Getting the Word Out

Speakers were part of the Inauguration security in case messages needed to be broadcast to attendees. Photo courtesy of Federal Signal
Whether it’s a crime incident or a tornado, an electrical crash or even a special sale on concert tickets, getting the word out to a community of employees, students or city residents is now easier thanks to mass notification systems.
They incorporate a variety of response mechanisms to allow enterprises and institutions to improve communications often in the event of an emergency. But the systems can improve the business processes of major corporations and even create an income stream for colleges and cities.
The best definition of mass notification is a means to notify occupants of a building or area in a real-time setting. A primary command center broadcasts live or pre-recorded emergency voice and data messages and/or instructions. The overall aim is to get accurate and useful information out to people who need it. The trick is to use enough types of means of communication to get the word out to most everyone. There are systems that work with existing fire alarm systems and emergency telephone systems. Others play off of cellular telephones, instant messaging and smartphones as well as audio broadcast, strobes, computer displays and even LED-enabled billboards.
They incorporate a variety of response mechanisms to allow enterprises and institutions to improve communications often in the event of an emergency. But the systems can improve the business processes of major corporations and even create an income stream for colleges and cities.
The best definition of mass notification is a means to notify occupants of a building or area in a real-time setting. A primary command center broadcasts live or pre-recorded emergency voice and data messages and/or instructions. The overall aim is to get accurate and useful information out to people who need it. The trick is to use enough types of means of communication to get the word out to most everyone. There are systems that work with existing fire alarm systems and emergency telephone systems. Others play off of cellular telephones, instant messaging and smartphones as well as audio broadcast, strobes, computer displays and even LED-enabled billboards.
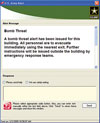
Notices can be delivered through networked desktop and laptop computers with ways to note receipt and action taken.
TOO DEPENDENT ON MASS MEDIA
According to research by CDW-Government, there still is a disconnect between companies, schools and government agencies and their ways of getting the word out. Many still depend on broadcast media. But media consumption habits are changing: Americans watch less TV, are more mobile and, especially within younger demographics, are increasingly reliant on cell phones and text messaging. Most governments and companies have not kept pace with these developments, which can keep people safe in emergencies. City, state and local governments primarily rely on television and radio to communicate emergency information to the public, according to the CDW-Government study. Both require citizens to have access to electricity and actively “tune in.” In an emergency, people need to be notified quickly so they know either to take shelter at their current location or move to a safe location. Time is usually of the essence.
So enterprises are turning to newer ways.
UCLA created its campus-wide emergency mass notification system, known as “BruinAlert,” based on AtHoc software. With this deployment of the network-centric emergency notification solution, UCLA became one of the first major American universities to deploy an effective mass notification system that fully unified all campus communications resources. The implementation of its network-centric emergency notification system came about as the result of a comprehensive needs gathering and system evaluation process.
More than 60,000 students and staff engage in a variety of activities on the UCLA campus. To protect them, UCLA’s emergency notification capabilities had evolved to incorporate new technologies. As a result, the university developed a comprehensive set of separate alerting systems, including bulk e-mail, AM radio, a cable television station and a Web site. However, no single method of alerting could guarantee contact with everyone during an emergency. That was the reason behind UCLA’s desire to use multiple forms of alerting that could be triggered through a single system.
Such systems also need testing.
Just last month, the University of Houston Department of Public Safety tested its mass notification voice and siren system. The siren sounded for 30 seconds, followed by a brief voice message. The university plans to use the system in the event of emergencies such as severe weather conditions, active shooter or other terrorism incidents and major hazardous material incidents.
So enterprises are turning to newer ways.
UCLA created its campus-wide emergency mass notification system, known as “BruinAlert,” based on AtHoc software. With this deployment of the network-centric emergency notification solution, UCLA became one of the first major American universities to deploy an effective mass notification system that fully unified all campus communications resources. The implementation of its network-centric emergency notification system came about as the result of a comprehensive needs gathering and system evaluation process.
