Utilizing data analytics in physical security
The increase in use of technology and the Internet of Things (IoT) in the security industry has led to the generation of massive amounts of data points each day. From smart interconnected systems to access control, surveillance and incident management systems, technology can produce powerful insights and guide security teams’ data-driven decision-making. To combat new and existing emerging threats, security professionals must be proactive in identifying security gaps and risks using data analytics.
The story
The tale of pursuing data analytics’ utilization in the security field started with an experience, led to a hypothesis and ended with validated research findings. With a degree in Information Systems and experience working in both healthcare and banking industries as an analyst and later as a network engineer, data was always a critical asset. Upon transitioning to the physical security field, utilizing data and creating specific metrics to measure operational effectiveness was indisputable, but it appeared to be a new phenomenon amongst many of my security professional colleagues. This experience became evident when I led and directed a security metrics program implementation several years ago for a Fortune 100 company.
The implementation included the rollout of an incident management system (i.e., applications such as dispatch, incident reporting, investigations, task management and guard tours), data collection and analysis and data visualization. Data utilization by many of the security professionals was truly a new phenomenon and the skill gap was apparent. At times, there was even a strong resistance to implement a security metrics program from many security leaders.
The hypothesis
The question emerged; is the security industry lagging in integrating data analytics into their daily operations and translating quantitative data into practical insights? This is a study I conducted at the University of Southern California while pursuing a doctoral degree in Organizational Change and Leadership. The study focused on security professionals with a lens on skill gaps and assets. The research explores knowledge, motivation and organizational influences (KMO) to identify assets and needs impacting the utilization of data analytics in the field of physical security.
The study was guided by three research questions:
- What is the security professionals’ knowledge in the context of using data analytics to inform data-driven decision-making?
- What is the security professionals’ motivation in the context of using data analytics to inform data-driven decision-making?
- How do the organizational context and culture either facilitate or hinder their efforts in implementation and use of data analytics?
Purpose of study
The purpose of this study was to evaluate the utilization of data analytics by security professionals in the field of physical security. Upon conducting the literature review, scholarly sources supported the hypothesis that security professionals lack effective utilization of data for process improvement, risk mitigation and to inform their decision-making.
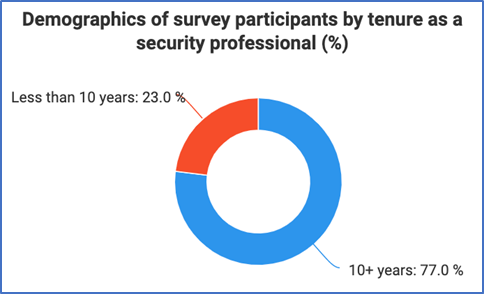
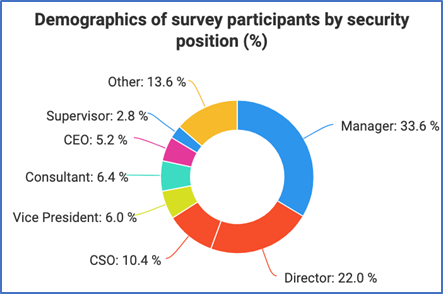
The study used explanatory sequential mixed methods including surveys and interviews. Survey data was obtained from over 250 security professionals from the United States and 43 other countries globally. Additionally, data from seven security professionals was obtained through interviews. Security professionals were recruited using various security organizations, including the ASIS Connects community of global security professionals. The participants represented various positions such as manager (33.6%), director (22%) and Chief Security Officer (CSO) (10.4%), among other security positions, and 77% of respondents reported more than 10 years of experience in the security field.
Results and findings
The study found three key findings impacting security professionals’ slow adoption of data analytics through triangulation of both quantitative and qualitative research data. The three key findings include inadequate data analytical skills (Procedural knowledge); lack of motivation to engage in data collection and analysis (Self-efficacy); and provisioning of resources (Cultural setting).
