Utilizing Biometric Single Sign-On for Stronger Data Security
Single sign-on (SSO) is a biometric identification management system that allows end users the ability to provide their biometric credentials in place of a password, token, or personal identification number (PIN) as a secure method of system or database access. SSO systems provide secure access to sensitive data and bring flexibility to identity management, fully integrated with Windows Active Directory and are readily available for large enterprises, healthcare organizations, financial service institutions, or any government entity. Traditional passwords are potentially the weakest link to information security systems for these organizations and with an increasing number of data security breaches due to weak passwords and inadequate network and data encryption systems, many organizations are considering deploying biometric SSO solutions using either fingerprint, finger vein or palm vein authentication for secure password and identity management.
Biometrics are unique traits or behavioral characteristics that can be captured and used for individual identification through a host of different biometric modalities such as: fingerprint, finger vein, iris, facial or voice recognition. Biometrics are unique to every human on the planet, even identical twins have different biometric physiological characteristics. Due to their high level of identification accuracy, security and usability biometric SSO solutions are considered “next generation” personal identification solutions to reduce data security risks and potential loss of intellectual capital.
Why Are Data Security Risk Financial Losses Rising?
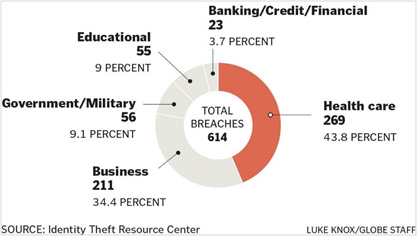 The risk of data security breaches in industries such as financial services, healthcare, and government are rising fast and often result in serious financial loss, loss of confidence, and damage to brand reputation. In a survey of more than 3,900 companies worldwide, it was found that the cost of lost financial data ranged anywhere from $66,000 to $938,000 per organization, depending on the size. Most data security breach cases are the result of internal threats rather than external cyber security risks. Weak passwords, unsecure identity management, and lack of proper monitoring of who is accessing data is often the root cause of data security breaches in almost all types of organizations. Cyber-attacks are also rising as cyber criminals are now using more advanced techniques to easily break down traditional password based security systems. The following are examples of industries that are particularly susceptible to suffering financial losses due to data security problems:
The risk of data security breaches in industries such as financial services, healthcare, and government are rising fast and often result in serious financial loss, loss of confidence, and damage to brand reputation. In a survey of more than 3,900 companies worldwide, it was found that the cost of lost financial data ranged anywhere from $66,000 to $938,000 per organization, depending on the size. Most data security breach cases are the result of internal threats rather than external cyber security risks. Weak passwords, unsecure identity management, and lack of proper monitoring of who is accessing data is often the root cause of data security breaches in almost all types of organizations. Cyber-attacks are also rising as cyber criminals are now using more advanced techniques to easily break down traditional password based security systems. The following are examples of industries that are particularly susceptible to suffering financial losses due to data security problems:
- Healthcare: Thehealthcare industry is perhaps the most vulnerable to data security breaches because black market demand for health records is high. The Ponemon Institute, a research center that examines data protections, recently reported that data breaches cost the healthcare industry up to $5.6 billion a year.
- Banking/Financial Services: Banks and other financial institutions are attractive targets for data security breaches mostly because existing external and internal data security protocols are weak and identity management systems are antiquated and easily exploitable. In a recent survey of 75 banks and credit unions results found that losses due to data security breaches reached more than $2 million.
- Government: As reported by the GAO, government data breaches in recent months are at an all-time high. The government/military ranked third on the data breach list in the U.S., accounting for 11.1% of the overall breaches and 14.3% of the compromised records, according to an Identity Theft Resource Center Report.
- Business Enterprises: A recentreport by Identity Theft Resource Center shows that the business sector has been victimized by 32.9% of the total breaches this year in the U.S., representing nearly 60% of the compromised records.
How Can Biometric SSO Increase Data Security?
