Defending Against Ransomware: The Growth of Targeted Attacks
Ransomware attacks are getting bolder and affect enterprises of all sizes.

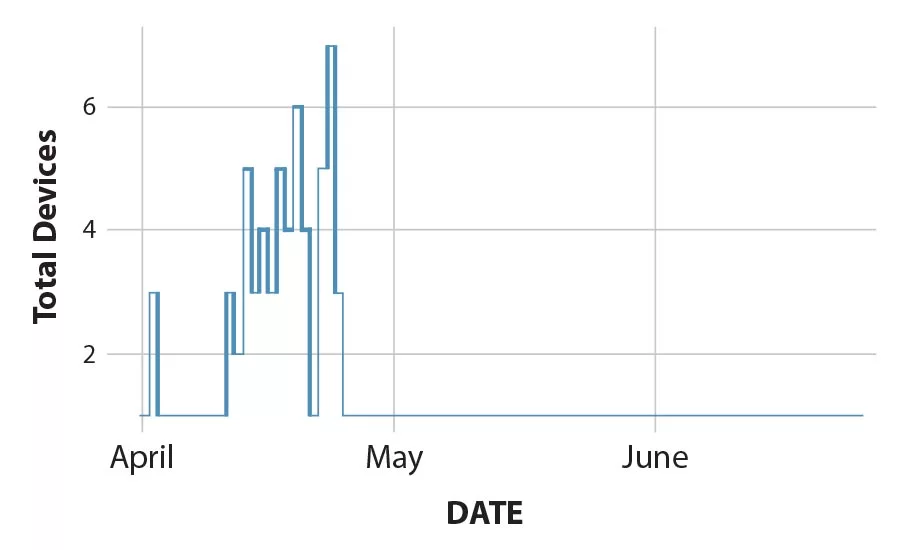
Figure 1: Devices detecting Ryuk variants
The evolution of ransomware attacks continues a trend in which cybercriminals are moving away from mass-volume, opportunistic ransomware attacks and are focusing their efforts on enterprises that they believe will pay their ransoms. To make this even more likely, they are adding focused attack strategies that include deep reconnaissance and targeted payloads, such as pre-selected detection evasion strategies, to ensure their attacks are particularly effective and damaging to the enterprises being targeted.
Ransomware continues to play a significant role in the cyberthreat landscape, as reported in Fortinet’s Q2 2019 Threat Landscape Report.
Current Applications of Ransomware
Multiple different ransomware attacks have made recent headlines. An example includes the attack on the city of Baltimore, which disrupted critical services for weeks and forced government officials to set up manual workarounds to handle real estate transactions, utility payments, property taxes and more critical municipal functions. Baltimore officials, acting on the advice of the FBI, refused to pay the approximately $100,000 the attackers wanted as ransom and ended up spending more than $18 million on recovery efforts. For this series of attacks, cybercriminals used a ransomware variant called Robbinhood.
Analysis of Robbinhood shows it was designed to attack an enterprise’s network infrastructure, and based on detailed analysis of it attack trajectory, it is most likely being distributed using weaponized remote desktop applications. In addition to encrypting and holding data for ransom, this malware’s capabilities also include disabling Windows services that prevent data encryption and disconnecting from shared drives.
Ryuk, which surfaced last year, has also been used in recent attacks. It uses several evasion tactics, including destroying its encryption key and deleting shadow copies on an infected system. Researchers have primarily linked the use of Ryuk to targeted attacks, and the low number of detections in Figure 1 supports that position. This malware is likely being distributed via spearphishing or brute force attacks on RDP services.
These and many other ransomware attacks noted last quarter are all part of a trend that began last year. Cybercriminals are continuing to move away from mass-volume, opportunistic ransomware attacks and are increasingly focusing their power on enterprises that they perceive as having both the ability and the incentive to pay big ransoms.
