Rapidly Deployable Beyond-the-Fence Detection
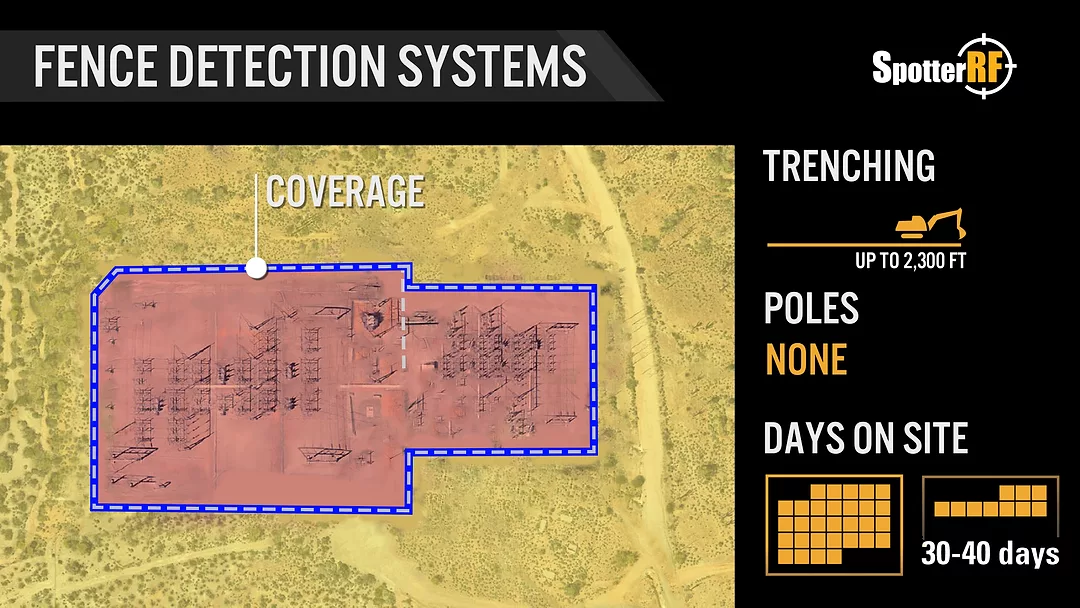
Graphic A: Fence line sensors can provide adequate coverage at the fence, but up to 2,300 feet of trenching (white dashed lines) is required to bring the sensors to the fence. Graphic courtesy of SpotterRF

Graphic B: Thermal cameras can be a simpler perimeter security solution, especially when analytics are included, but they can be timely and expensive to install. Graphic courtesy of SpotterRF

Graphic C: Compact Surveillance Radars (CSRs) can be combined with PTZ cameras to detect and track threats in a shorter installation time. Graphic courtesy of SpotterRF

A FLIR thermal camera combined with SpotterRF Compact Surveillance Radar is being used at this substation control house to monitor for intruders. Photo courtesy of SpotterRF
Physical protection of electrical substations is much more critical than simply guarding against copper theft. Recent terrorist attacks on substations and the potential for simultaneous attacks across the U.S. put the entire country at serious risk for major power interruption. Detection devices such as fence sensors, thermal cameras, microwave and passive infrared (PIR) motion sensors all provide some warning against such attacks, but are all limited in their ability to detect threats outside the fence line, and take months to deploy at each site.
In the last five years a new technology, Compact Surveillance Radar (CSR), has emerged to fill that gap by providing wide area coverage (10 to 100s of acres of volumetric coverage) in a small lightweight sensor (< 5 lbs) that is simple and quick to set up using existing infrastructure.
CSR operates on the same principles as all radars, but its compact size makes it simpler to install and less expensive to utilize. When someone walks into the field of view of a CSR, the radio waves bounce off the person and back to the CSR, which then calculates the precise GPS location and size of the target. The radars then tell the camera to zoom to that location. The camera automatically stays on the target, moving with and tracking it. Because the radars control the cameras, the cameras only move upon detection, which significantly extends the shelf life of the cameras and allows them to last for years without replacement.
CSR, when integrated with PTZ cameras and IP communications, provides early-warning detection and identification of threats both inside and outside the fence line.
While other technologies have attempted to solve the substation security problem, each has disadvantages that make it less practical than a radar/camera solution.
While fence line sensors provide adequate coverage at the fence line, up to 2,300 feet of trenching (white dashed lines in Graphic A above) is required to bring the sensors to the fence and to break the fence into at least five zones.
This means that four to six weeks are required for installation, making this a costly option. And after all of that, the sensors provide detection only, meaning that a camera system must be installed to provide identification of threats.
Thermal camera systems are a somewhat simpler solution, with the identification included in the video analytics (see Graphic B above). However, thermal cameras are again costly and time-consuming to install, and inclement weather – including rain and fog – can cause them the cameras to malfunction.
Because compact surveillance radars have such large coverage areas, the CSRs and the PTZ cameras are mounted right on the control house (see Graphic C above). The radars detect and track the threat and automatically cue the camera on target for identification and continue to follow the threat no matter where they go.
The installation is so simple that it typically requires less than two weeks to complete. The CSR/Camera system delivers all weather, wide area coverage at a fraction of the cost of alternative technologies.
Our critical infrastructure is worth protecting at any cost. Carefully evaluating and weighing the costs and benefits of any security solution is vital in ensuring the protection of power stations, dams, bridges and other vulnerable areas to ensure these assets are kept safe from vandals and terrorists.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