Most recent data security breaches were the result of employee passwords being compromised and unencrypted file sharing. Using a biometric SSO solution can prevent unethical employees from repudiating responsibility for their actions by claiming an imposter had logged on using their authentication credentials when they were not present. Using a biometric SSO system for sensitive file encryption is the most effective strategy to avoid these situations because when traditional passwords are compromised, strong encryption cannot even offer protection from data breaches.
Therefore, stealing, sharing, or swapping passwords by employees can cause devastating data security breaches as we have seen in the past few years and the problem is getting worse every day. The number one leading cause of data security breaches resulted from employee error (39%). The Ponemon Institute concludes that these breaches are typically the consequence of complacency or negligence from lax or insufficient access control to sensitive or confidential data. Implementing a single sign-on (SSO) biometric solution can solve these problems easily and in a convenient way.
The Advantages of Using Biometric SSO for Data Security
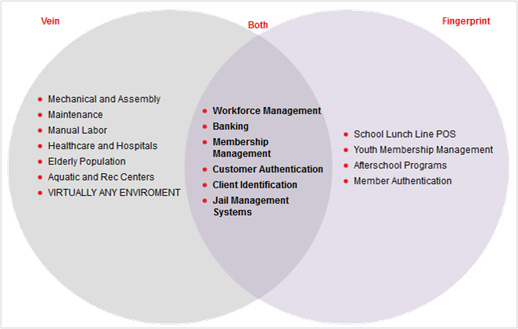
|
| Suitable Usage of biometrics in different industries |
The advantages of using biometric SSO for securing enterprise information are huge. The main advantage of using biometric authentication instead of traditional passwords or physical tokens is that biometrics cannot be easily lost, stolen, duplicated or compromised. A biometric SSO system also reduces employee password reset requests which can be a financial and productivity drain on IT staff help desks. Here are some major advantages of using a biometric SSO solution for any kind of organization:
- Strong Authentication: Using biometric SSO authentication provides stronger authentication instead of relying on traditional passwords. It is virtually impossible to steal or duplicate biometric characteristics for authentication purposes.
- Anti-Spoofing Capabilities: Each human biometric characteristic is unique, and every individual has different physiological characteristics such as fingerprints, finger vein patterns, palm vein patterns, iris patterns, etc. Therefore, all of these modalities are hard to forge, copy, or spoof. Some biometric identification management experts even suggest the use two-factor biometric authentication because single modal biometric systems have a higher risk of spoofing attacks. Moreover, biometric technology is now more advanced and there are new affordable multi modal biometrics devices that can capture both fingerprint and finger vein mages in one single scan, relying on the presence of blood flow via the vascular biometric modality for liveness detection and anti-spoofing capabilities.
- Higher Identification Accuracy: Biometric characteristics are unique for every person in the world, even identical twins have different biometrics. Biometric SSO provides the highest level of identification accuracy and helps to prevent duplicate identities.
- High level of Security: Biometrics has been considered the highest level of authentication security measure for many years in industries such as law enforcement, military, and the government using Automated Fingerprint Identification System (AFIS) software. As the industry has evolved, biometrics are more sophisticated and available for commercial use in many different ways such as biometric SSO which has strong potential for organizations to protect data from being compromised.
- Strong Data Encryption: Data encryption in many organizations does not always protect information, especially when traditional password security protections are weak. Implementing biometric SSO for data encryption can provide strong encryption protection.
- User Friendly and Ease of Management: The user-friendly nature of biometric authentication solution automation provides peace of mind to IT departments of any organization.
- Cost Effective: Implementing a fingerprint single sign on solution in small to big organizations reduces financial losses from being compromised by weak password management policies. Plus, the variety of biometric SSO modalities available brings flexibility to organizations who may be using fingerprints but would be better suited to use vascular biometrics such as finger vein or palm vein to achieve better return on investment (ROI)
Implementing a biometric SSO solution with convenient integration into Active Directory bolsters password management security and leaves IT departments in complete control. Biometric SSO solutions can save the cost many organizations face from government regulations, fines, and penalties on data security each year. Biometric SSO solutions can also save financial losses resulting from data security breaches. It is now essential for organizations to focus on unique end-user sign-on challenges and deploy strong authentication and accurate identity management initiatives.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!