It’s also common in these targeted attacks for cybercriminals to have already gained access to their victims’ network, and used that time to conduct considerable reconnaissance before deploying their ransomware on carefully selected systems. As a result, some report a sharp increase both in the average ransom payments that enterprises are making to get their data back, as well as in disruption-related costs.
Another new ransomware variant called Sodinokibi (aka Sodin) surfaced during the second quarter of 2019 that may become a major threat for enterprises this year. Functionally, Sodinokibi is not very different from a majority of ransomware tools in the wild. What makes it troublesome is that it exploits a recently announced critical vulnerability that allows for arbitrary remote code execution.
The impact of this could be severe because an unpatched system with this vulnerability can get infected without the victim doing anything to trigger it.
While investigating Sodinokibi, researchers encountered the newly discovered Nemty ransomware. It has an artifact embedded in its binary that the GandCrab ransomware also used, and it is being distributed using the same method as Sodinokibi. Nemty contains some irregularities that led investigators to believe that it is still in its early stage of development.
Nemty ransomware uses a combination of AES-128 in CBC mode, RSA-2048 and the unusual RSA-8192 for its file encryption and key protection. The strings used throughout Nemty’s execution are obfuscated using a combination of simple base64 encoding and RC4 encryption. To express their unsurprising animosity towards the security industry, this variant used a vulgar RC4 encryption key.
Best Practices for Today’s Security
As ransomware and other forms of destructive malware grow in sophistication and volume, there are practical security measures you can take to protect your enterprise:
- Have a copy of critical data and resources stored off-network on a separate device so that operations can be restored and resumed if a ransomware attack occurs. Backup systems regularly, scan backups for infection and run data restoration drills so that recovery from an attack is routine and predictable.
- Prioritize regular patching and update operating systems, devices and software. Consider automating patching processes. Upgrade systems that are no longer supported by the manufacturers. And for those systems that cannot be patched or updated (i.e. IoT and similar devices), make sure that adequate proximity controls are in place along with intent-based network segmentation to limit the scope of a compromise.
- Ensure network and device antivirus, IPS and anti-malware tools are running the latest updates. Just as importantly, also ensure that they and other security tools can share real-time security intelligence to ensure that they can launch a coordinated response in the event that such a threat is detected.
- Analyze email attachments, websites and files for malware with professional email and web security tools that can block potentially compromised advertisements and social media sites that have no business relevance. These tools should include sandbox functionality so that new or unrecognized files can be executed and analyzed in a safe environment.
- Create and enforce a BYOD security policy that can inspect and block devices that do not meet standards for security (antivirus files are out of date, client or anti-malware is not installed, operating systems need critical patches, etc.).
- Use application whitelisting where possible, especially on devices with a limited scope of function, which prevents unauthorized applications from being downloaded or run. This is especially critical in OT environments.
- Segment networks into security zones to ensure that an infection in one area cannot easily spread to another.
- Use the policy of “least privileged.” Create and enforce permission and privilege to ensure that the fewest number of users have the potential to infect business-critical applications, data or services. Use this same strategy for hardening and controlling embedded software, such as PowerShell, that are increasingly being hijacked in order to hide malicious behaviors inside legitimate traffic.
- Implement forensic analysis tools so that after an attack, you can identify:
- where the infection came from.
- how long the threat has been in the environment.
- what other devices may have been impacted.
- that all threats have been removed from every device.
- that you can ensure the threat doesn’t come back.
- User awareness training is also critical to ensure that employees know not to download files, click on email attachments, or follow unsolicited web links in emails. Empower them with knowledge, training and education.
A New Security Strategy
Ransomware isn’t going anywhere. In fact, it’s becoming more targeted – and, therefore, more effective against enterprises. And while this trend is certainly concerning, ransomware is just one example of the types of focused, recon-based attacks that are possible today.
Such attacks make security more challenging than ever, but victory is possible. Use the best practices listed above to create a security posture that protects the network on all fronts without slowing down critical applications and services.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