More than 60,000 students and staff engage in a variety of activities on the UCLA campus. To protect them, UCLA’s emergency notification capabilities had evolved to incorporate new technologies. As a result, the university developed a comprehensive set of separate alerting systems, including bulk e-mail, AM radio, a cable television station and a Web site. However, no single method of alerting could guarantee contact with everyone during an emergency. That was the reason behind UCLA’s desire to use multiple forms of alerting that could be triggered through a single system.
Such systems also need testing.
Just last month, the University of Houston Department of Public Safety tested its mass notification voice and siren system. The siren sounded for 30 seconds, followed by a brief voice message. The university plans to use the system in the event of emergencies such as severe weather conditions, active shooter or other terrorism incidents and major hazardous material incidents.
BEYOND THE PHONE TREES
In another example, although emergency communications has always been a primary concern of Longwood University, the university was unable to communicate to the campus community quickly and efficiently in an emergency.
Like many colleges, Longwood relied on contact phone trees for internal communications and media outlets for external communications. There were no means to notify students who were outdoors or off-campus within seconds of a disaster or if there was a power outage. “The events at Virginia Tech and other schools across the country have demonstrated the necessity to create redundant effective systems that provide information among many pathways,” said Longwood’s Dan Dillon.
So he brought in Cooper Notification’s mass notification system, which includes outdoor warning systems, emergency text messaging and e-mail alerts, enables officials to alert the campus community in real-time during times of extreme circumstances such as a tornado or police emergency, and offers the best protection for the entire campus. There are six high power speaker arrays at highly populated on- and off-campus locations for exterior voice alerting. In an emergency, they broadcast a siren alert, followed by a live or recorded voice message tailored to the situation. The intrusive system has the capability of alerting the entire campus or individual areas depending on the scope of the emergency.
On a tight economy, organizations also see ways to generate revenue from mass notification. Especially at educational institutions, some have established notification systems that allow opt-in for messages that are not necessarily for emergencies. The information may center on campus events, sales pitches and paid advertising.
More recently, corporations, government agencies and the military have sought for notification tools to send out messages over networked desktop and laptop computers.
One example, also from Cooper Notification, is technology which turns computer desktops into emergency notification devices. When critical information must be communicated, it allows authorized administrators to send audio and visual pop-up notifications within seconds to all recipients or targeted groups who are logged onto the network. It enables organizations to customize their desktop pop-up screens and provide links to access maps, evacuation routes and additional emergency information as well as two-way communications for delivery confirmation and user response,
Compounding matters is the fact that no industry standard governing mass notification systems exists. The only exception in this standard-free environment is the U.S. Department of Defense (DoD) guidelines written to address mass notification on military bases.
Like many colleges, Longwood relied on contact phone trees for internal communications and media outlets for external communications. There were no means to notify students who were outdoors or off-campus within seconds of a disaster or if there was a power outage. “The events at Virginia Tech and other schools across the country have demonstrated the necessity to create redundant effective systems that provide information among many pathways,” said Longwood’s Dan Dillon.
So he brought in Cooper Notification’s mass notification system, which includes outdoor warning systems, emergency text messaging and e-mail alerts, enables officials to alert the campus community in real-time during times of extreme circumstances such as a tornado or police emergency, and offers the best protection for the entire campus. There are six high power speaker arrays at highly populated on- and off-campus locations for exterior voice alerting. In an emergency, they broadcast a siren alert, followed by a live or recorded voice message tailored to the situation. The intrusive system has the capability of alerting the entire campus or individual areas depending on the scope of the emergency.
On a tight economy, organizations also see ways to generate revenue from mass notification. Especially at educational institutions, some have established notification systems that allow opt-in for messages that are not necessarily for emergencies. The information may center on campus events, sales pitches and paid advertising.
More recently, corporations, government agencies and the military have sought for notification tools to send out messages over networked desktop and laptop computers.
