Zalud Report: In the Palm of Your Hand

Enterprises big and small share goals when it comes to security. When it makes business sense, they want to leverage what exists; speed up the delivery of more accurate information to the appropriate decision maker; improve a process that’s essential to the organization; piggyback one solution to help solve sometimes unrelated others; and save time or money or both.
Daniel Gohl, principal at McKinley Technology High School in Washington, D.C., knows better than some boardroom-oriented CEOs that – when there’s an incident – wasted time can cause exponential harm.
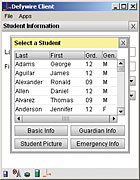
Middleware can access a database, display student names and document an incident – all in a uniform and fast way.
Leverage existing tech
Gohl’s assignment: Leverage the school’s existing technology to improve student services by increasing his faculty’s access to student information such as emergency contacts and medical records as well as grades and schedules.His solution was in the hands of his staff – WiFi-enabled PDAs. Mobility was the overriding key. Before the improvements, “We were able to access student information only on desktop systems, which isn’t helpful to school personnel monitoring school grounds.”
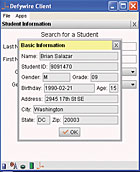
More security executives, often working more closely with their IT colleagues, are also bringing in middleware or what some call enabling technology to bridge existing computer and communications infrastructure to do better or more or faster or all of these outcomes. Middleware comes from sources not usually found in the traditional security market or are brought into a design thanks to a systems integrator.
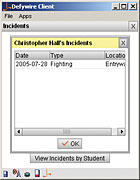
The charm of middleware
For McKinley’s Gohl, “Now we have an application (Mobile Guardian from Defywire, Herndon, Va.) that roams wherever our personnel and students are. This has greatly enhanced our ability to secure the school and significantly cuts down on staff hours spent completing paperwork associated with disciplinary incidents.”The real-time nature of such incident reporting applications creates accurate, uniform and instantaneous documentation of incidents. To me, it also sounds like guard tour systems on steroids.
And just like those early guard tour systems, Gohl aims to expand uses for his mobile devices. His future plans include adding teachers to the user base and using sophisticated wireless technology to evaluate teachers and provide instant feedback at the end of the class.
SIDEBAR: My Twist on Security Happenings
It’s Zalud’s Blog. You can access it at http://blog.securitymag.com or through Security Magazine’s Web site at www.securitymagazine.com. Every day – including weekends – I post items of specific interest to you. Some you can’t see anywhere else. The blog also allows you to comment on items so your colleagues can gain from your insights.Links
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





