Stop the Abuse! (Of Your Cybersecurity Team)

Can you imagine if the head designer at Mercedes-Benz was asked to change tires? Or if an army general was expected to sit at a screen for hours at a time and track the movements of one spy? They would be out the door before you could say “HR”!
But this is what many organizations are effectively doing to their senior security analysts. CCIE’s – analysts with the highest network expert certification – are spending hours a day sifting through network logs, as are Networking experts, Cloud experts, Microsoft OS experts, application experts and other valuable employees.
What these hard to find and recruit team members SHOULD be doing is coordinating and managing all the expensive security assets at the organization and dealing only with real security alerts and threats.
Even if you assume that your analysts and security engineers – senior or junior – are willing to sift through the mountains of logs without reaching burnout after a few months – how effective is what they are doing in protecting your network? Unfortunately, not very.
Because the performance and costs of SIEMS can often be a ‘black box’ to security teams, and even rise unpredictably with time, tools such as an ROI calculator can help organizations assess the effectiveness of their current SIEM – or the one they are contemplating purchasing.
For example, if you are a mid-sized organization with 4000 hosts and three full time security analysts, using Logrhythm, you are reaching below 10 percent of all the logs and alerts the system asks you to examine. This means your network is highly vulnerable to attack.
If you were to try to achieve 100 percent coverage in this scenario, it means one of two things:
- Asking each analyst to work like 10 analysts (the reality is frightening), mostly on logs of course and not the real important stuff.
- Hire more analysts – very expensive. In this case the overall annual software and all associated operational costs would be a whopping over seven million.
To better understand how ROI is calculated, check out the diagram below that explains the concept:
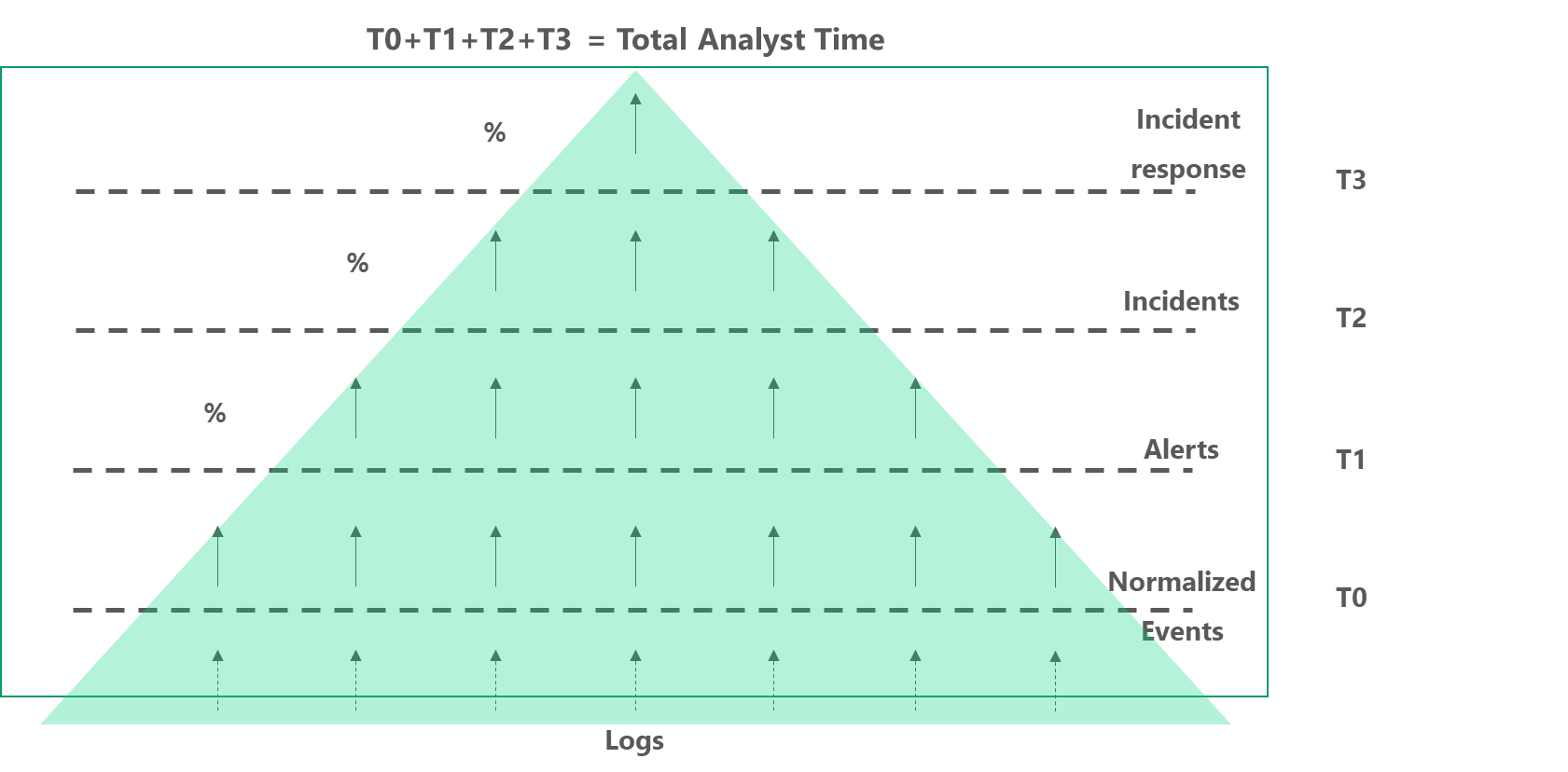
The diagram shows the process of analyzing a log from multiple data sources and calculates the work that needs to be done at each stage (T represents the time spent in each stage):
- T0: Time spent writing testing and debugging raw logs parsers and normalization rules, which are required for creating effective alert rules
- T1: Time spent writing and tightening alert rules, as well as analyzing the alerts
- T2: Time spent writing and maintaining correlation and investigation rules, analyzing rules results and prioritizing incidents that are of real interest to the organization
- T3: Time spent analyzing the prioritized incidents, creating a response plan and executing it
The above diagram illustrates what security professionals intuitively know to be correct – that having analysts sit down and analyze mountains of logs, in the bottom of this cyber data pyramid, is not only frustrating for them, but ultimately ineffective for the organization.
Using AI and NLP algorithms is one solution that can help to finally release this bottleneck. NLP – or Natural Language Processing - is a field in artificial intelligence has been progressing rapidly in the past couple of years, for speech and natural language understanding. In the cybersecurity context, NLP can allow to automatically classify signals into potential attack stages, tactics and techniques. The result is that these algorithms can replace much of the manual correlation writing tasks of security analysts, bringing to their attention only those attacks which an NLP based platform has judged to be significant threats to the organization, saving them loads of time and making their work more meaningful and effective.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








