Bless this Union

Millions of dollars are lost each year due to stolen or damaged physical assets or the unavailability of mission-critical systems. The convergence of physical and IT security is a well-accepted trend that has already taken root in many organizations. But a less-noticed trend that is also gaining traction is building automation controls systems integrators providing integrated physical security (HVAC and security integrated on one console).

Trends converge
Two complimentary convergence trends are influencing the adoption rate and preferred suppliers as physical and IT security converge:An end user convergence that includes the security decision maker(s), the facilities decision maker(s) and the IT decision maker(s) collectively making the decisions and acting interdependently.
A supplier convergence that includes security functionality, building automation controls (HVAC) and integration with IT network management systems being integrated from one supplier.
Some independent building automation controls manufacturers are sourcing IP-based access control, video surveillance and environmental monitoring solutions to their independent systems integrators today. Independent controls manufacturers and suppliers must offer security functionality to compete with the larger industry giants that have acquired security companies to offer a one-stop shop solution.
Building automation controls system integrators are better positioned today to be the premier and preferred supplier of integrated security and HVAC solutions to support physical and IT security convergence. The building automation controls manufacturers and controls systems integrators have a distinct advantage over the security dealers and the combined controls/security industry giants:
No internally owned legacy and/or proprietary products to hamper their solutions.
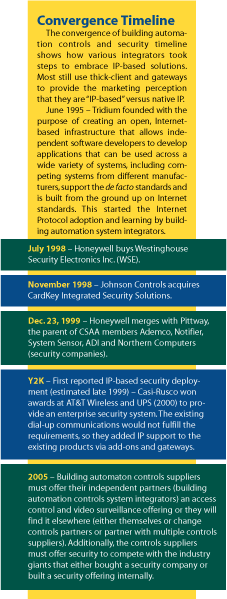
They embraced native IP-based technology as early as 1999, while the first security deployments of IP-based systems used grafted-on-thick clients and gateways to offer an IP-based enterprise security solution.
They have learned security and offer native IP-based security.
Offerings already integrated with their HVAC solutions – for example: one integrated console for security and HVAC that can interoperate with an IT console.
Local incumbents offering a level of personal and on-the-premises services that build trusted relationships.
?Business requirement to integrate access control to support energy management application.
Security dealers are not in a position to learn HVAC and offer integrated solutions.
IT departments are not in a position to learn physical security because of workload and a lack of standards in the physical security space.

Assertions
It is widely acknowledged that convergence between physical security and IT security (cyber security) is happening, albeit at a slow rate. This is a convergence of services at the end-user level. This does not necessarily mean that IT will run or absorb physical security.A second convergence has been happening for over five years, and is gaining momentum, at the physical security and building automation controls supplier level. This is a convergence at the supplier level.
Truly open standards, based on thin-client IP browser-based technology, will be required by IT departments as they take an even more active role in the decision-making process to ensure they adequately manage risks, leverage their skills and become accountable for the converged network availability.
How does it happen?
In 2004, 20 percent of respondents to a survey by Agility PR on behalf of Axis Communications (U.K.) Ltd. “found that security buying patterns are changing. More than a quarter (28 percent) believed that the physical security buying decision was not in the hands of the IT director and his senior management as against 20 percent last time.”
The magic question: Who will provide the open, IP-based (designed, not bolt-on) solutions that integrate with the IT network management systems and fulfill the requirements of the security department and the facilities manager?
According to the survey, the ultimate providers will be a combination of:
Large government and IT systems integrators that subcontract to the building automation system integrators for controls and physical security, deployment, support and maintenance – 70 percent probability.
Security systems integrators that offer the same IT-friendly systems for standalone opportunities – 75 percent probability
Industry giants will re-architect their proprietary solutions that use bolt-on, thick clients and/or Lantronix RS-232 to IP converters to an open, IP-based solution that rides the technology cost curve – 30 percent probability.
The Forrester Research report – “Security Convergence Gets Real” – bulleted four areas of cost-cutting convergence.
Consolidate credentials for IT and physical access onto a single card. A smart card can serve as an ID badge for building access and can also store IT credentials like passwords and digital certificates.
Connect the processes for granting and revoking building and IT access. Linking the processes for managing employees’ IT access rights with those for managing their building access will get people productive quicker and will improve security.
Correlate security events across the physical and IT realms. Security event management systems, presently used to monitor and respond to IT-related events, should incorporate events from physical security systems. An alert should trigger if, for example, the VPN signals an employee logging in remotely while the badging system indicates that he is inside the corporate office.
Unify the auditing of physical and IT rights and events. By assessing authentication and authorization processes and controls across IT and physical facilities, organizations will find many opportunities for improved efficiencies and security. For example, Forrester recently performed an audit that showed ways in which one company could streamline processes of employee and visitor badging by integrating existing identity management systems.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




