Three Tips for Securing the Open Enterprise
 The days of wrapping our enterprise users and systems within a network security perimeter are long gone. In order to better innovate and compete in today’s fast moving markets, the business needs to leverage any opportunity to accelerate new initiatives and create new revenue opportunities. For example, the business brings in SaaS applications to meet their needs if IT can’t deliver services fast enough; it adopts new mobile apps to support employee and customer engagement; it packages its own intellectual property in the form of APIs for growth and agility; and it sets up internal system access for partners and contractors for streamlined operations. This essentially opens the enterprise and creates a challenge for the security team: How to enable and still protect the Open Enterprise.
The days of wrapping our enterprise users and systems within a network security perimeter are long gone. In order to better innovate and compete in today’s fast moving markets, the business needs to leverage any opportunity to accelerate new initiatives and create new revenue opportunities. For example, the business brings in SaaS applications to meet their needs if IT can’t deliver services fast enough; it adopts new mobile apps to support employee and customer engagement; it packages its own intellectual property in the form of APIs for growth and agility; and it sets up internal system access for partners and contractors for streamlined operations. This essentially opens the enterprise and creates a challenge for the security team: How to enable and still protect the Open Enterprise.
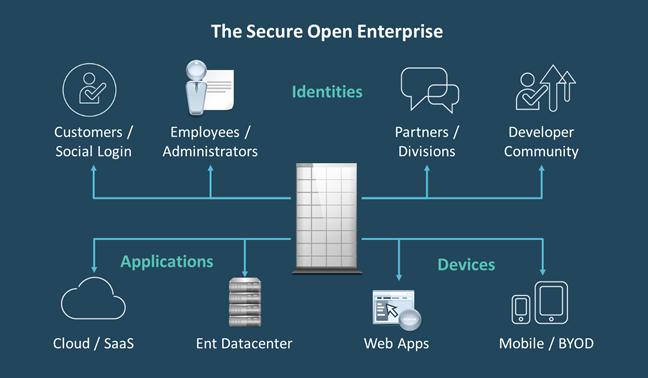
Because we are expanding on three dimensions at the same time, enabling the secure Open Enterprise presents several challenges: 1) The identity population needing access to enterprise data is moving beyond employees and administrators to include business partners, contract developers and a rapidly growing customer community; 2) At the same time, the applications those groups need access to are migrating from the enterprise data center to the cloud and; 3) The access device is evolving from PC to smartphone and tablet but will quickly include other smart devices such as wearables and smart meters. While opening the enterprise increases the attack surface, securely enabling the open business can help it innovate and grow.
The first step to securing the Open Enterprise is managing identity. According to the Verizon data breach report, the use of stolen or misused passwords continues to be the number one way to gain access to information. With fragmented IT systems, identity is the new security perimeter. Authentication of identities should be centralized to all resources, whether on premise or not. This offers a single point of control and an audit point. You can then apply multi-factor authentication options to reduce the threat of compromise from weak or leaked passwords. By federating access from your identity broker, multi-factor authentication is applied to applications that don’t otherwise support it. Over time, the business can add more sophisticated authentication elements bringing in context (device type, network type, geo-location, etc.) and analytics. In this model, disabling users now means they have no access to any external SaaS applications, a big win for securing corporate IP.
Next, the Open Enterprise needs to share information. The days of building a web app are quickly passing. The business needs API level access to information to share across divisions and with partners. In fact, instead of IT building a mobile app for the business, give the business a set of APIs to build their own mobile apps. By implementing an API gateway to your applications and data, you can create strong security controls while the business innovates and experiments with new apps. The business can even open these information feeds directly to partners to include in their applications.
The final, key component of the Open Enterprise architecture is managing developer access to APIs and providing business owners insight to usage. Once applications and data are available in a secure, accessible model, the business will quickly find new revenue models and want to scale. The Developer Portal will allow a large number of developers inside or outside the organization to request access to a set of APIs, obtain access keys, review sample code, test integration and begin developing in a self-serve model. This component will also let application or business owners get reports on which applications and which business partners are driving traffic.
A great example of this in action is the New York MTA. Its business team thought it could increase ridership if the schedules were easier to access. Rather than trying to create the one perfect app, the IT team focused on securely exposing API access to the scheduling systems and allowing developers to focus on what they do best. Within three months, there were dozens of mobile apps that incorporated MTA scheduling information in a way that works best for their consumer. The security team had complete visibility to log and monitor each transaction.
It is well understood that the threats to corporate intellectual property continue to grow. The Open Enterprise further increases the attack surface. By centrally controlling identity and abstracting security controls to the API gateway, the business can securely enable the open enterprise and manage the risk. In fact, the new architecture helps the business move faster, innovate and experiment with programs that drive revenue. Using these three tips to secure the Open Enterprise shows business leaders that the security team supports and is in alignment with business goals. Who knows, additional budget and resources may surface as security becomes an enabler of the business.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







