valuable asset in determining which system architecture is best suited for the operation and maintenance philosophy of the system owner.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






