Solutions: Laptops. Privacy. ID Theft. Try Online Backup
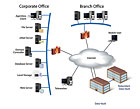
There is local and offsite online backup for corporate and branch offices.
In today’s around-the-clock business environment, critical data is growing at an explosive rate. Protecting this information is a crucial business need. So chief security officers (CSO) need immediate and constant access to important information to ensure business continuity when disasters happen.
At the same time, a growing number of incidents point to the vulnerability of laptops offsite, as enterprises crack down on placing sensitive data on laptops that travel with executives.
That is why more and more companies each day are considering and ultimately switching to online data backup.
Here’s how it works. The first step with online backup is for the service provider to supply the company with software to be installed on the PC or server that needs to be protected. The software will enable the user to hand-select the files, databases or email to be backed up. Once the software is installed, the user will be asked to establish a backup schedule, which can occur as frequently as the user needs.
Next, the data is compressed, encrypted and sent offsite. After the initial backup the subsequent backups will be reviewed for changes since the last backup and only the changes will be sent offsite. Once uploaded to the service provider’s data center, the data is available to be restored 24 hours a day, seven days a week.
Now, let’s review some of the benefits and limitations of online data backup. First, the advantages:
- Online backup relies on an automated process that does not require human intervention. Backup status is provided to the customer by e-mail after every scheduled backup, making the process easily monitored.
- Data is stored securely off-site. In case of any emergency, disaster or fire at the business location, all data is safely stored off the premises.
- Set-up and installation can be quick and simple. Many times installation can be done remotely and completed just with a simple phone call.
- Backup and data recovery can be simpler and faster than more traditional methods, such as tape. Just a couple clicks and your backup or restore is underway.
- Online backup allows the user to centrally manage data protection for remote office locations.
- There are no upfront costs to get started. No purchase of hardware or software is required.
- Online backup provides the user with the ability to back-up and restore multiple versions of files. This can be useful if earlier versions of a document need to be retrieved.
- Upgrades are made frequently and, for the customer, effortlessly. Using an online backup provider means that product improvements are free and conducted regularly.
- Online backup is available to all size companies – big and small – which helps the small and medium-sized businesses compete in a global market, giving them access to resources that have traditionally only been available only to larger enterprise companies.

Lost laptops with sensitive business information have grabbed headlines and CEO headaches. More CSOs are opting to add biometrics for laptop access and also move data to online backup, just in case.
Benefits and disadvantages
The rapid increase in businesses adopting online data backup is an indication that the benefits have been outweighing the disadvantages. However, it is important to be aware of some potential pitfalls:- Internet speed and availability can be an influencing factor in reviewing online backup service for a company. The duration of backups and restores will be limited by the speed of the Internet connection. Therefore, if an internet connection is unavailable, it may not be possible to perform a backup or restore. To avoid this from happening to you, be sure that your online backup provider is able to save a copy of the backup on your Local Area Network (LAN) as well as offsite. In the event that the company needs to perform an emergency restore and the internet connection is unavailable or the amount of data is extremely large, it is important to have a copy of the backup on the network. Many online backup providers also have the ability to return data on CD, DVD or USB in the event of a disaster.
- Relying on an external company to protect your critical business data can be seen as a risk. That is why it is important to meet with the service provider, ask to tour their data center, and do some research. Some businesses have chosen to store unencrypted backup tapes with an offsite storage company and we have heard many stories of these tapes being lost and the location of unsecured data is unknown. With online backup, this risk is eliminated by ensuring that data is encrypted and only the user holds the key to decrypt the data.
- The cost can be a potential disadvantage if the service provider is not chosen wisely. Most service providers charge on a monthly basis for online backup. One factor to consider is that you will get the best deal if you only pay for the data you are storing offsite. Avoid paying for pricing plans that require you to pay for pricing commitment where you pay for storage space not used. Also, some online backup providers charge for uncompressed data -- be sure that your service provider charges only for compressed data.
If you decide that you would like to pursue online data backup for your company, below are seven simple – but critical -- questions to ask the potential service provider:
- Can I obtain customer references from companies with similar requirements?
- Is free customer support available 24 hours a day, seven days a week?
- Is the backup of mail servers and open databases included? (Don’t be misled -- some companies require the purchase of additional software for protecting this type of data.)
- Will my data be encrypted during transfer and while stored on remote servers?
- Can we have a copy of your Service Level Agreement (SLA)? The absence of a guarantee on uptime should be an element considered when reviewing online backup providers.
- Will my data be stored in a secure data center?
- Does the service provider have a second data center where the data is protected?
Online backup can be an excellent way to augment your existing backup solution or can serve as a complete replacement to traditional backups. Be educated about the pros and cons, and follow this advice to determine a solution that best suits your company’s needs.
Human error, disasters, file corruption, and hardware failure can and do happen – more often than we’d like to admit. A little planning today can go a long way to ensure the safety of your business tomorrow.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






