Attack of the Foreign Botnets
Botnet attacks, often from sophisticated offshore locations, can bring down enterprise applications including integrated physical security systems working on enterprise networks.
Among the most serious threats facing the Internet today are Distributed Denial of Service (DDoS) attacks in which compromised PCs controlled by remote attackers inundate a network with the intent to crash its Web or application services. Worldwide DDoS attacks reached as many as 10,000 per day in 2006, according to a survey conducted by the Computer Security Institute.
These attacks are very easy to launch and hard to track. Furthermore, it is difficult to deny the requests of attackers without also refusing legitimate requests for service. Up to now, conventional DDoS prevention included mitigation leveraged routers, firewalls and intrusion detection systems and more recently new plug-and-play DDoS mitigation devices. But these solutions have limitations particularly in light of the size of the attacks.
CHECK WITH YOUR NET ADMINISTRATOR
Organizations can purchase these solutions themselves, and many Internet service providers offer the devices on their networks. DDoS mitigation devices employ newer intrusion prevention technology that not only inspect traffic, but also proactively mitigate attacks based on rules established by the network administrator. For example, an intrusion prevention system might drop a packet that it determines to be malicious and block all further traffic from that IP address or port while allowing unaffected traffic to flow unimpeded. Mitigation systems can perform complex monitoring and analysis, such as watching and responding to both individual packets and overall traffic patterns.Unfortunately, these hardware devices also have performance limitations. After they reach their limits, they allow “attack leakage” back onto the system, hurting the network. Modifying these solutions to add capacity is a slow process that can take days to weeks – far slower than the rate at which attack sizes are increasing.
In the end, the most effective prevention against DDoS attacks is to make sure they never enter a network in the first place. Increasingly many organizations are turning to service providers that mitigate massive DDoS attacks “in the cloud,” leveraging large amounts of bandwidth and racks of “scrubbing equipment.” Managed service providers spread the cost of their resources over many customers, so they can purchase massive amounts of resources to handle the largest attacks.
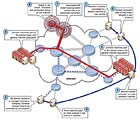
The most effective DDoS mitigation service providers have global reach, and so are able to mitigate attacks near their origin.
It is increasingly common that US- and European-based companies are attacked by large botnets stemming from Asia. So it makes little sense to have gigabits of traffic travel over continents and oceans en route to a single DDoS mitigation system.
About the Source
Security Magazine thanks Paul Sop, chief technology officer at Prolexic Technologies, for the material in this article. During his career, Sop also founded a company focused on insider threat simulation. Contact him at paulsop@prolexic.com.Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