Knowledge influence
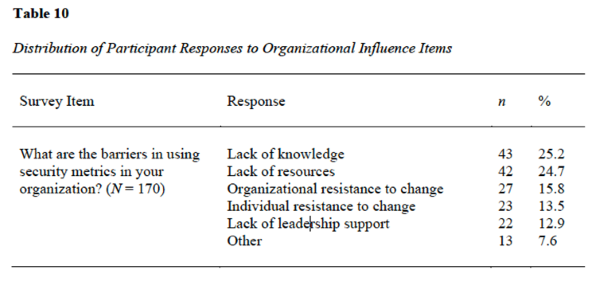
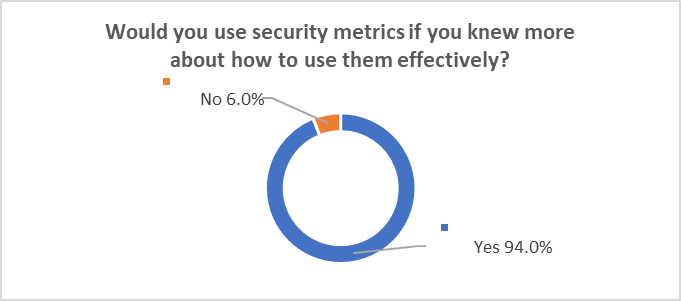
When asked to identify barriers in utilization of data, security professionals reported knowledge and resources as the two main barriers in their profession. Additionally, 94% of security professionals who currently do not perform any form of data analysis reported they would utilize data analytics if they knew more about how to use them effectively.
Security professionals’ responses to additional knowledge items indicated various levels of familiarity in utilization of data analytics. Security professionals were asked to indicate their familiarity level with the below survey items related to data analytics:
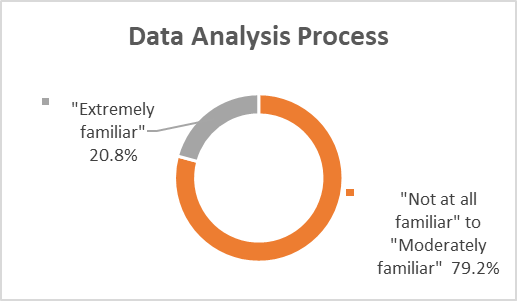
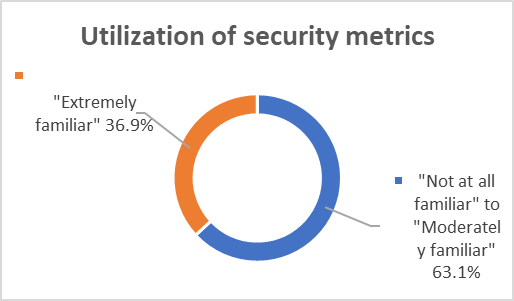
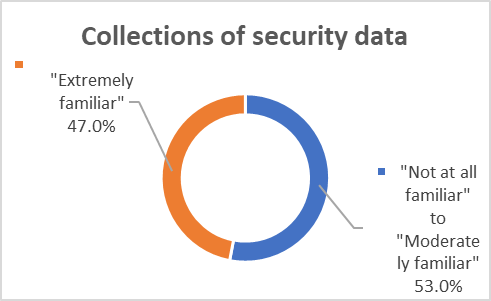
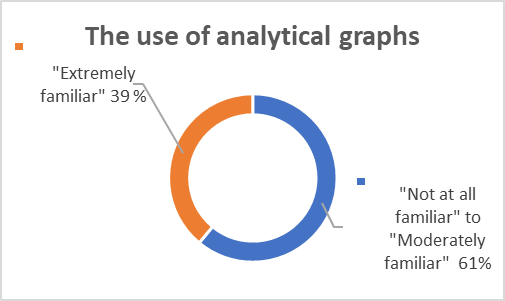
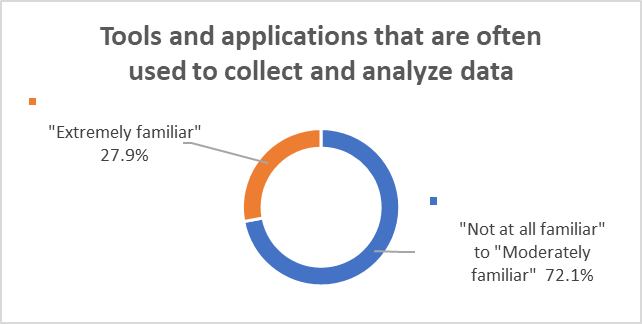
Motivation influence
The self-efficacy-related survey items measured security professionals’ motivation in utilizing data analytics. Security professionals (71.1%) reported they were “not at all confident” to “moderately confident” in their ability to perform data analysis, while only 28.9% reported they were “extremely confident” in their ability.
