Approaching a Market Size for PSIM
Physical security information management, PSIM, is one of the most talked about and sometimes controversial topics in the security industry today. Is it a technology? Is it a marketing category? What is it? What does it do? Is there any money in it? I looked into it and came up with a clear understanding about what security executives want from PSIM and how much they are ready to spend.
First of all, here is my definition of PSIM. I call it software designed to aggregate, normalize, correlate, apply policy to and display diverse data as information to simplify and improve physical security incident response. Basically, it is a better, more flexible and much more useful way of managing security events and the information needed to respond to incidents than traditional command center solutions.
There’s Gold in Them There Hills
PSIM software solutions will earn $3 billion to $4 billion annually by 2012. Public and private organizations, large and small, are already assuming a growing trend in spending for PSIM solutions. The PSIM market is enjoying a convergence of trends that enhance its potential, namely: the continued adoption of computers, software and networking to perform business functions; lowering costs of networking sensors and systems globally; innovations in software for collecting, analyzing and responding to incidents.Finding the Numbers
A top-down estimation of the potential PSIM spending would normally take total security spending and parse it out based on certain assumptions. For example, of the say $50 billion annually spent on security products and installation services, only a portion would be spent in organizations considered candidates for PSIM solutions, like corporate facilities, airports and the like. Further percentages would be peeled away, assuming the adoption lifecycle of PSIM-like technologies in those environments (long sales cycles, integrator reluctance, etc).That sort of estimation could very reasonably find $1 billion to $5 billion or more of expected spending on PSIM products over the next few years. One magazine published a quote by a vendor claiming $10 billion by 2012.
That felt a little extreme, so my team and I decided to take a bottom up approach.
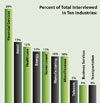
The Hunt Business Intelligence team and I sampled interviews we had previously conducted with 211 individuals in North America representing ten industries. See the accompanying chart.
Nearly half of the respondents work for organizations with annual revenues exceeding $3 billion. Roughly one-quarter represents organizations in the mid-market, with revenues in the range of $100 million to greater than $1 billion. Respondents held influential positions in corporate (physical) security, IT security, IT operations and compliance with the following titles (or equivalent):
- Chief information officer
- Chief information security officer
- Chief network architect
- Chief security officer
- Chief technology officer
- Director of infrastructure
- Enterprise architect
- Security director (corporate/physical)
- Vice president of operations
Top Spending Amounts
But this was not sufficient for us, of course. That told us the bottom of the spending range, but what is the top? How many of those $1 billion+ organizations will spend $100,000 or even a million dollars by 2012? To determine that, end-user executives in 15 more companies were interviewed, who described scenarios where PSIM solutions could produce value. For example, we described specific uses of technology to handle situations involving three or more data types in corporate, transit and government environments.The reaction was enthusiastic and indicated the prospect of three to five times current expected spending (that sudden increase was due to what we call the “aha!” factor). Once a person knows that a more efficient or effective solution exists, the budget will appear. It may take one to three years for the budget to go thru full internal adoption processes, but it is clear that there is interest in PSIM.
Therefore, among large organizations of $1 billion annual revenue or larger, we can safely assume $1-2 billion annual spending by 2012. Add smaller organizations and local governments which may be classified as smaller than a usual $1 billion company, and the total spend could be much higher. For every Global 3000 candidate able to spend
$100,000 or more, there will likely be three or four candidates in the much more populous mid-sized corporate or government categories spending $50,000 or more, effectively doubling the total spend of the large organizations.
With approximately $3 billion as our working assumption, I think it is fair to assume that special contracts to government, military or special events (e.g. Olympics) can safely add half a billion dollars in additional spending in any year.
Alternative View
While the estimates mentioned above may be based in sound reasoning, they are only estimates and do not fully take into account variables such as lack of vendor presence in certain geographies (like Asia), poor execution by vendors, or fluctuations in the dollar.So far, this estimation is only substantiated by interviews in North America and greater Europe; Middle Eastern, Asia Pacific and southern hemisphere markets will constitute additional spending, of course, but we have little date to support an estimate. However, many technology companies, after establishing sales and marketing presence in Asia Pacific, achieve sales figures equal to those in North America. If PSIM vendors become effective selling in Asia, potential revenues could be considerably higher.
So there you have it. PSIM is here to stay and security executives are already planning to spend money on it this year and for years to come.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