One example, also from Cooper Notification, is technology which turns computer desktops into emergency notification devices. When critical information must be communicated, it allows authorized administrators to send audio and visual pop-up notifications within seconds to all recipients or targeted groups who are logged onto the network. It enables organizations to customize their desktop pop-up screens and provide links to access maps, evacuation routes and additional emergency information as well as two-way communications for delivery confirmation and user response,
Compounding matters is the fact that no industry standard governing mass notification systems exists. The only exception in this standard-free environment is the U.S. Department of Defense (DoD) guidelines written to address mass notification on military bases.
PART OF LIFE SAFETY SYSTEMS
A combination fire alarm/mass notification system is declared to be “the simplest and most economical approach” for U.S. military bases and other DoD properties. The 2010 edition of NFPA 72: National Fire Alarm Code is expected to replicate the specifications for private sector applications.
Most commercial buildings already encompass a fire alarm system that is required by code to be tested and maintained on a regular basis. Today’s high-tech fire alarms are supervised systems, constructed to be more “survivable,” which enables them to continue functioning properly even when one or more parts are damaged. Stringent codes applied to these systems also dictate a high-level of intelligibility to ensure live voice and pre-recorded messages can be clearly understood. The same intelligibility conditions apply to the phone communications provided between components of a combo fire alarm/MNS for security and first responders to use as a means for communicating during an emergency. One example, Gamewell-FCI has a line for both new construction and renovation applications.
Another approach that has a leg up is through emergency telephone systems, which traditionally have been installed in colleges, hospitals, airport parking lots and garages. From sources such as Talk-A-Phone and Code Blue, existing equipment can be transformed to emergency broadcasting systems for maximum audio clarity and range.
Whether at a college or university, a corporate campus, military base, utility plant, airport, shipping complex or any other multi-building setting, IP or network-capable mass notification systems can provide solutions in tying together indoor and outdoor areas. In most cases, IP infrastructure already exists. Wide-area paging, for instance, can link together buildings and outdoor parking lots and play grounds. That can be accomplished wirelessly or by installing additional cable runs to outdoor areas.
Most commercial buildings already encompass a fire alarm system that is required by code to be tested and maintained on a regular basis. Today’s high-tech fire alarms are supervised systems, constructed to be more “survivable,” which enables them to continue functioning properly even when one or more parts are damaged. Stringent codes applied to these systems also dictate a high-level of intelligibility to ensure live voice and pre-recorded messages can be clearly understood. The same intelligibility conditions apply to the phone communications provided between components of a combo fire alarm/MNS for security and first responders to use as a means for communicating during an emergency. One example, Gamewell-FCI has a line for both new construction and renovation applications.
Another approach that has a leg up is through emergency telephone systems, which traditionally have been installed in colleges, hospitals, airport parking lots and garages. From sources such as Talk-A-Phone and Code Blue, existing equipment can be transformed to emergency broadcasting systems for maximum audio clarity and range.
Whether at a college or university, a corporate campus, military base, utility plant, airport, shipping complex or any other multi-building setting, IP or network-capable mass notification systems can provide solutions in tying together indoor and outdoor areas. In most cases, IP infrastructure already exists. Wide-area paging, for instance, can link together buildings and outdoor parking lots and play grounds. That can be accomplished wirelessly or by installing additional cable runs to outdoor areas.
INTEGRATED EMERGENCY PHONES
For instance, Talk-A-Phone’s wide-area emergency broadcast system has IP and analog options that can also integrate with other devices on the network, including wall-mounts, indoor and outdoor paging units, blue-light strobes and security video cameras.
The advantage of an IP-based mass notification system is that it can integrate text, e-mail, instant messaging, telephone, PDA, fax machines, TYY for the hearing impaired and satellite-based communications.
The advantage of an IP-based mass notification system is that it can integrate text, e-mail, instant messaging, telephone, PDA, fax machines, TYY for the hearing impaired and satellite-based communications.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