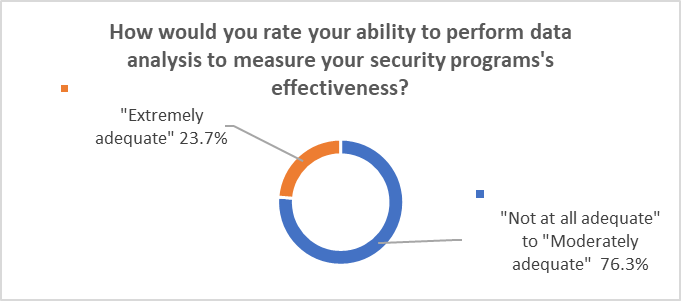
Similarly, 76.3% of security professionals reported their ability to perform data analysis to measure their security programs’ effectiveness as “not at all adequate” to “moderately adequate,” while 23.7% reported their ability as “extremely adequate.”

As illustrated below, 94% of security professionals reported they would use security metrics if they knew how to use them effectively, while only 6% of participants reported they would not engage in use of security metrics. Data suggested that an overwhelming gap in knowledge exists for those security professionals who do not currently perform data analysis, therefore hindering their self-efficacy.
Data also suggested that security professionals perceive high utility value in using security metrics to inform their decision-making process. Over half of respondents reported security metrics would be “extremely likely” to inform their decision-making process, followed by 42.4% of participants who reported security metrics would “likely” inform their decision-making process. Similarly, 56.3% of respondents reported they would be “extremely likely” to attend a training program on security metrics if one was offered by their organization, followed by 37.2% reporting they would likely attend a training program on security metrics, stressing security professionals’ high utility value in utilizing data analytics.
Organizational influence
Security professionals reported that the organizational climate provided support for utilization of data analytics. Data suggested the level of support was even higher for those security professionals who currently engage in utilization of data. Additionally, most security professionals (88.4%) either “agree” or “strongly agree” that their organizations’ leaders are supportive of utilization of data analytics, compared to 11.7% who either “strongly disagree” or “disagree” regarding the same issue. This result highlights strong leadership support for the utilization of data analytics and finds that leadership support is not one of the barriers to utilization of data analytics by security professionals.
Recommendations
Security professionals do not need to be data scientists, but they should strive to be data champions within their organizations. To be a data champion, the skill gaps identified in this study should be addressed using adequate training and resources. Using data, security professionals can tell a better story of the state of security within their organizations. Such intelligence can lead to proactive risk mitigation, effective program management and places the organization in a place of advantage when facing new threats.
Security leaders should also insert the “utilization of data” in their conversations with their teams and hold their vendors and security contractors accountable for provisioning data to gain business intelligence within their respective areas. Leaders should also ensure access to data analytics training is available and incentivized for their teams.
Kiron and Shockley posit that organizations reside in three stages of analytics utilization cycle: aspirational, experienced and transformed. Organizations in the aspirational stage use data analytics sparingly or, at times, not at all. Organizations in the experienced stage utilize data analytics as a tactical tool. However, strategic impact of data analytics to the organization and change is limited. Transformed organizations utilize data analytics to its full potential and are able to change their business as needed. Many security organizations live in the aspirational stage and must lead their teams towards the experienced and, ultimately, transformed stages.
There are several recommendations outlined in this study. A few of those recommendations include:
- Develop security professionals’ data analytics skills
- Enhance security professionals’ motivation to engage in the collection and analysis of security data
- Provision adequate resources to support security professionals in their data analytics journey
To read the full study and further recommendations, click here. View results in infographic form here.
All graph and table images courtesy of Farhad Tajali
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







