OWASP updates top 10 security vulnerability ranking

The Open Web Application Security Project (OWASP) has released an updated draft of its ranking of the top 10 vulnerabilities. The draft release marks the first changes to the list since November 2017.
The OWASP Top 10 — primarily an awareness document — has been used as a de facto industry standard since its inception in 2003.
In this update, AppSec Labs, GitLab, Micro Focus, Sqreen, Cobalt.io, HackerOne, PenTest-Tools, Veracode, Contrast Security, HCL Technologies, Probely and WhiteHat (NTT), along with some anonymous donors, donated data for more than 500,000 applications to make this release the largest and most comprehensive application security data set.
So, What’s Changed for 2021?
According to OWASP, this installment of the Top 10 is more data-driven than ever — but not blindly data-driven. OWASP selected eight of the ten categories from contributed data and two categories from an industry survey at a high level. It takes time for AppSec researchers to search for new vulnerabilities and different ways to test for them, and the process of integrating into various tools and processes can be quite lengthy.
To continue to mature the Top 10 — which takes several years — OWASP implemented a couple of category changes to offer additional training benefits as companies can focus on CWEs that make sense for a language/framework, OWASP says. There are three new categories, four categories with naming and scoping changes, and some consolidation in the Top 10 for 2021.
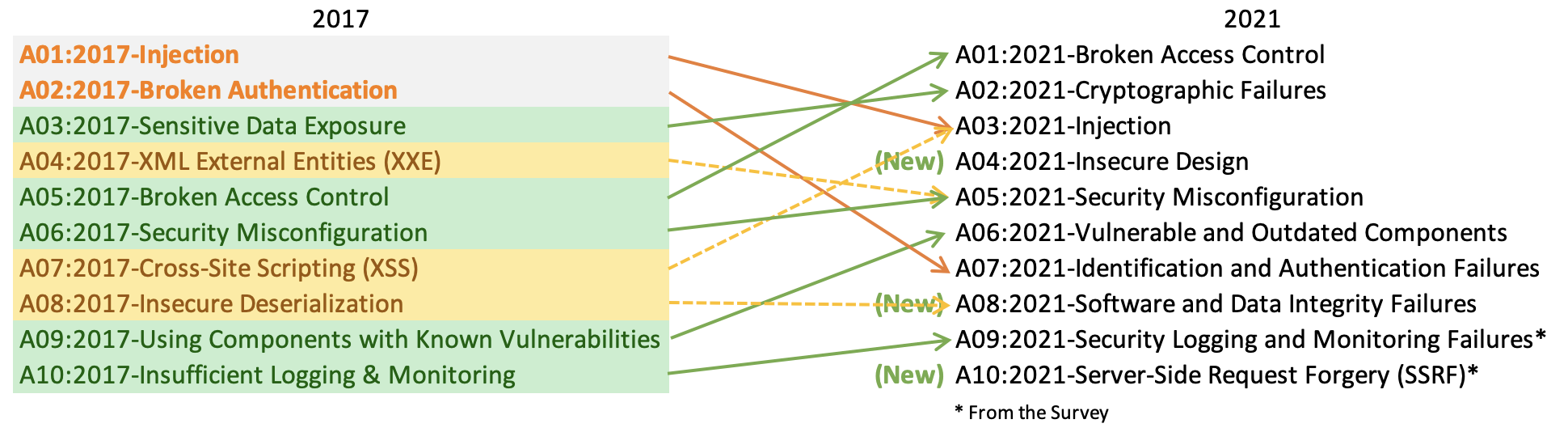
Image courtesy of OWASP
The Top 10 List
- A01:2021-Broken Access Control moved up from #5. Ninety-four percent of applications were tested for some form of broken access control, and the 34 CWEs mapped to Broken Access Control had more appearances in applications than any other category.
- A02:2021-Cryptographic Failures shifted one position to #2, previously known as Sensitive Data Exposure, a broad symptom rather than a root cause. The renewed focus here is on failures related to cryptography which often leads to sensitive data exposure or system compromise.
- A03:2021-Injection slid down to the third position. 94% of the applications were tested for some form of injection, and the 33 CWEs mapped into this category have the second most occurrences in applications. Cross-site Scripting is now part of this category in this edition.
- A04:2021-Insecure Design is a new category for 2021, with a focus on risks related to design flaws. If the industry genuinely wants to “move left,” it calls for more threat modeling, secure design patterns and principles, and reference architectures.
- A05:2021-Security Misconfiguration moved up from #6; 90% of applications were tested for some form of misconfiguration. With more shifts into highly configurable software, it’s not surprising to see this category move up. The former type for XML External Entities (XXE) is now part of this category.
- A06:2021-Vulnerable and Outdated Components was previously titled Using Components with Known Vulnerabilities, moved up from #9, and is now #2 in the industry survey. It had enough data to make the Top 10 via data analysis. This category is a known issue that security developers struggle to test and assess risk. It is the only category not to have any CVEs mapped to the included CWEs, so a default exploit and impact weights of 5.0 are factored into their scores.
- A07:2021-Identification and Authentication Failures was previously Broken Authentication and slid down from the second position. It now includes CWEs that are more related to identification failures. This category is still an integral part of the Top 10, but the increased availability of standardized frameworks seems to be helping.
- A08:2021-Software and Data Integrity Failures is a new category for 2021, focusing on making assumptions related to software updates, critical data and CI/CD pipelines without verifying integrity. One of the highest weighted impacts from CVE/CVSS data mapped to the 10 CWEs in this category. Insecure Deserialization from 2017 is now a part of this larger category.
- A09:2021-Security Logging and Monitoring Failures was previously Insufficient Logging & Monitoring and is added from the industry survey (#3), moved up from #10. This category is expanded to include more failures, is challenging to test for, and isn’t well represented in the CVE/CVSS data. However, failures in this category can directly impact visibility, incident alerting and forensics.
- A10:2021-Server-Side Request Forgery is added from the industry survey (#1). The data shows a relatively low incidence rate with above average testing coverage, along with above-average ratings for Exploit and Impact potential. The category represents the scenario where the industry professionals show this is important, even though it’s not illustrated in the data.
Commenting on this year’s update, Tim Wade, Technical Director, CTO Team at Vectra, a San Jose, Calif.-based AI cybersecurity company, notes he always appreciates and respects the tremendous work OWASP does advancing the state of application security.
He adds, “It’s noteworthy to see the continued generalization of categorization, merging attacks that are tactically unique but share some conceptual tissue. Additionally, I applaud the modest bump of the importance of Security Logging and Monitoring. In some respects, this reflects further maturation in the software security space that recognizes application security is not strictly self-contained integrity within the app but incorporates an application’s capacity to accurately and actionably communicate its state outward.”
Although there has been much discussion about the overlap between the Top Ten risks, by definition of each (including the list of CWEs), there isn’t any overlap, OWASP says, but conceptually, there can be overlap or interactions based on the higher-level naming, as shown below.

The Venn diagram represents the interactions between the Top Ten 2017 risk categories. Image courtesy of OWASP
Ben Pick, Senior Application Security Consultant at nVisium, a Falls Church, Virginia-based application security provider, says, “The OWASP Top 10 is not intended to be used for compliance purposes, but it is often looked at in this manner. The listed items are meant to drive awareness of trends across the industry regarding vulnerabilities and exploits faced by the companies who volunteered their data — particularly for those who may not have a security background. Overall, this living document matches the risks I have observed within various assessments, and I will continue to use this resource to learn about new types of threats. The OWASP Top 10 is still in draft form and will be edited and improved as more of the security industry reviews the content.”
Editor's note: All data and findings belong to OWASP.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




